Answer the question
In order to leave comments, you need to log in
What blocks FTP behind NAT through OpenVpn?
Good afternoon.
I have the following connection scheme:
1. openvpn server (VDS freebsd) ip 10.8.0.1
2. openvpn client 1 (windows XP)
3. openvpn client 2 (ubuntu linux) 10.8.0.2
I need to go via FTP from client 1 (XP) to the client 2 (ubuntu).
From FTP server to client 2 works in both passive and active modes. 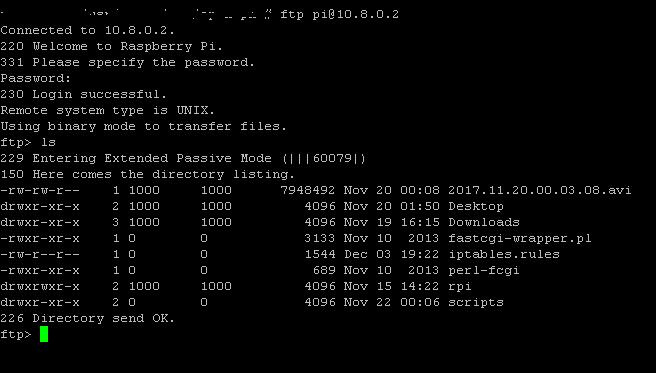
.
.
But client 1 fails to execute the LIST command to get a list of client 2 directories:
Статус: Соединяюсь с 10.8.0.2:21...
Статус: Соединение установлено, ожидание приглашения...
Ответ: 220 Welcome to Raspberry Pi.
Команда: USER pi
Ответ: 331 Please specify the password.
Команда: PASS ******
Ответ: 230 Login successful.
Статус: Сервер не поддерживает символы не ASCII.
Статус: Соединение установлено
Статус: Получение списка каталогов...
Команда: CWD /home/pi/rpi
Ответ: 250 Directory successfully changed.
Команда: PWD
Ответ: 257 "/home/pi/rpi" is the current directory
Команда: TYPE I
Ответ: 200 Switching to Binary mode.
Команда: PASV
Ответ: 227 Entering Passive Mode (10,8,0,2,235,68).
Команда: LIST
Ответ: 150 Here comes the directory listing.
Ошибка: Превышено время ожидания соединения
Ошибка: Не удалось получить список каталоговAnswer the question
In order to leave comments, you need to log in
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question