Answer the question
In order to leave comments, you need to log in
Setting up a VPN between Mikrotik and Zywall?
–î–æ–±—Ä—ã–π –¥–µ–Ω—å, –ø—ã—Ç–∞—é—Å—å –Ω–∞—Å—Ç—Ä–æ–∏—Ç—å IPSec VPN –º–µ–∂–¥—É Mikrotik –∏ Zywall. VPN –ø–æ–¥–Ω—è–ª—Å—è –∞ –ø–∏–Ω–≥–∞ —Å —Å–µ—Ç–∏
Mikrotik –≤ —Å–µ—Ç—å Zywall –Ω–µ—Ç—É, –æ–±—Ä–∞—Ç–Ω–æ –ø–∏–Ω–≥ –µ—Å—Ç—å.
–ú–∞—Ä—à—Ä—É—Ç–∏–∑–∞—Ü–∏—é –Ω–∞ –º–∏–∫—Ä–æ—Ç–∏–∫—É –ø—Ä–æ–ø–∏—Å–∞–ª –∏ –ø–æ—è–≤–∏–ª—Å—è –ø–∏–Ω–≥ —Å Zywall –≤ —Å–µ—Ç—å –º–∏–∫—Ä–æ—Ç–∏–∫–∞.
–û—Ç–∫–ª—é—á–∞–ª firewal –Ω–∞ –∑—É–≤–æ–ª–µ –Ω–µ –ø–æ–º–æ–≥–ª–æ
–í–æ–∑–º–æ–∂–Ω–æ –ø—Ä–æ–±–ª–µ–º–∞ –≤ –º–∞—Ä—à—Ä—É—Ç–∏–∑–∞—Ü–∏–∏, –ø–æ–º–æ–≥–∏—Ç–µ —Ä–∞–∑–æ–±—Ä–∞—Ç—å—Å—è
–ù–∞—Å—Ç—Ä–æ–π–∫–∏ Zywall:
–ª–æ–∫–∞–ª—å–Ω–∞—è —Å–µ—Ç—å - 192.168.1.0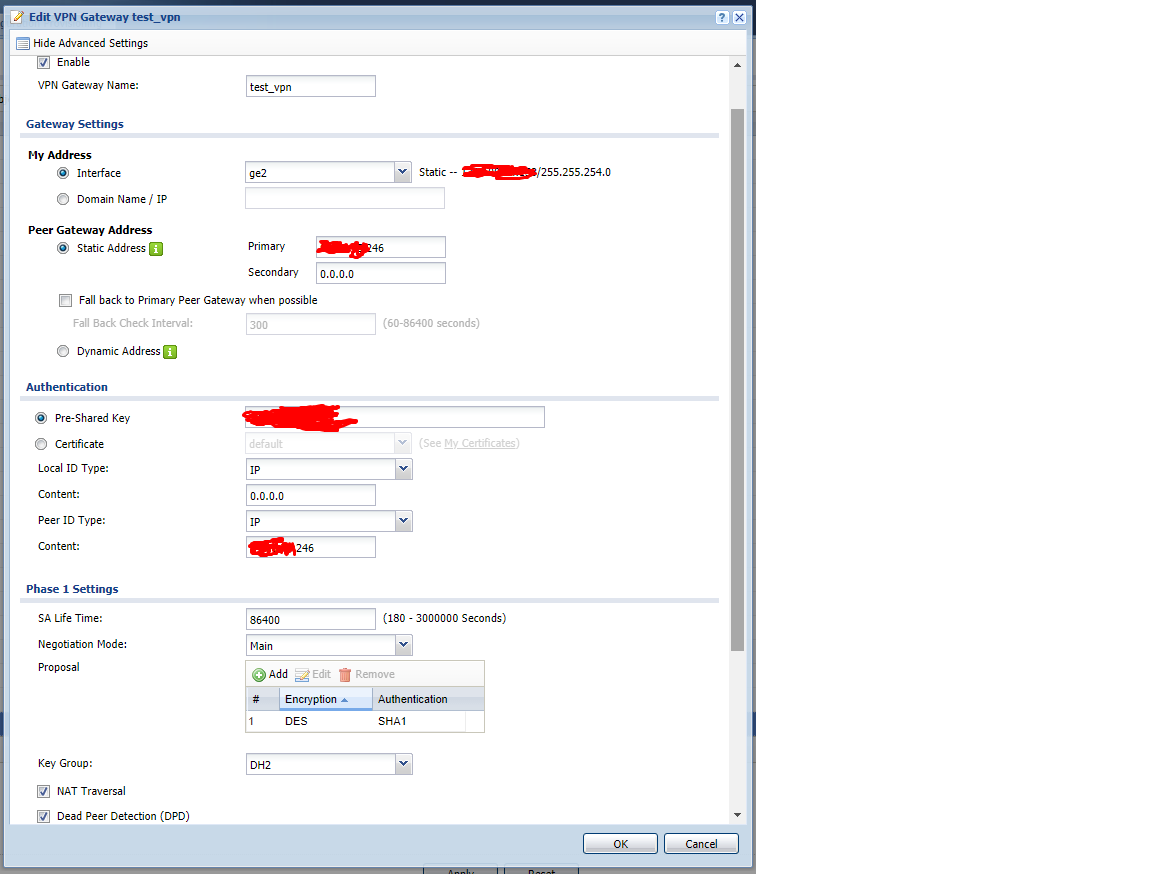
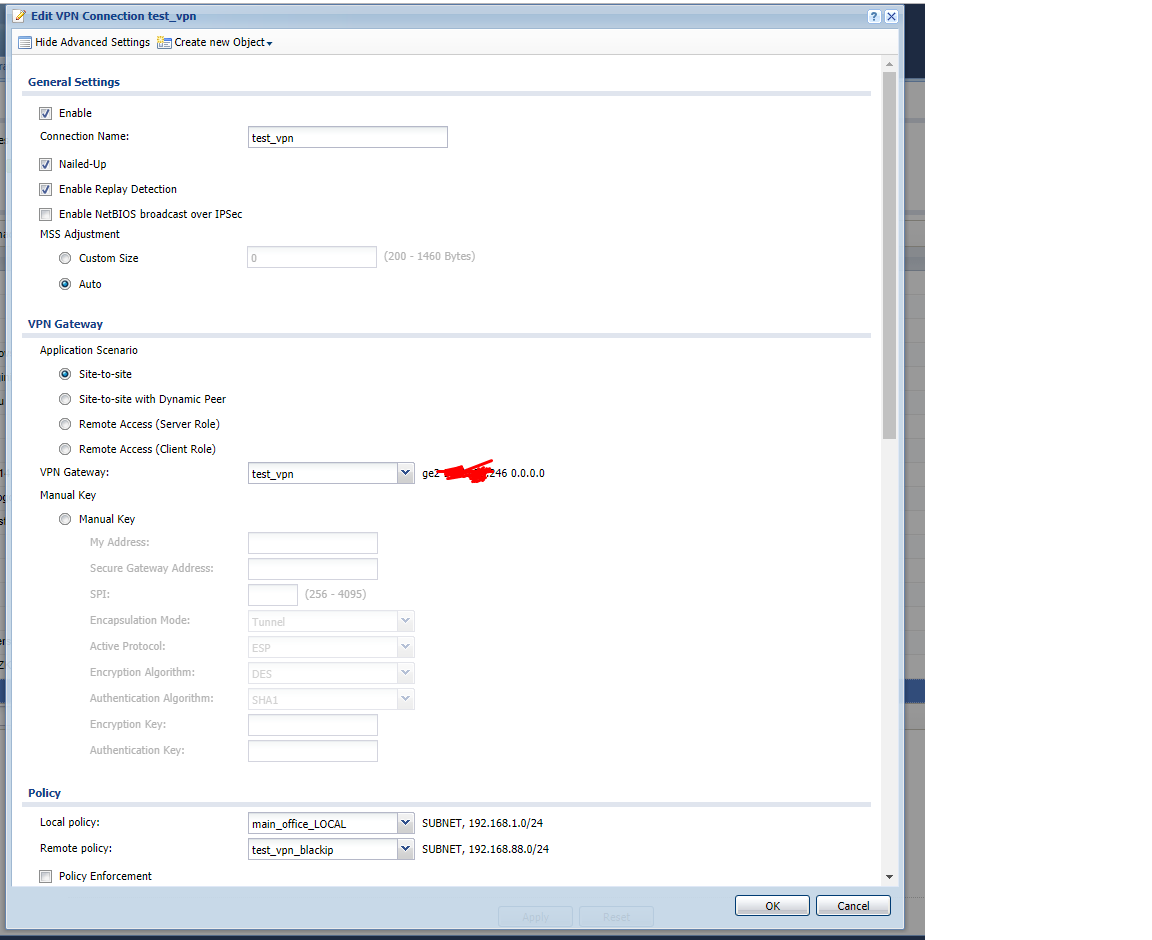
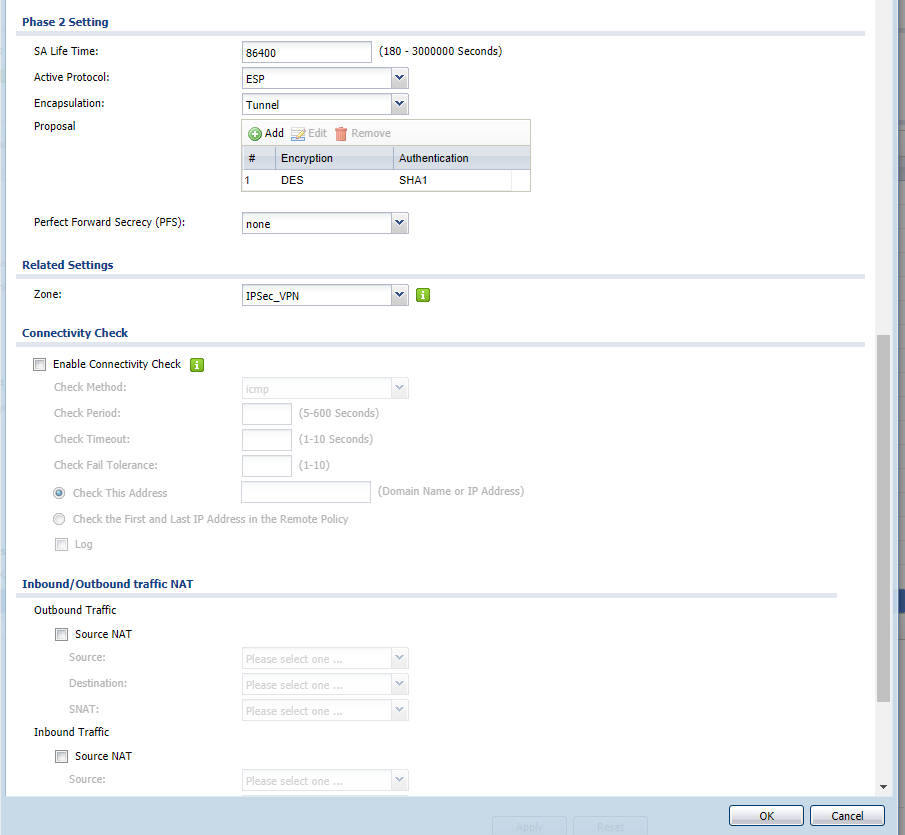
–ù–∞—Å—Ç—Ä–æ–π–∫–∞ Mikrotik:
–õ–æ–∫–∞–ª—å–Ω–∞—è —Å–µ—Ç—å - 192.168.88.0
/ip ipsec> policy print
Flags: T - template, X - disabled, D - dynamic, I - invalid, A - active, * - default
0 T * group=default src-address=::/0 dst-address=::/0 protocol=all proposal=default template=yes
1 A src-address=192.168.88.0/24 src-port=any dst-address=192.168.1.0/24 dst-port=any protocol=all action=encrypt
level=require ipsec-protocols=esp tunnel=yes sa-src-address=111.111.111.246 sa-dst-address=111.1111.111.158
proposal=zyxel ph2-count=1
/ip ipsec> peer print
Flags: X - disabled, D - dynamic, R - responder
0 ;;; Unsafe configuration, suggestion to use certificates
address=111.111.1111.158/32 profile=default auth-method=pre-shared-key secret="1111111" generate-policy=no
policy-template-group=default exchange-mode=main send-initial-contact=yes
/ip ipsec> proposal print
Flags: X - disabled, * - default
0 * name="default" auth-algorithms=sha1 enc-algorithms=aes-256-cbc,aes-192-cbc,aes-128-cbc lifetime=30m
pfs-group=modp1024
1 name="zyxel" auth-algorithms=sha1 enc-algorithms=des lifetime=30m pfs-group=none
/ip firewall> filter print
Flags: X - disabled, I - invalid, D - dynamic
0 D ;;; special dummy rule to show fasttrack counters
chain=forward action=passthrough
1 ;;; defconf: accept ICMP
chain=input action=accept protocol=icmp log=no log-prefix=""
2 ;;; defconf: accept established,related
chain=input action=accept connection-state=established,related log=no log-prefix=""
3 ;;; defconf: fasttrack
chain=forward action=fasttrack-connection connection-state=established,related log=no log-prefix=""
4 ;;; defconf: accept established,related
chain=forward action=accept connection-state=established,related log=no log-prefix=""
5 ;;; defconf: drop invalid
chain=forward action=drop connection-state=invalid log=no log-prefix=""
6 X ;;; defconf: drop all from WAN not DSTNATed
chain=forward action=drop connection-state=new connection-nat-state=!dstnat in-interface=ether1 log=no
log-prefix=""
7 ;;; Allow IKE/NAT-T for IPSec
chain=input protocol=udp dst-port=500,4500 log-prefix="IKE/NAT-T"
8 ;;; Allow ESP for IPSec
chain=input protocol=ipsec-esp log-prefix="ESP"
9 ;;; Allow IKE/NAT-T for IPSec
chain=output protocol=udp src-port=500,4500 log-prefix="IKE/NAT-T"
10 ;;; Allow ESP for IPSec
chain=output protocol=ipsec-esp log-prefix="ESP"
11 ;;; Accept, when packet from internal net to internal net (between vlans)
chain=forward action=accept src-address-list=Internal nets dst-address-list=Internal nets log=no log-prefix=""
12 chain=forward action=accept src-address=192.168.88.0/24 dst-address=192.168.1.0/24 log=no log-prefix=""
/ip firewall> nat print
Flags: X - disabled, I - invalid, D - dynamic
0 ;;; place hotspot rules here
chain=unused-hs-chain action=passthrough
1 ;;; defconf: masquerade
chain=srcnat action=masquerade dst-address=!192.168.1.0/24 out-interface=ether1 log=no log-prefix=""
2 ;;; masquerade hotspot network
chain=srcnat action=masquerade log=no log-prefix=""
3 ;;; masquerade hotspot network
chain=srcnat action=masquerade log=no log-prefix=""
4 ;;; masquerade hotspot network
chain=srcnat action=masquerade log=no log-prefix=""
5 ;;; masquerade hotspot network
chain=srcnat action=masquerade log=no log-prefix=""
6 ;;; masquerade hotspot network
chain=srcnat action=masquerade log=no log-prefix=""
7 ;;; masquerade hotspot network
chain=srcnat action=masquerade log=no log-prefix=""
8 ;;; Does not touch IPSec ESP packets to avoid break packets checksum
chain=srcnat out-interface=ether1 log-prefix="NAT avoid" ipsec-policy=out,ipsec
/ip route> print
Flags: X - disabled, A - active, D - dynamic, C - connect, S - static, r - rip, b - bgp, o - ospf, m - mme,
B - blackhole, U - unreachable, P - prohibit
# DST-ADDRESS PREF-SRC GATEWAY DISTANCE
0 ADS 0.0.0.0/0 11111.1111.1111.241 1
1 ADC 111111111111/28 11111111111 ether1 0
2 A S 192.168.1.0/24 ether1 1
3 ADC 192.168.88.0/24 192.168.88.1 bridge 0Answer the question
In order to leave comments, you need to log in
2 A S 192.168.1.0/24 ether1 11. There is no problem with routing, no manual routes need to be created. Everything is decided by policy. This is where you specify which networks are behind the tunnel. Should be mirrored on both sides. What rule 2 AS 192.168.1.0/24 ether1 1 should do is not clear.
2. We look at the 6th rule in the ip firewall filter, why is it higher than 12?
3. What's with nat? You can't do that chain=srcnat action=masquerade log=no log-prefix=""
in the policy src-address=192.168.88.0/24 src-port=any dst-address=192.168.1.0/24 you specify external addresses here.
In nata from a masquerade you remove a remote network, it and so will not go there.
Disable everything in the firewall for the duration of the setup.
Create an interface for vpn connection, in the route you set it as a gateway.
Like so
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question