Answer the question
In order to leave comments, you need to log in
Mikrotik, port forwarding via VPN, with access from LAN 1, LAN 2 and WAN?
To MikroTik LAN1 with "white IP" a PPTP "site-to-site" tunnel from MikroTik
LAN2 is installed. Access to the service_IP_LAN2:port at the external address of MikroTik-1 from any network is needed: from LAN1, LAN2 and outside.
If access is from LAN1 or LAN2, then the service is available.
The problem is accessing from the WAN. 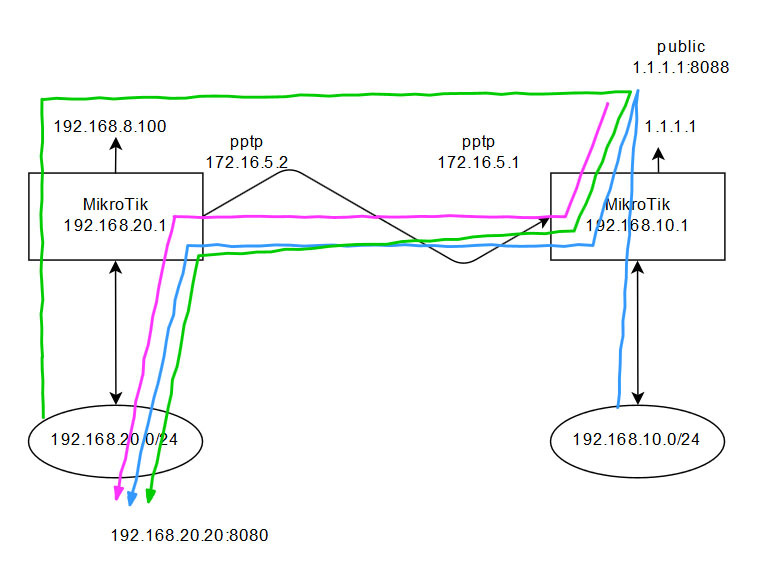
setup MK1
/ppp secret
add local-address=172.16.1.1 name=user password=*** remote-address=172.16.1.2 routes=\
"192.168.20.0/24 172.16.1.2 1" service=pptp
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" out-interface=ether1
add action=dst-nat chain=dstnat dst-port=8088 in-interface=ether1 \
protocol=tcp to-addresses=192.160.20.20 to- ports=8080
add action=dst-nat chain=dstnat dst-address-type=local dst-port=8088 in-interface=bridge \
protocol=tcp to-addresses=192.168.20.20 to-ports=8080
add action=masquerade chain=srcnat dst -address=192.168.20.20 dst-port=8080 protocol=tcp \
src-address=192.168.10.0/24
# DST-ADDRESS PREF-SRC GATEWAY DISTANCE
0 ADS 0.0.0.0/0 1.1.1.1 0
1 ADC 1.1.1.0/ 24 1.1.1.1 ether1 0
2 ADC 172.16.1.2/32 172.16.1.1 0
3 ADC 192.168.10.0/24 192.168.10.1 bridge 0
4 ADS 192.168.20.0/24 172.16.1.2 1
MK2 setting
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" out-interface=lte1
add action=dst-nat chain=dstnat dst-port=8088 in-interface=pptp-out1 protocol=tcp to-addresses =\
192.168.20.20 to-ports=8080
add action=dst-nat chain=dstnat dst-port=8088 in-interface=bridge protocol=tcp to-addresses=192.168.20.20 to-ports=8080
add action=masquerade chain= srcnat dst-address=192.168.20.20 dst-port=8080 protocol=tcp src-address=192.168.20.0/24
# DST-ADDRESS PREF-SRC GATEWAY DISTANCE
0 ADS 0.0.0.0/0 192.168.8.1 1
1 ADC 172.16.1.1 /32 172.16.1.2 pptp-out1 0
2 ADC 192.168.8.0/24 192.168.8.100 lte1 0
3 AS 192.168.10.0/24 pptp-out1 1
4 ADC 192.168.20.0/24 192.168.20.1 bridge 0
Google VPN site-to-site, Hairpin_NAT.
Tell me, what's wrong?
Answer the question
In order to leave comments, you need to log in
on mk2 set default gateway mk1 with route mark mk1
in mangle mark all traffic coming to mk2 from mk1 and hang route mark mk1
On mk2, remake dst-nat, specifying not in-interface, but dst-address = 1.1.1.1. This should be enough
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question