Answer the question
In order to leave comments, you need to log in
How to fix internet PPPOE?
Hello! Faced such a problem. I would be very grateful for advice.
The client has a Mikrotik RB951Ui-2HnD, firmware 6.48 (stable). Provider Rostelecom, connection via PPPOE. Some sites do not open, for example, rambler (came to hand). Sometimes google.com does not open, but google.ru opens. Changed DNS servers to public 8.8.8.8, 8.8.4.4. - did not help, changed MTU - did not help. Everything responds, all traces pass, everything is super, but some of the sites do not open.
If you turn on the VPN in the opera, then everything is ok, it works like a clock.
Rostelecom says that everything works on their part.
What could be? Where to dig?
/export hide-sensitive output
# jan/14/2021 16:13:36 by RouterOS 6.48
# software id = NIDE-AXVM
#
# model = 951Ui-2HnD
# serial number = 8A7308******
/interface bridge
add admin-mac=CC:2D:E0:2C:***** arp=proxy-arp auto-mac=no comment=defconf \
igmp-snooping=yes name=bridge
/interface pppoe-client
add add-default-route=yes disabled=no interface=ether1 max-mtu=1492 name=\
pppoe-out1 use-peer-dns=yes user=szt
/interface wireless
set [ find default-name=wlan1 ] antenna-gain=0 band=2ghz-b/g/n channel-width=\
20/40mhz-XX country=russia disabled=no distance=indoors frequency=auto \
frequency-mode=manual-txpower mode=ap-bridge ssid=Studio-s station-roaming=\
enabled wireless-protocol=802.11
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/interface wireless security-profiles
set [ find default=yes ] authentication-types=wpa-psk mode=dynamic-keys \
supplicant-identity=MikroTik
/ip pool
add name=dhcp ranges=192.168.1.10-192.168.1.254
/ip dhcp-server
add address-pool=dhcp interface=bridge name=defconf
/ppp profile
set *0 change-tcp-mss=default
/user group
set full policy="local,telnet,ssh,ftp,reboot,read,write,policy,test,winbox,passw\
ord,web,sniff,sensitive,api,romon,dude,tikapp"
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3
add bridge=bridge comment=defconf interface=ether4
add bridge=bridge comment=defconf interface=ether5
add bridge=bridge comment=defconf interface=wlan1
/ip neighbor discovery-settings
set discover-interface-list=LAN
/interface list member
add comment=defconf interface=bridge list=LAN
add comment=defconf interface=ether1 list=WAN
/ip address
add address=192.168.1.22/24 comment=defconf interface=bridge network=\
192.168.1.0
/ip dhcp-client
add comment=defconf interface=ether1
/ip dns static
add address=192.168.1.22 name=router.lan
/ip firewall address-list
add address=test.*****.ru list=WhiteList
add address=zabbix.****.ru list=WhiteList
add address=home.******.ru list=WhiteList
add address=91.204.***.*** comment=Buh list=WhiteList
add address=188.134.**.** comment=Iliya list=WhiteList
add address=77.247.***.*** comment=posntnikov list=WhiteList
add address=85.235.***.**** comment=posntnikov list=WhiteList
/ip firewall filter
add action=accept chain=input dst-port=161 protocol=udp src-address-list=\
WhiteList
add action=accept chain=input comment=Winbox dst-port=8291 protocol=tcp \
src-address-list=WhiteList
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" connection-state=\
invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface=pppoe-out1
add action=drop chain=input in-interface=pppoe-out1
/ip firewall mangle
add action=change-mss chain=forward new-mss=1360 protocol=tcp tcp-flags=syn \
tcp-mss=1453-65535
/ip firewall nat
add action=masquerade chain=srcnat out-interface=pppoe-out1
add action=dst-nat chain=dstnat comment=VideoRegistrator dst-port=80 protocol=\
tcp to-addresses=192.168.1.49 to-ports=80
add action=dst-nat chain=dstnat comment=VideoRegistrator dst-port=6036 \
protocol=tcp to-addresses=192.168.1.49 to-ports=6036
add action=dst-nat chain=dstnat comment=SRV1_RDP dst-port=49391 protocol=tcp \
src-address-list=WhiteList to-addresses=192.168.1.11 to-ports=3389
add action=dst-nat chain=dstnat comment=SRV1_Zabbix dst-port=10055 protocol=tcp \
src-address-list=WhiteList to-addresses=192.168.1.11 to-ports=10050
add action=dst-nat chain=dstnat comment=SRV2_RDP dst-port=33399 protocol=tcp \
src-address-list=WhiteList to-addresses=192.168.1.201 to-ports=3389
add action=dst-nat chain=dstnat comment=SRV2_Zabbix dst-port=10056 protocol=tcp \
src-address-list=WhiteList to-addresses=192.168.1.201 to-ports=10050
add action=dst-nat chain=dstnat comment="1\D1VM_RDP" dst-port=32084 protocol=\
tcp src-address-list=WhiteList to-addresses=192.168.1.155 to-ports=3389
add action=dst-nat chain=dstnat comment="1\D1VM_Zabbix" dst-port=10057 \
protocol=tcp src-address-list=WhiteList to-addresses=192.168.1.155 \
to-ports=10050
add action=dst-nat chain=dstnat comment=ServerVM_RDP dst-port=8939 protocol=tcp \
src-address-list=WhiteList to-addresses=192.168.1.1 to-ports=33398
add action=dst-nat chain=dstnat comment=ServerVM_Zabbix dst-port=10058 \
protocol=tcp src-address-list=WhiteList to-addresses=192.168.1.1 to-ports=\
10050
add action=dst-nat chain=dstnat comment=D4WVM_RDP dst-port=44268 protocol=tcp \
src-address-list=WhiteList to-addresses=192.168.1.67 to-ports=3389
add action=dst-nat chain=dstnat comment=D4WVM_Zabbix dst-port=10059 protocol=\
tcp src-address-list=WhiteList to-addresses=192.168.1.67 to-ports=10050
add action=dst-nat chain=dstnat comment=ATC_SSH dst-port=25661 protocol=tcp \
src-address-list=WhiteList to-addresses=192.168.1.10 to-ports=22
add action=dst-nat chain=dstnat comment=ATC_Zabbix dst-port=10060 protocol=tcp \
src-address-list=WhiteList to-addresses=192.168.1.10 to-ports=10050
/snmp
set [email protected]*****.ru enabled=yes location=Studio***** trap-version=2
/system clock
set time-zone-name=Europe/Moscow
/tool mac-server
set allowed-interface-list=LAN
/tool mac-server mac-winbox
set allowed-interface-list=LANAnswer the question
In order to leave comments, you need to log in
Gregory , poisons , Drno thanks a lot for the feedback, but the problem turned out to be that there is no masquerading.
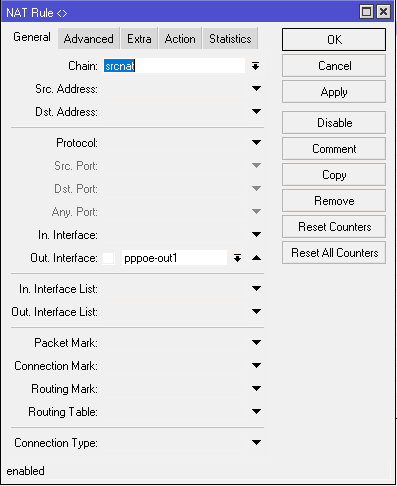
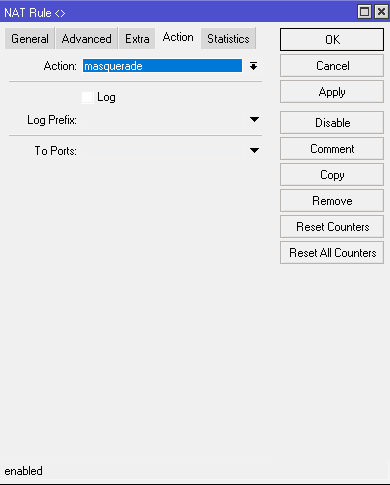
Also, which is not unimportant, it is not recommended to create NAT rules like your ip: 80
Check DNS, try running everything through which VPN thread... to check
Try DNS 1.1.1.1
/ppp profile
set *0 change-tcp-mss=default
/interface pppoe-client
add add-default-route=yes disabled=no interface=ether1 max-mtu=1492 name=\
pppoe-out1 use-peer-dns=yes user=szt
/ip firewall mangle
add action=change-mss chain=forward new-mss=1360 protocol=tcp tcp-flags=syn \
tcp-mss=1453-65535
/ip dhcp-client
add comment=defconf interface=ether1
add action=dst-nat chain=dstnat comment=VideoRegistrator dst-port=80 protocol=\
tcp to-addresses=192.168.1.49 to-ports=80
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question