Answer the question
In order to leave comments, you need to log in
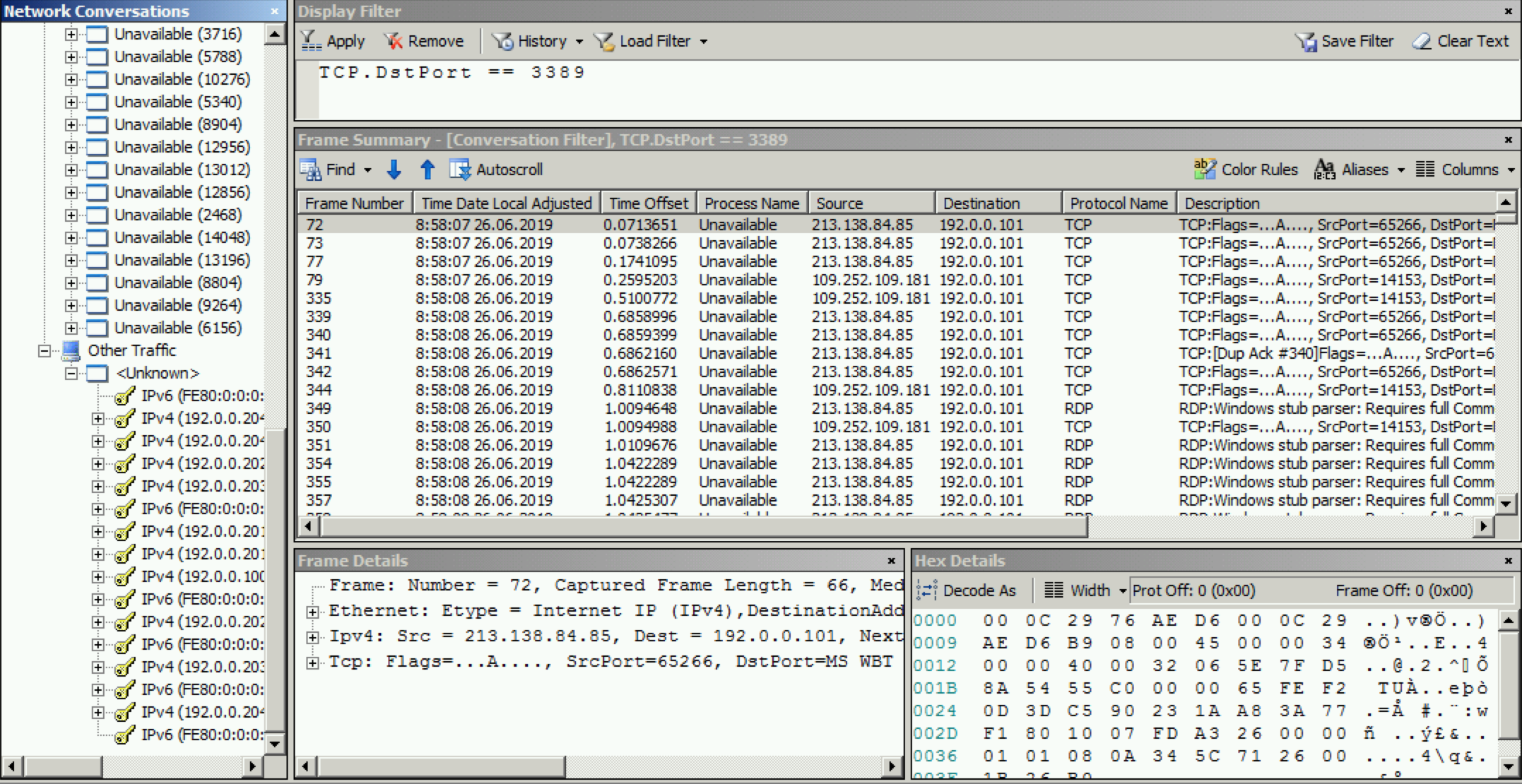
Does not let in half of the cases via RDP to the 2008R2 terminal, how to identify the problem?
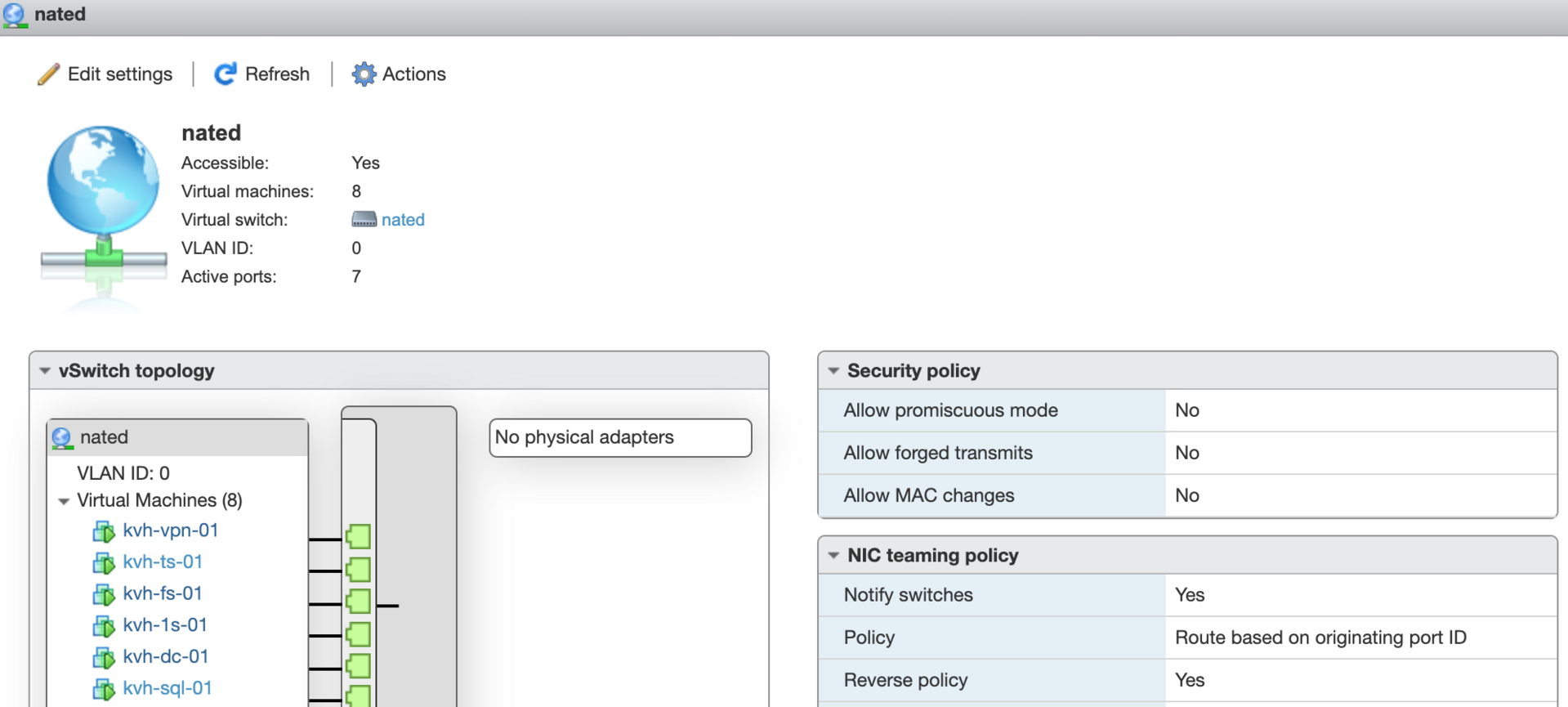
Terminal 2008R2 on a virtual machine inside ESXi 6.5 on a dedicated server in Hetzner. PfSense serves as a virtual machine router, it has a white IP and port forwarding to the virtual machine. Except for ESXi, the latest updates are everywhere.
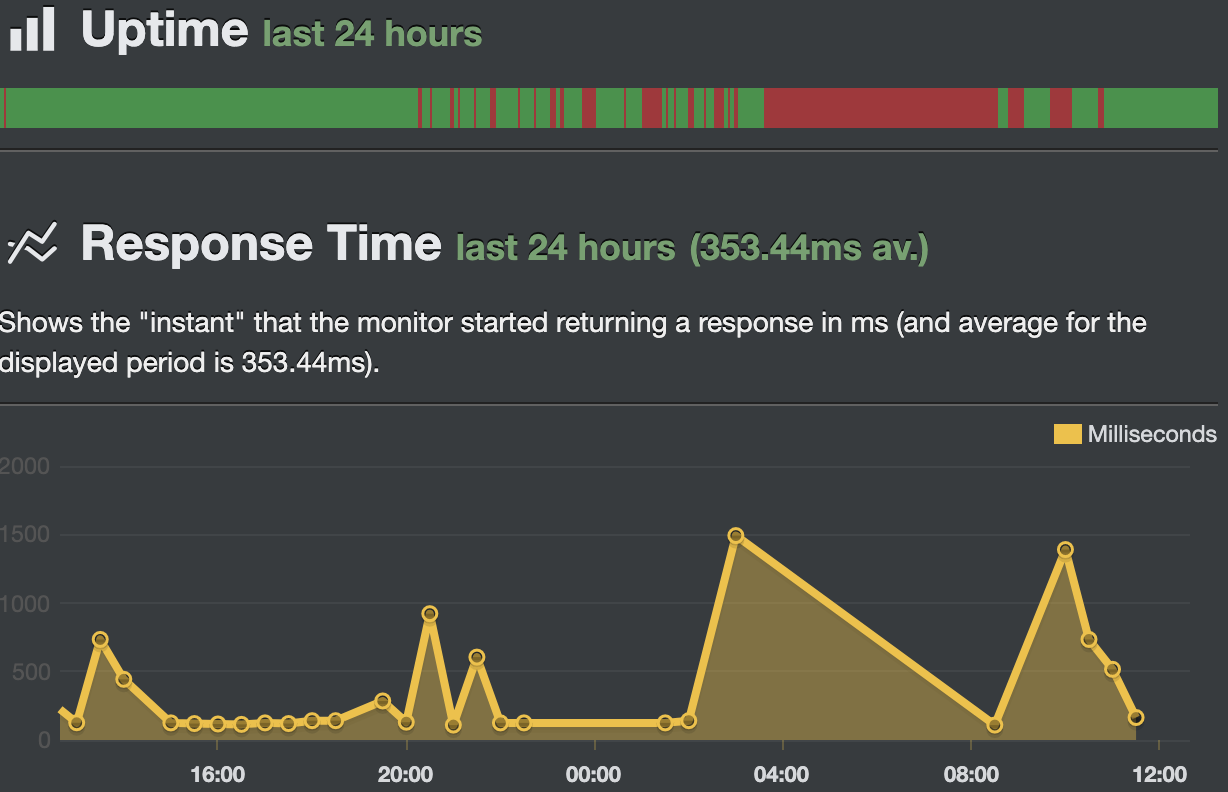
Suddenly, the uptime robot began to write messages about the unavailability of the server by port. Then users ceased to start up on RDP. It happens suddenly, without explanation. Just a feeling that the terminal is not available. Time from 6-7 lets, if you quickly make attempts to connect. Subjectively, with RDCman, the chance to connect is much higher than with mstsc. On Remmina, users have not heard anyone complain at all.
Answer the question
In order to leave comments, you need to log in
udp1. I made forwarding 3390 on the router to the same place in 3389 on the machine - packets do not disappear there. It turns out that someone clogs 3389 with garbage?
1. primitive Firewall after updating venda can go)
2. the second cant with the routing table on the router. Were there experiments? It could be preserved until you clean it.
3. I read that the bourgeoisie had similar problems: all of a sudden for no reason. It is necessary to prescribe something in system politicians. Google it: w.. 2008 rdp no connection system policy
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question