Answer the question
In order to leave comments, you need to log in
Why doesn't iptables block incoming traffic from an IP address on port 80?
(UPDATE: I fixed a logical error in the command, but this did not solve the problem).
Hello. It is necessary to block access to the server via HTTP (80) port to a specific IP address.
I enter:
iptables -I INPUT -s *here is the IP to ban* -p tcp --dport 80 -j DROP
A rule is created, I check: 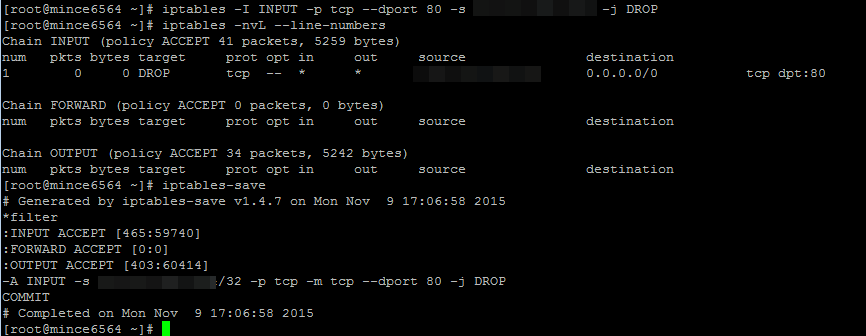
I test on my own IP. I calmly go to the sites, i.e. does not block. Tried to use REJECT instead of DROP, same thing.
If you block completely (without -p, --dport), then you cannot connect via SSH, FTP (resets), i.e. bans, but over HTTP all the rules and the site comes.
If you block port 21 (FTP), then it resets, i.e. bans. The problem is only with port 80!!
What could be the reason? In general, I set up fail2ban + nginx req limit module, and did not block the IP addresses of intruders properly, but now I’m just testing banal iptables commands in the terminal, and I can’t understand why it doesn’t work. Please help a beginner. Server on Linux CentOS 6, for sites: nginx on the front end, and apache on the back end.
Answer the question
In order to leave comments, you need to log in
update. Due to the fact that proxying (anti-ddos) is enabled, iptables cannot be fully used on the server, as I was told in the technical support of the hosting provider.
-d destination
your rule says:
incoming packets destined for the address (un that you ban) and port 80 - discard.
How do you imagine it at all?
-s ban_ip and everything will be fine
If there is a proxy, then ask the provider to send x_forwarder_for and block on it using the frontend.
it is possible to look at the full exhaust of rules
in the nat table is REDIRECT from the 80th port.
it will work before INPUT in the filter table.
the easiest way to check where flies is
to execute
iptables -A INPUT -s BANNED_IP -j LOG
iptables -t nat -A PREROUTING -s BANNED_IP -j LOGGood day!
Please don't kick me too hard, I'm just starting to deal with iptables...
But it's also a problem, Mandriva has VBox, Box has a mail server on Win2008 server H-Mail ip 192.185.0.55
Constantly trying to break. ( IPs are different, already a whole list)
------------------------------------ --------------------
3949 15:03:16.618245 vnesh_IP 180.166.46.151 SMTP S: 535 Authentication failed. Too many invalid logon attempts.
-------------------------------------------------- ------------
do this iptables -I INPUT -s 180.166.46.151 -j DROP
no result
iptables-save
# Generated by iptables-save v1.4.7 on Thu Jun 2 14:49:52 2016
*raw
:PREROUTING ACCEPT [1758:231837]
:OUTPUT ACCEPT [1456:389798]
COMMIT
# Completed on Thu Jun 2 14:49:52 2016
# Generated by iptables-save v1.4.7 on Thu Jun 2 14:49:52 2016
*nat
:PREROUTING ACCEPT [151:17934]
:POSTROUTING ACCEPT [20:1347]
:OUTPUT ACCEPT [20:1347]
-A PREROUTING -d vnesh_IP -p tcp -m multiport --dports 25 -j DNAT --to-destination 192.185. 0.55
-A PREROUTING -d vnesh_IP -p tcp -m multiport --dports 26 -j DNAT --to-destination 192.185.0.55
-A PREROUTING -d vnesh_IP -p tcp -m multiport --dports 80 -j DNAT --to -destination 192.185.0.99
-A POSTROUTING -d 192.185.0.55/32 -p tcp -m multiport --dports 25 -j SNAT --to-source 192.185.0.115
-A POSTROUTING -d 192.185.0.55/32 -p tcp -m multiport --dports 26 -j SNAT --to-source 192.185.0.84
-A POSTROUTING -d 192.185.0.99/32 -p tcp -m multiport --dports 80 -j SNAT --to-source 192.185.0.84
-A OUTPUT -d vnesh_IP -p tcp -m multiport --dports 25 -j DNAT --to-destination 192.185.0.55
-A OUTPUT -d vnesh_IP -p tcp -m multiport --dports 26 -j DNAT --to-destination 192.185.0.55
-A OUTPUT -d vnesh_IP -p tcp -m multiport --dports 80 -j DNAT --to-destination 192.185.0.99
COMMIT
# Completed on Thu Jun 2 14:49:52 2016
# Generated by iptables-save v1.4.7 on Thu Jun 2 14:49:52 2016
*mangle
:PREROUTING ACCEPT [1758:231837]
:INPUT ACCEPT [1445:198515]
:FORWARD ACCEPT [252:24954 ]
:OUTPUT ACCEPT [1456:389798]
:POSTROUTING ACCEPT [1709:414821]
:tcfor - [0:0]
:tcout - [0:0]
:tcpost - [0:0]
:tcpre - [0:0]
-A PREROUTING -j tcpre
-A FORWARD -j MARK --set-xmark 0x0/0xffffffff
-A FORWARD -j tcfor
-A OUTPUT -j tcout
-A POSTROUTING -j tcpost
COMMIT
# Completed on Thu Jun 2 14:49:52 2016
# Generated by iptables-save v1.4.7 on Thu Jun 2 14:49:52 2016
*filter
:INPUT DROP [0:0]
:FORWARD DROP [0:0]
:OUTPUT DROP [0:0]
:Drop - [0: 0]
:Ifw - [0:0]
:Reject - [0:0]
:dropBcast - [0:0]
:dropInvalid - [0:0]
:dropNotSyn - [0:0]
:dynamic - [0:0]
:fw2net - [0:0]
:logdrop - [0:0]
:logreject - [0:0]
:net2fw - [0:0]
:reject - [0:0]
:shorewall - [0:0]
-A INPUT -s 180.166.46.151/32 -j DROP
-A INPUT -j Ifw
-A INPUT -m conntrack --ctstate INVALID,NEW -j dynamic
-A INPUT -i eth2 -j net2fw
- A INPUT -i ppp0 -j net2fw
-A INPUT -i eth3 -j net2fw
-A INPUT -i vboxnet0 -j net2fw
-A INPUT -i eth1 -j net2fw
-A INPUT -i eth0 -j net2fw
-A INPUT -i lo -j ACCEPT
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A INPUT -j Reject
-A INPUT -j LOG --log-prefix "Shorewall:INPUT:REJECT:" --log-level 6
-A INPUT -g reject
-A FORWARD -m conntrack --ctstate INVALID,NEW -j dynamic
-A FORWARD -i ppp0 -o eth2 -j ACCEPT
-A FORWARD -i ppp0 -o eth3 -j ACCEPT
-A FORWARD -i ppp0 -o vboxnet0 -j ACCEPT
-A FORWARD -i ppp0 -o eth1 -j ACCEPT
-A FORWARD -i ppp0 -o eth0 -j ACCEPT
-A FORWARD -i eth2 -o ppp0 -j ACCEPT
-A FORWARD -i eth2 - o eth3 -j ACCEPT
-A FORWARD -i eth2 -o vboxnet0 -j ACCEPT
-A FORWARD -i eth2 -o eth1 -j ACCEPT
-A FORWARD -i eth2 -o eth0 -j ACCEPT
-A FORWARD -i eth3 -o ppp0 -j ACCEPT
-A FORWARD -i eth3 -o eth2 -j ACCEPT
-A FORWARD -i eth3 -o vboxnet0 -j ACCEPT
-A FORWARD -i eth3 -o eth1 -j ACCEPT
-A FORWARD -i eth3 -o eth0 -j ACCEPT
-A FORWARD -i vboxnet0 -o ppp0 -j ACCEPT
-A FORWARD -i vboxnet0 -o eth2 -j ACCEPT
-A FORWARD -i vboxnet0 -o eth3 -j ACCEPT
-A FORWARD -i vboxnet0 -o eth1 -j ACCEPT
-A FORWARD -i vboxnet0 -o eth0 -j ACCEPT
-A FORWARD -i eth1 -o ppp0 -j ACCEPT
-A FORWARD -i eth1 -o eth2 -j ACCEPT
-A FORWARD - i eth1 -o eth3 -j ACCEPT
-A FORWARD -i eth1 -o vboxnet0 -j ACCEPT
-A FORWARD -i eth1 -o eth0 -j ACCEPT
-A FORWARD -i eth0 -o ppp0 -j ACCEPT
-A FORWARD -i eth0 -o eth2 -j ACCEPT
-A FORWARD -i eth0 -o eth3 -j ACCEPT
-A FORWARD -i eth0 -o vboxnet0 -j ACCEPT
-A FORWARD -i eth0 -o eth1 -j ACCEPT
-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -j Reject
-A FORWARD -j LOG --log-prefix "Shorewall:FORWARD:REJECT:" --log-level 6
-A FORWARD - g reject
-A OUTPUT -o eth2 -j fw2net
-A OUTPUT -o ppp0 -j fw2net
-A OUTPUT -o eth3 -j fw2net
-A OUTPUT -o vboxnet0 -j fw2net
-A OUTPUT -o eth1 -j fw2net
-A OUTPUT -o eth0 -j fw2net
-A OUTPUT -o lo -j ACCEPT
-A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A OUTPUT -j Reject
-A OUTPUT -j LOG --log-prefix "Shorewall: OUTPUT:REJECT:" --log-level 6
-A OUTPUT -g reject
-A Drop
-A Drop -p tcp -m tcp --dport 113 -m comment --comment "Auth" -j reject
-A Drop -j dropBcast
-A Drop -p icmp -m icmp --icmp-type 3/4 -m comment --comment "Needed ICMP types" -j ACCEPT
-A Drop -p icmp -m icmp --icmp- type 11 -m comment --comment "Needed ICMP types" -j ACCEPT
-A Drop -j dropInvalid
-A Drop -p udp -m multiport --dports 135,445 -m comment --comment "SMB" -j DROP
-A Drop -p udp -m udp --dport 137:139 -m comment --comment "SMB" -j DROP
-A Drop -p udp -m udp --sport 137 --dport 1024:65535 -m comment --comment " SMB" -j DROP
-A Drop -p tcp -m multiport --dports 135,139,445 -m comment --comment "SMB" -j DROP
-A Drop -p udp -m udp --dport 1900 -m comment --comment " UPnP" -j DROP
-A Drop -p tcp -j dropNotSyn
-A Drop -p udp -m udp --sport 53 -m comment --comment "Late DNS Replies" -j DROP
-A Ifw -m set --match-set ifw_wl src -j RETURN
-A Ifw -m set - -match-set ifw_bl src -j DROP
-A Ifw -m state --state INVALID,NEW -m psd --psd-weight-threshold 10 --psd-delay-threshold 10000 --psd-lo-ports-weight 2 --psd-hi-ports-weight 1 -j IFWLOG --log-prefix "SCAN"
-A Ifw -p udp -m state --state NEW -m udp --dport 67 -j IFWLOG --log-prefix " NEW"
-A Ifw -p udp -m state --state NEW -m udp --dport 68 -j IFWLOG --log-prefix "NEW"
-A Ifw -p tcp -m state --state NEW -m tcp - -dport 22 -j IFWLOG --log-prefix "NEW"
-A Ifw -p tcp -m state --state NEW -m tcp --dport 25 -j IFWLOG --log-prefix "NEW"
-A Ifw -p tcp -m state --state NEW -m tcp --dport 3128 -j IFWLOG --log-prefix "NEW"
-A Reject
-A Reject -p tcp -m tcp --dport 113 -m comment --comment "Auth" -j reject
-A Reject -j dropBcast
-A Reject -p icmp -m icmp --icmp-type 3/4 -m comment --comment "Needed ICMP types" -j ACCEPT
-A Reject - p icmp -m icmp --icmp-type 11 -m comment --comment "Needed ICMP types" -j ACCEPT
-A Reject -j dropInvalid
-A Reject -p udp -m multiport --dports 135,445 -m comment --comment "SMB" -j reject
-A Reject -p udp -m udp --dport 137:139 -m comment --comment "SMB" -j reject
-A Reject -p udp -m udp --sport 137 --dport 1024 :65535 -m comment --comment "SMB" -j reject
-A Reject -p tcp -m multiport --dports 135,139,445 -m comment --comment "SMB" -j reject
-A Reject -p udp -m udp --dport 1900 -m comment --comment "UPnP" -j DROP
-A Reject -p tcp -j dropNotSyn
-A Reject -p udp -m udp --sport 53 -m comment --comment "Late DNS Replies" -j DROP
-A dropBcast -m addrtype --dst-type BROADCAST -j DROP
-A dropBcast -d 224.0.0.0/4 -j DROP
-A dropInvalid -m conntrack --ctstate INVALID -j DROP
-A dropNotSyn -p tcp -m tcp ! --tcp-flags FIN,SYN,RST,ACK SYN -j DROP
-A fw2net -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A fw2net -j ACCEPT
-A logdrop -j DROP
-A logreject -j reject
- A net2fw -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A net2fw -p udp -m multiport --dports 67,68 -j ACCEPT
-A net2fw -p tcp -m multiport --dports 22,25,26,3128 -j ACCEPT
-A net2fw -j Drop
-A net2fw - j LOG --log-prefix "Shorewall:net2fw:DROP:" --log-level 6
-A net2fw -j DROP
-A reject -m addrtype --src-type BROADCAST -j DROP
-A reject -s 224.0.0.0 /4 -j DROP
-A reject -p igmp -j DROP
-A reject -p tcp -j REJECT --reject-with tcp-reset
-A reject -p udp -j REJECT --reject-with icmp-port-unreachable
-A reject -p icmp -j REJECT --reject-with icmp-host-unreachable
-A reject -j REJECT --reject-with icmp-host-prohibited
COMMIT
# Completed on Thu Jun 2 14:49:52 2016
Please advise where to dig?
And "your own IP" is the same, where do you turn iptables or turn it on the server, and check "your own" from another computer?
Just if the first, then such traffic can safely bypass the INPUT chain :)
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question