Answer the question
In order to leave comments, you need to log in
What is the problem with connecting to ipsec+ikev2 through certificates?
I watch with wireshark on the client and tcpdump on the server.
It goes like this:
the client asks the server for ikev_init; the
server responds ;
the client sends its certificate and the supported ciphers; the
server receives them and sends a response;
the client does not receive this response! (in some networks, the same client receives it and then the VPN connection succeeds)
The server sends a packet, but it does not reach the client:
mysite = domain of my server
clientdomain - my client
17:27:23.187306 IP (tos 0x0, ttl 64, id 48370, offset 0, flags [DF], proto UDP (17), length 365)
mysite.isakmp > clientdomain.432: isakmp 2.0 msgid 00000000: parent_sa ikev2_init[R]:
(sa: len=44
(p: #2 protoid=isakmp transform=4 len=44
(t: #1 type=encr id=aes (type=keylen value=0100))
(t: #2 type=integ id=hmac-sha )
(t: #3 type=prf id=hmac-sha )
(t: #4 type=dh id=modp1024 )))
(v2ke: len=128 group=modp1024)
(nonce: len=32 data=(c4a4d5aed36e40823c9a...bf291b136ca24898abf4000b0000000800004014))
(n: prot_id=#0 type=16388(nat_detection_source_ip))
(n: prot_id=#0 type=16389(nat_detection_destination_ip))
(v2cr: len=21)
(n: prot_id=#0 type=16404(status))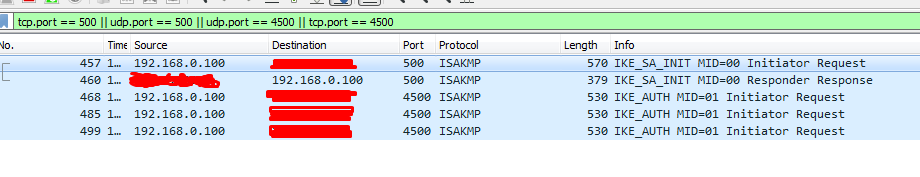
Answer the question
In order to leave comments, you need to log in
There is reason to believe that this is a crookedly configured ALG on the provider's network. You have a client behind a provider NAT, and this NAT cuts packets. In Online, this happens with L2TP in the network - the server sends a packet for negotiating connection parameters, the client receives it and ANSWERS. But the response does not reach the server. An output - is cut by provider. Fighting this is probably useless. I've been butting with online since April about this. "Your appeal has been forwarded to the relevant department, blah blah blah." Moreover, they do not say which particular department is the "profile" department. Well, that is, in other words, they put a bolt on such applications, and it is not redirected to any "profile departments".
In your case, the way out is to build IPSec in another tunnel - L2TP or PPTP.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question