Answer the question
In order to leave comments, you need to log in
Problem with IPsec Mikrotik?
I am setting up an IPsec tunnel between Mikrotik and Kerio Control. When creating a policy, for some reason it lights up red, and there are no packages.
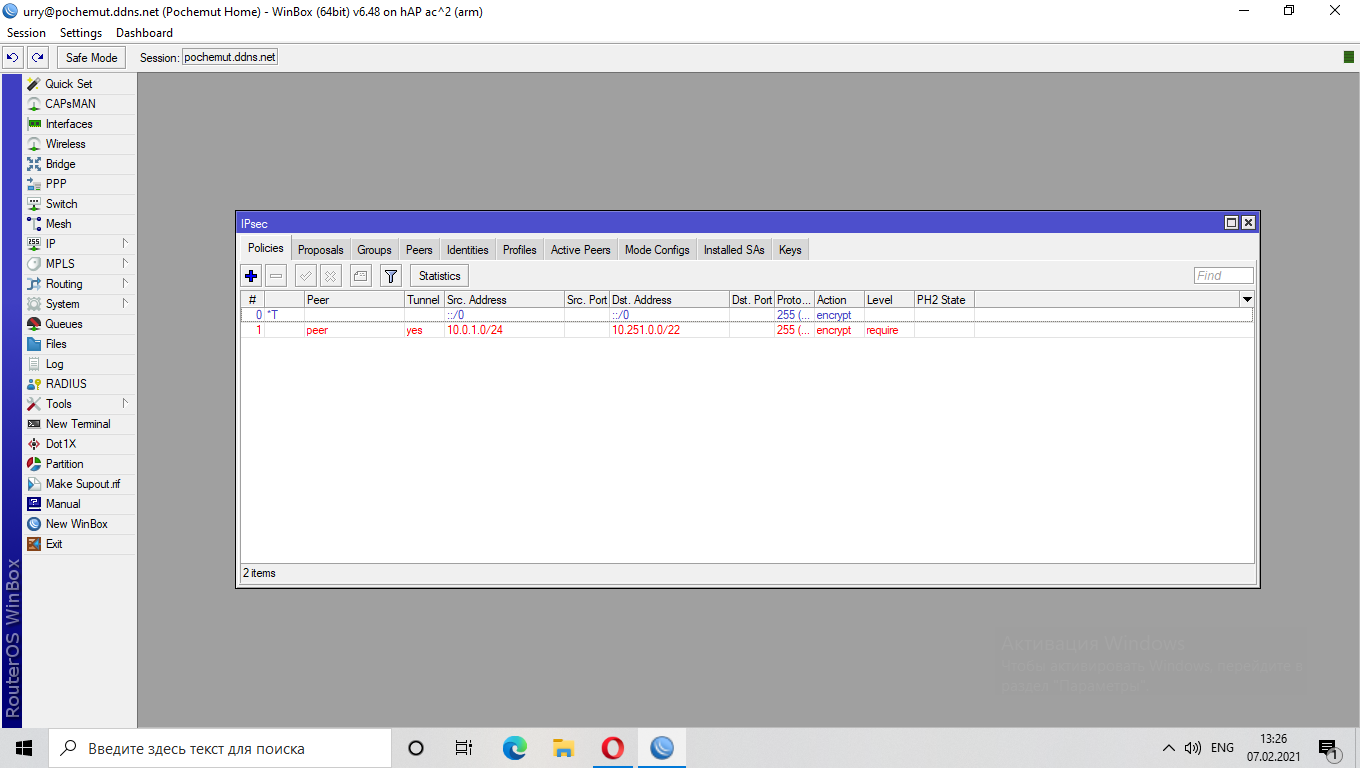
Here is the config itself:
/ip ipsec peer
add address=80.210.222.**/32 exchange-mode=ike2 name=peer passive=yes
/ip ipsec profile
set [ find default=yes ] dh-group=modp2048,modp1536 nat- traversal=no
/ip ipsec proposal
set [ find default=yes ] enc-algorithms=aes-256-cbc,aes-128-cbc,3des
/ip ipsec identity
add generate-policy=port-override peer=peer secret=** *******
/ip ipsec policy
add dst-address=10.251.0.0/22 peer=peer src-address=10.0.1.0/24 tunnel=yes
ps I did it using a working template in a similar situation.
Answer the question
In order to leave comments, you need to log in
The policy is red because there are no corresponding Peer and Identity settings, or they are incorrect / not applicable.
Here is a proposal I use for one office that is a little sick in the head:
/ip ipsec proposal
add auth-algorithms=sha256,sha1,md5 enc-algorithms=\
aes-256-cbc,aes-256-gcm,aes-192-cbc,aes-192-gcm,aes-128-cbc,aes-128-gcm lifetime=1hDidn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question