Answer the question
In order to leave comments, you need to log in
Mikrotik, how to turn off Internet access from branches through the central office?
Good day!
There is a network, a central office and branches, mikrotik gre + ipsec + rip equipment everywhere, connection of branches through the central office, all branches see each other, pppoe or static Internet access, static ip addresses everywhere, Internet access is provided at the central office through kerio, it is also the default router in the central office network, that is, there are two Internet channels in the central office - mikrotik for branches and kerio for everything else.
The question is how to wrap all Internet traffic from branches to kerio which is located at the central office?
As far as I understand, you need to use mangle, mark routing, but how to do this as correctly and optimally as possible?
Approximate scheme: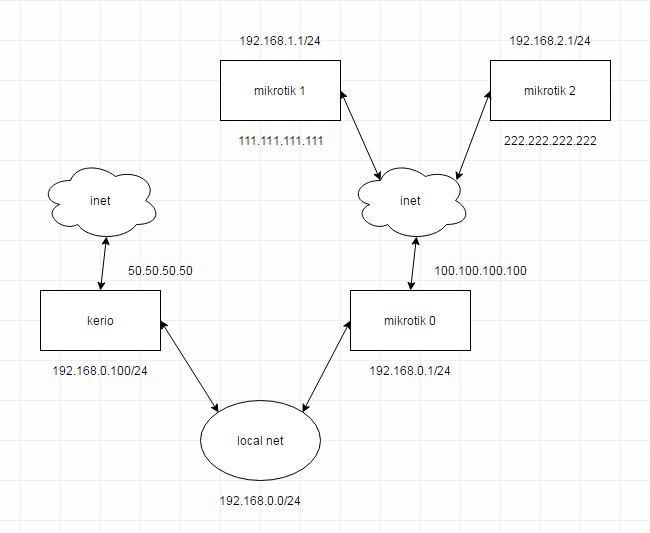
Answer the question
In order to leave comments, you need to log in
For the cisco, the "default-information originate" command is responsible for this.
For Mikrotik, I don't know where, but there should be something similar in the RIP settings, something like announce a default route or Distribute default
1. Raise VPN
2. Register routes
3. For all offices, wrap routes in VPN with Kerio gateway
Although it is asked - what for do you need it?
We mark packets in subnet branches with the necessary routing mark
/ip firewall mangle
add action=mark-routing chain=prerouting comment="route for xbox" in-interface=bridge-local new-routing-mark=rout_xx passthrough=no src-address=192.168 .88.0/24
/ip route
add check-gateway=ping distance=1 gateway=kerio_ip routing-mark=rout_xx
I post the configs of Mikrotiks, the ip-addresses do not match the scheme, the logic matches.
mikrotik 0:
# feb/21/2017 12:01:24 by RouterOS 6.38.1
#
/interface bridge
add admin-mac=6C:3B:6B:F8:22:1B auto-mac=no comment=defconf disabled=yes \
name=bridge
/interface ethernet
set [ find default-name=ether2 ] name=ether2-master
set [ find default-name=ether3 ] master-port=ether2-master
set [ find default-name=ether4 ] master-port=ether2-master
set [ find default-name=ether5 ] master-port=ether2-master
set [ find default-name=ether6 ] name=ether6-master
set [ find default-name=ether7 ] master-port=ether6-master
set [ find default-name=ether8 ] master-port=ether6-master
set [ find default-name=ether9 ] master-port=ether6-master
set [ find default-name=ether10 ] master-port=ether6-master
/interface gre
add allow-fast-path=no !keepalive name=gre-mk1-mk2 remote-address=50.50.50.50
add allow-fast-path=no !keepalive name=gre-mk1-mk3 remote-address=\
150.150.150.150
/ip neighbor discovery
set ether1 discover=no
/ip ipsec proposal
set [ find default=yes ] auth-algorithms=sha256,sha1 enc-algorithms=\
aes-256-cbc,aes-128-cbc
/ip pool
add name=default-dhcp ranges=192.168.88.10-192.168.88.254
/ip dhcp-server
add address-pool=default-dhcp interface=bridge name=defconf
/interface bridge port
add bridge=bridge comment=defconf interface=ether2-master
add bridge=bridge comment=defconf interface=ether6-master
add bridge=bridge comment=defconf interface=sfp1
/ip address
add address=192.168.111.1/24 comment=defconf disabled=yes interface=\
ether2-master network=192.168.111.0
add address=100.100.100.100/24 interface=ether1 network=100.100.100.0
add address=172.16.255.10/30 interface=gre-mk1-mk2 network=172.16.255.8
add address=192.168.0.6/24 interface=ether3 network=192.168.0.0
add address=172.16.255.6/30 interface=gre-mk1-mk3 network=172.16.255.4
/ip dhcp-client
add comment=defconf dhcp-options=hostname,clientid interface=ether1
/ip dhcp-server network
add address=192.168.88.0/24 comment=defconf gateway=192.168.88.1 netmask=24
/ip dns
set allow-remote-requests=yes servers=100.100.100.1
/ip dns static
add address=192.168.88.100 name=router
/ip firewall address-list
add address=192.168.0.0/24 list=LocalNet
add address=192.168.111.0/24 list=LocalNet
add address=192.168.222.0/24 list=LocalNet
add address=172.16.255.0/24 list=LocalNet
add address=192.168.100.0/24 list=LocalNet
/ip firewall filter
add action=drop chain=input connection-state=invalid
add action=accept chain=input
add action=drop chain=input comment="defconf: drop all from WAN" \
in-interface=ether1
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=accept chain=forward
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface=ether1
/ip firewall mangle
add action=mark-routing chain=prerouting dst-address-list=!LocalNet \
new-routing-mark=inet passthrough=no src-address-list=LocalNet
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" disabled=yes \
out-interface=ether1
/ip ipsec peer
add address=50.50.50.50/32 enc-algorithm=aes-128 local-address=\
100.100.100.100 nat-traversal=no secret=1234
add address=150.150.150.150/32 enc-algorithm=aes-128 local-address=\
100.100.100.100 nat-traversal=no secret=1234
/ip ipsec policy
add dst-address=50.50.50.50/32 sa-dst-address=50.50.50.50 sa-src-address=\
100.100.100.100 src-address=100.100.100.100/32
add dst-address=150.150.150.150/32 sa-dst-address=150.150.150.150 \
sa-src-address=100.100.100.100 src-address=100.100.100.100/32
/ip route
add distance=1 gateway=192.168.0.230 routing-mark=inet
add distance=5 gateway=100.100.100.1
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www-ssl certificate=cert1 disabled=no
set api disabled=yes
set api-ssl disabled=yes
/routing rip interface
add interface=gre-mk1-mk2 send=v1-2
add interface=gre-mk1-mk3 send=v1-2
/routing rip neighbor
add address=172.16.255.9
add address=172.16.255.5
/routing rip network
add disabled=yes network=192.168.111.0/24
add network=192.168.0.0/24
/system clock
set time-zone-name=Asia/Yekaterinburg
/tool mac-server
set [ find default=yes ] disabled=yes
add interface=bridge
/tool mac-server mac-winbox
set [ find default=yes ] disabled=yes
add interface=bridge# feb/06/2017 22:35:09 by RouterOS 6.38.1
#
/interface ethernet
set [ find default-name=ether2 ] name=ether2-master
set [ find default-name=ether3 ] master-port=ether2-master
set [ find default-name=ether4 ] master-port=ether2-master
set [ find default-name=ether5 ] master-port=ether2-master
/interface gre
add allow-fast-path=no !keepalive name=gre-mk2-mk1 remote-address=\
100.100.100.100
/ip neighbor discovery
set ether1 discover=no
/ip ipsec proposal
set [ find default=yes ] auth-algorithms=sha256,sha1 enc-algorithms=\
aes-256-cbc,aes-128-cbc
/ip pool
add name=default-dhcp ranges=192.168.88.10-192.168.88.254
/ip dhcp-server
add address-pool=default-dhcp interface=ether2-master name=defconf
/ip address
add address=192.168.222.1/24 comment=defconf interface=ether2-master network=\
192.168.222.0
add address=50.50.50.50/24 interface=ether1 network=50.50.50.0
add address=172.16.255.9/30 interface=gre-mk2-mk1 network=172.16.255.8
/ip dhcp-client
add comment=defconf dhcp-options=hostname,clientid interface=ether1
/ip dhcp-server network
add address=192.168.88.0/24 comment=defconf gateway=192.168.88.1 netmask=24
/ip dns
set allow-remote-requests=yes servers=50.50.50.1
/ip dns static
add address=192.168.88.50 name=router
/ip firewall address-list
add address=192.168.222.0/24 list=LocalNet
add address=192.168.111.0/24 list=LocalNet
add address=192.168.0.0/24 list=LocalNet
add address=172.16.255.0/24 list=LocalNet
add address=192.168.100.0/24 list=LocalNet
/ip firewall filter
add action=drop chain=input connection-state=invalid
add action=accept chain=input
add action=drop chain=input comment="defconf: drop all from WAN" \
in-interface=ether1
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=accept chain=forward
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface=ether1
/ip firewall mangle
add action=mark-routing chain=prerouting dst-address-list=!LocalNet \
new-routing-mark=inet passthrough=no src-address-list=LocalNet
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" disabled=yes \
out-interface=ether1
/ip ipsec peer
add address=100.100.100.100/32 enc-algorithm=aes-128 local-address=\
50.50.50.50 nat-traversal=no secret=1234
/ip ipsec policy
add dst-address=100.100.100.100/32 sa-dst-address=100.100.100.100 \
sa-src-address=50.50.50.50 src-address=50.50.50.50/32
/ip route
add distance=1 gateway=172.16.255.10 routing-mark=inet
add distance=5 gateway=50.50.50.1
/routing rip interface
add interface=gre-mk2-mk1 send=v1-2
/routing rip neighbor
add address=172.16.255.10
/routing rip network
add network=192.168.222.0/24
/system clock
set time-zone-name=Asia/Yekaterinburg
/tool mac-server
set [ find default=yes ] disabled=yes
add interface=ether2-master
/tool mac-server mac-winbox
set [ find default=yes ] disabled=yes
add interface=ether2-masterDidn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question