Answer the question
In order to leave comments, you need to log in
Is it really necessary to have two DMZs (theory)?
Good afternoon. At the moment I delve into the technology of ME.
The essence of the question is this
: resources are external (DMZ) and internal, it is necessary to protect each from external intruders and, accordingly, from internal ones.
Studying the theory on the Internet, I found out that there can be either one or 2 DMZs.
Example 1. One DMZ zone: 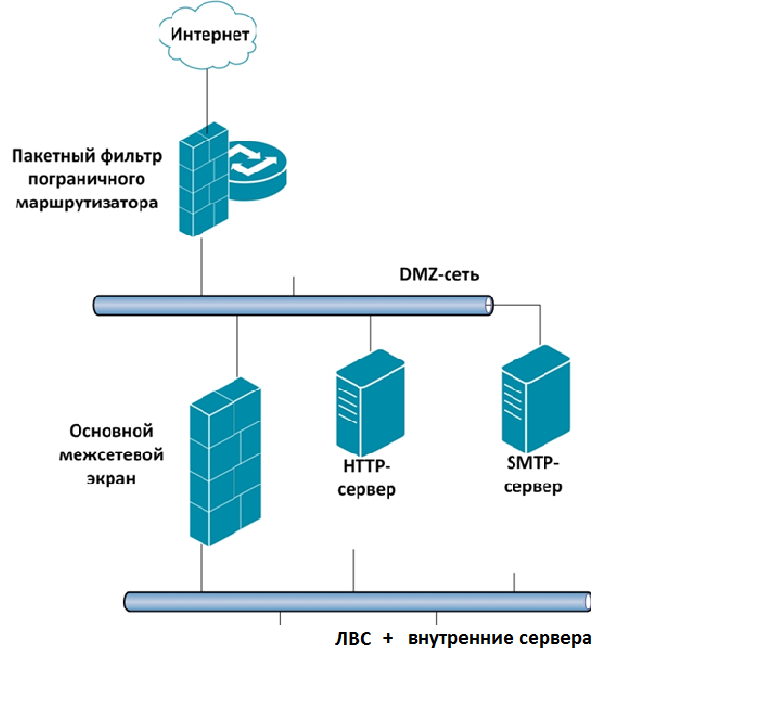
All incoming traffic is filtered by a banal (fast) packet filter.
Further, the DMZ network is connected to the main ME (with filter function with connection tracking, URL filtering, IPS and other hardware ME goodies).
Here, the protection of external resources is understandable, but the protection of internal servers is what happens if they are combined into 1 segment.
Example 2: Two DMZs: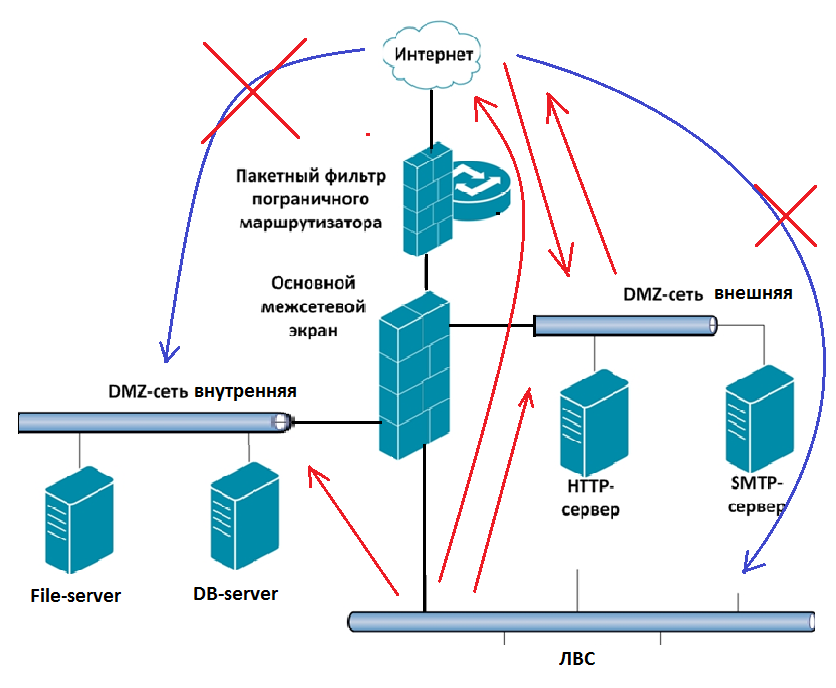
Here it is already more clear, there are 2 zones (internal and external), red arrows - where traffic is allowed, blue - prohibited.
Actually, the questions themselves:
1. Why is 1 DMZ zone indicated in theory, although it is necessary to protect internal and external resources?
2. In cases where two zones are indicated, then each zone has its own (separate) ME. Isn't it possible to get by with one (as shown in example 2).
Dear professionals, I hope for your help. Thank you.
Answer the question
In order to leave comments, you need to log in
In your last drawing, in fact, not 2 DMZs and a LAN, but 3 LAN segments going through 2 firewalls, possibly with different Internet access rights.
DMZ - correctly depicted in the first figure.
DMZ is relevant for attacks from outside. If you need to restrict access to certain servers within the LAN, then no one bothers you to separate them into a separate network and protect them with your firewall. But this is no longer a DMZ, but simply a closed segment of the internal network. Within your network, you can fence any garden you like. Whether you want to separate networks, or not, you want to protect with a firewall, etc. The main thing is not to forget to prescribe routes.
I would say that there may not just be 2 DMZs or more, but in general the concept of DMZ is gradually becoming obsolete. In modern ITU practice, filters are increasingly configured individually for each server in the form of a centrally administered policy, and for user hosts virtual point-to-point connections with authorization, encryption and access policies are generally used + system-level filtering tools are used. Those. in fact, each host can be considered as a separate zone from the point of view of shielding. Moreover, filtering inside the host can be not only by network addresses and ports, but also by applications and users, i.e. the boundary of the security zone in terms of screening may not even be at the host level, but at the level of an individual application or user.
1. Proceeding from the name DMZ - a zone without strict control for external traffic. From the point of view of the external ITU, this area is equivalent to the external network, i.e. maximum severity. Since the DMZ and LAN need to be protected in different ways, they are indicated separately.
2. The topology with one ITU screen for DMZ and LAN is specified in the wiki (a router with external channels may not filter traffic at all).
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question