Answer the question
In order to leave comments, you need to log in
Iptables: could you see the rules?
Good afternoon. I work as a programmer (backend), but I also want to develop in the direction of administration and try to understand netfilter in Linux in more detail. I used to set up only simple things like open a port on a machine and that's it. And then I decided to try to make a test bench from two virtual machines: a gateway and a client. In general, I'm doing NAT for the first time (I've been sitting for two evenings, redid it several times, but it all seems that I'm doing something wrong, although it works).
Could you look at my iptables rules with an experienced eye and suggest what is superfluous or what is missing?
On the gateway external interface enp0s3 with IP 192.168.88.27
Local grid 10.0.1.0/24
Gateway interface that looks to the local area: enp0s8 with IP10.0.1.1
IP of the local machine that needs to be connected and ports forwarded - 10.0.1.2
I want to forward the external port 192.168.88.27:8080 to the local machine 10.0.1.2:80
In the table filterfor all chains, the DROP
enp0s3 - inet, enp0s8 - local
INPUT policy is:
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A INPUT -m conntrack --ctstate INVALID -j DROP
-A INPUT -i lo -j ACCEPT
-A INPUT -i enp0s8 -j ACCEPT-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -d 10.0.1.2/32 -p tcp -m conntrack --ctstate NEW -m tcp --dport 80 -j ACCEPT
-A FORWARD -i enp0s8 -o enp0s3 -j ACCEPT
-A FORWARD -i enp0s8 -o lo -j ACCEPT-A OUTPUT -o enp0s3 -j ACCEPT
-A OUTPUT -o lo -j ACCEPT
-A OUTPUT -o enp0s8 -j ACCEPTnat(all policies ACCEPT) -A PREROUTING -d 192.168.88.27/32 -p tcp -m tcp --dport 8080 -j DNAT --to-destination 10.0.1.2:80-A OUTPUT -d 192.168.88.27/32 -p tcp -m tcp --dport 8080 -j DNAT --to-destination 10.0.1.2:80-A POSTROUTING -o enp0s3 -j SNAT --to-source 192.168.88.27
-A POSTROUTING -s 10.0.1.0/24 -d 10.0.1.2/32 -p tcp -m tcp --dport 80 -j SNAT --to-source 10.0.1.1
# Либо только:
# -A POSTROUTING -s 10.0.1.0/24 -j MASQUERADE# filter
-A FORWARD -d 10.0.1.2/32 -p tcp -m conntrack --ctstate NEW -m tcp --dport 80 -j ACCEPT
# nat
-A PREROUTING -d 192.168.88.27/32 -p tcp -m tcp --dport 8080 -j DNAT --to-destination 10.0.1.2:80
-A OUTPUT -d 192.168.88.27/32 -p tcp -m tcp --dport 8080 -j DNAT --to-destination 10.0.1.2:80
-A POSTROUTING -s 10.0.1.0/24 -d 10.0.1.2/32 -p tcp -m tcp --dport 80 -j SNAT --to-source 10.0.1.1Answer the question
In order to leave comments, you need to log in
Start small, erase all the rules from the Firewall.
1) Allow formard packets on the system between interfaces.
cat /proc/sys/net/ipv4/ip_forward - there should be one (1).
2) 10.0.1.1 must be like GW 10.0.1.2 otherwise traffic must be masqueraded via SNAT.
3) Add a port forwarding rule
-A PREROUTING -i enp0s3 -p tcp -m tcp --dport 8080 -j DNAT --to-destination 10.0.1.2:80
4) Add a masquerade rule to masquerade responses from 10.0.1.2.
-A POSTROUTING -o enp0s3 -j MASQUERADE
Once you have a working minimum, you can add the rest of the rules.
P.S. Outgoing traffic (OUTPUT) is filtered by paranoids)
A good picture for understanding how iptables works
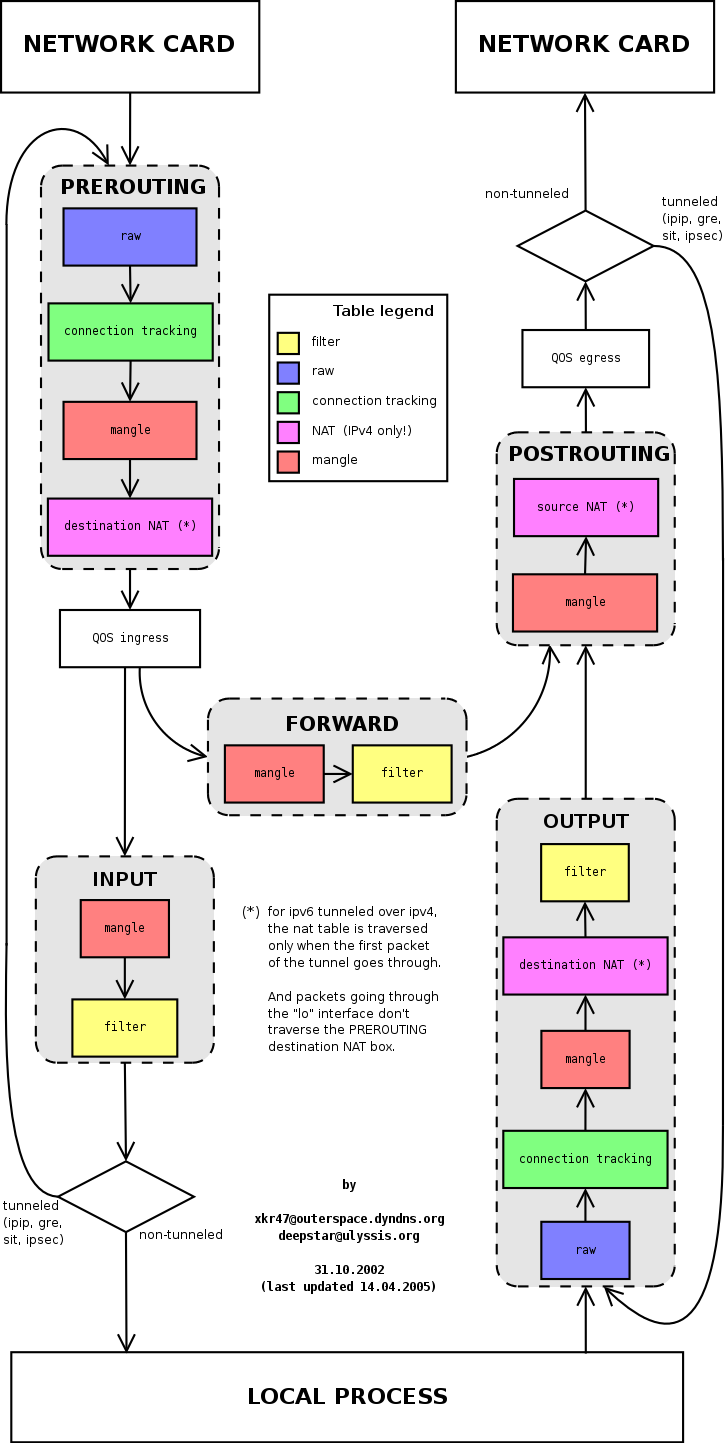
it turns out I added as many as 4 rules:
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question