Answer the question
In order to leave comments, you need to log in
How to set up Mikrotik to pass from VPN to LAN?
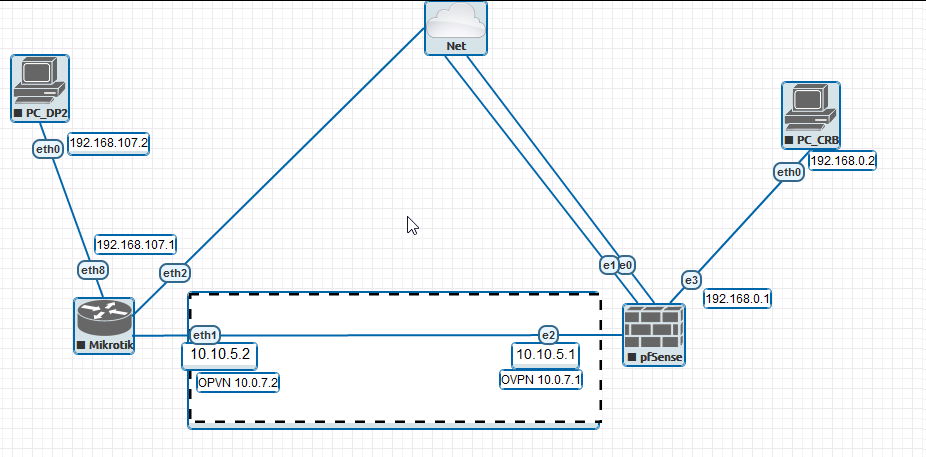
I am connecting two offices in eve-ng. On the one hand, PFSense looks at the Internet, on the other hand, Mikrotik looks at the Internet.
PC_DP2(192.168.107.2)-->(192.168.107.1)Mikrotick(10.10.5.2)<------->(10.10.5.1)PFSense(192.168.0.1)-->(192.168.0.2)PC_CRB
OVPN tunnel 10.0.7.0
are pinged like this
From PC_DP2 -
ping 192.168.107.1 - OK
ping 10.0.7.2 - OK
From PC_CRB
ping 192.168.0.1 - OK
ping 10.0.7.1 - OK
Mikrotik ping 192.168.0.1 - OK
192.168.107.1 - OK
10.0. 7.1 - OK
10.0.7.2 - OK
PFSENSE ping 10.0.7.1 and 10.0.7.2 OK
Mikrotik config is like this
> /export hide-sensitive
# jun/21/2020 15:41:28 by RouterOS 6.45.9
# software id =
#
#
#
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/interface ovpn-client
add certificate=mikrotik.p12_0 cipher=aes256 connect-to=10.10.5.1 mac-addres
02:E8:33:CB:A1:B2 name=ovpn profile=default-encryption user=any
/ip address
add address=192.168.5.151/24 interface=ether2 network=192.168.5.0
add address=192.168.107.1/24 interface=ether8 network=192.168.107.0
add address=10.10.5.2/24 interface=ether1 network=10.10.5.0
/ip dhcp-client
add disabled=no interface=ether1
>
Answer the question
In order to leave comments, you need to log in
routes are registered to subnets? if so, review the rules on the screen again.
It is necessary to prescribe routes on both sides, I won’t tell you for pfSense, unfortunately, I almost never dealt with it, but on microte you create a Dst route. Address - 192.168.0.0/24, Gateway - 10.0.7.1, Pref. Source - 192.168.107.1. You can also add a masquerading rule to NAT: Chain - srcnat, Src. Address - 192.168.107.0/24, Dst. Address - 192.168.0.0/24, Out. Interface - YOUR_OVPN_TUNNEL, Action - masquerade. This way you can access from the network behind the microtome to the network behind pfSense without creating a route on pfSense. This is useful when you do not want back access from the branch network to yours. In your example, the route in pfSense is required, I think it is done by analogy.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question