Answer the question
In order to leave comments, you need to log in
How to set up an ip-camera that sits in the subnet of the router after the debian8 server?
I am a happy owner of a debian8 server, set up iptables with grief in half, (probably postrouting) everything seems to work, but one of the subscribers wanted an ip-camera, and now I can’t figure out how to “forward” the port on the server and router or create a separate NAT. Due to my inexperience in the matter and the lack of time to study the issue, I ask you to help me or send me a link where there is some info for people like me. Thank you
Answer the question
In order to leave comments, you need to log in
I recommend using an iptables add-on, such as ferm, for starters. It is very accessible and understandable allows you to write and apply the rules.
Just write rules in /etc/ferm/ferm.conf and apply them with
sudo ferm /etc/ferm/ferm.conf
There is also a revert option
--interactive
Apply the firewall rules and ask the user for confirmation. Reverts to the previous ruleset if there is no valid user response within 30 seconds (see --timeout). This is useful
for remote firewall administration: you can test the rules without fearing to lock yourself out.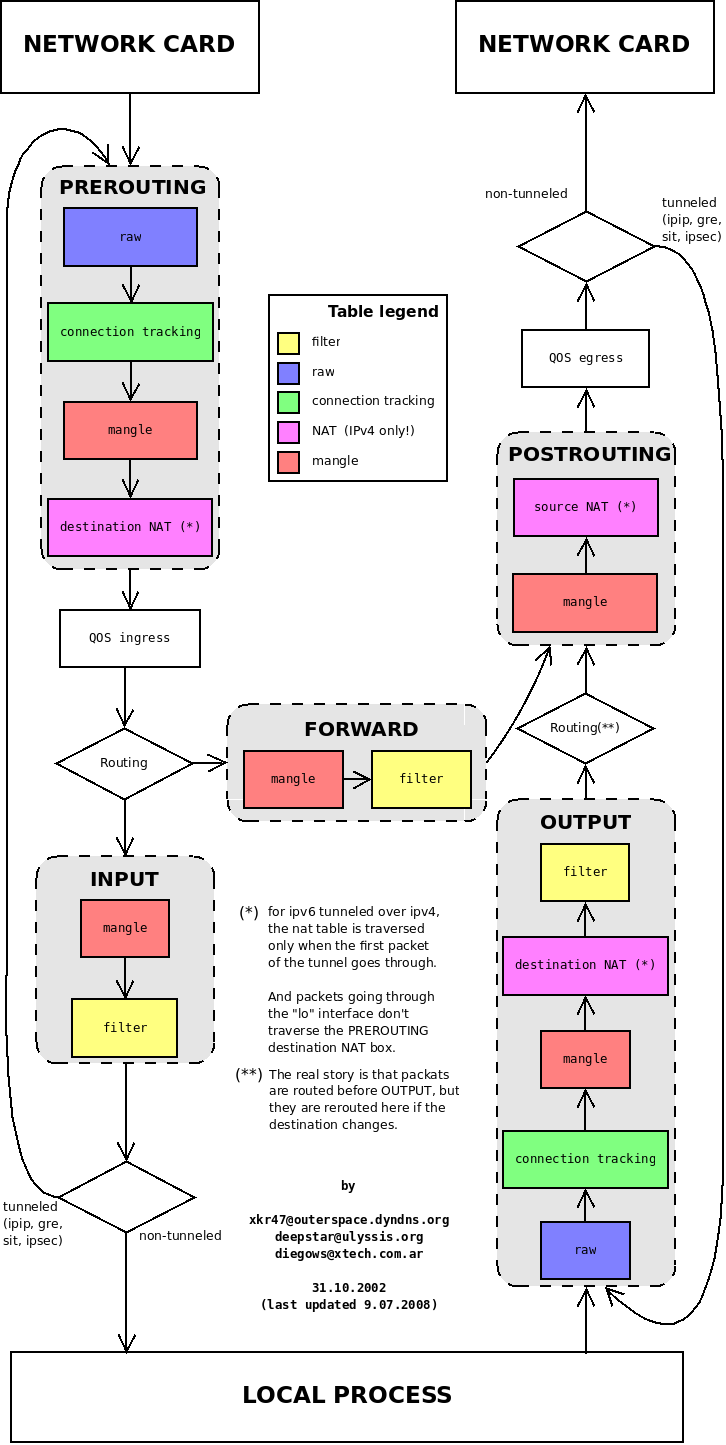
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question