Answer the question
In order to leave comments, you need to log in
How to repel a ddos attack on a website (server)?
More than 1000 requests per second on the server status 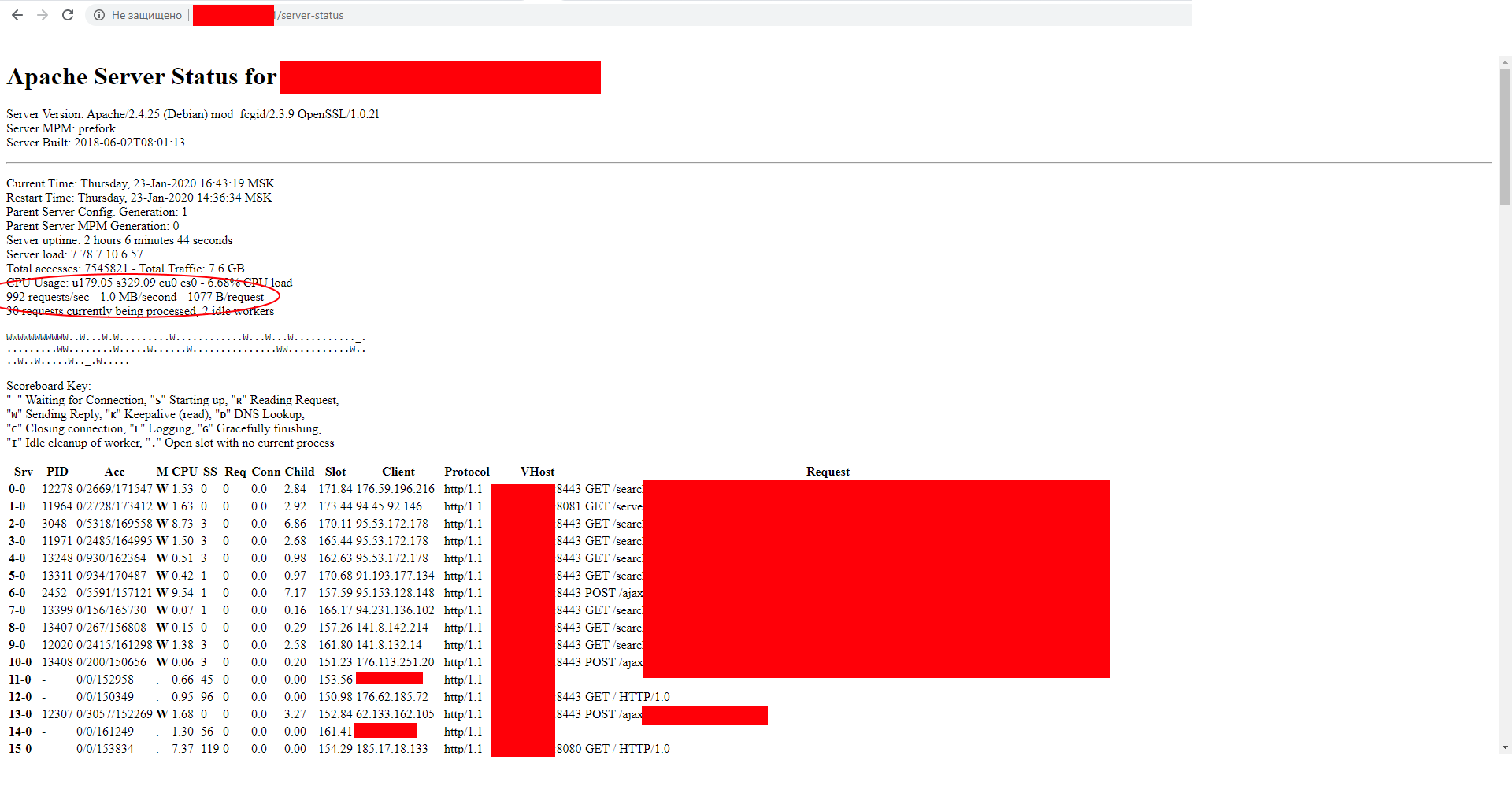
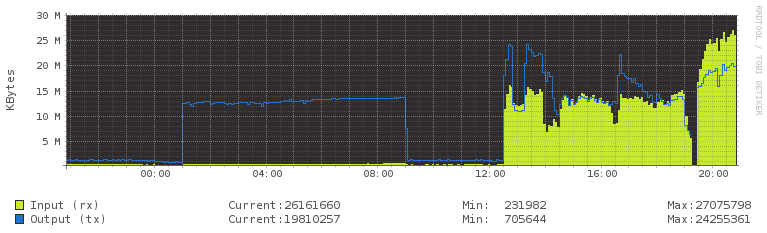
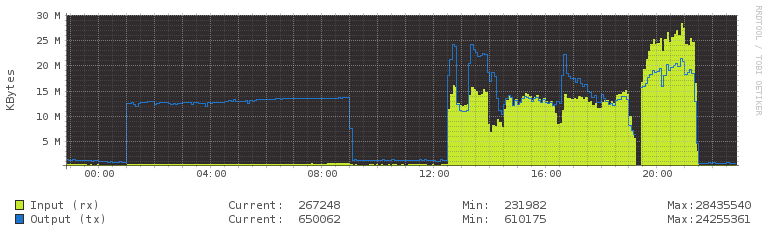
Screen from VestaCP 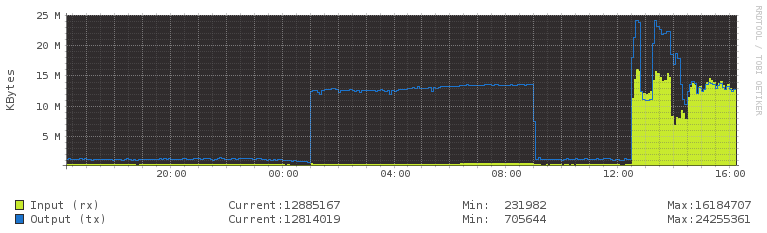
The server can not cope. I tried checking ip addresses for unnecessary countries and adding them to iptable like this: the iptables -I INPUT -s 172.69.186.0/24 -j DROP
server came to life a little, but the brakes are still terrible.
As far as I can see on the server status, the attack goes to the main page of the site.
Already blocked it in nginx, but server-status still shows more than 1000 connections per second.
location = / {
deny all;
}
Answer the question
In order to leave comments, you need to log in
You can get confused with fail2ban, for example, you can hide behind Cloudflare.
ip addresses from which they are hammered, different? If there are not many of them, can you limit, for example, 3 requests per second from one ip,
is your resource international or local? you can limit yourself to only the necessary regions
if ddos is going on, you need to look at what kind of traffic, if packets that are not a priori interesting to the server, just block them
Hello, I used to do protection through the nginx + Lua module, but this is a more complex implementation of the testcookie module without constant inclusion (only during an attack) and with heuristic checks.
By the way, most DDoS defenders do the same for big money.
I also advise you to use ipset for faster blocking of bots through one rule.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question