Answer the question
In order to leave comments, you need to log in
How to raise a gre tunnel between two mikrotiks?
Good day!
Please help in solving the problem, there are two Mikrotik rb-750, they are in different offices, configured the same way, each has two Internet and one local area network.
Lokalka on both mikrotiks works through the 1st port of
the Internet through the 2nd and 3rd ports,
nat masqrade masquerade is configured on both mikrotiks.
There are guarded objects on which there is equipment that sends packets via tcp port 3058 to white static addresses of the 1st microtic, the packets arrive at the firewall router configured so that it passes them through, port 3058 is configured to forward through nat to the local host, everything works, everything is fine.
There is also C2000 ethernet equipment, one block is connected to the LAN of the 1st Mirotik, the second block is connected to the LAN of the second Mirotik, these blocks communicate with each other only via udp port 2048, also for this port on both Mikrotiks there is a forwarding to the local host, here is the picture below as it is . 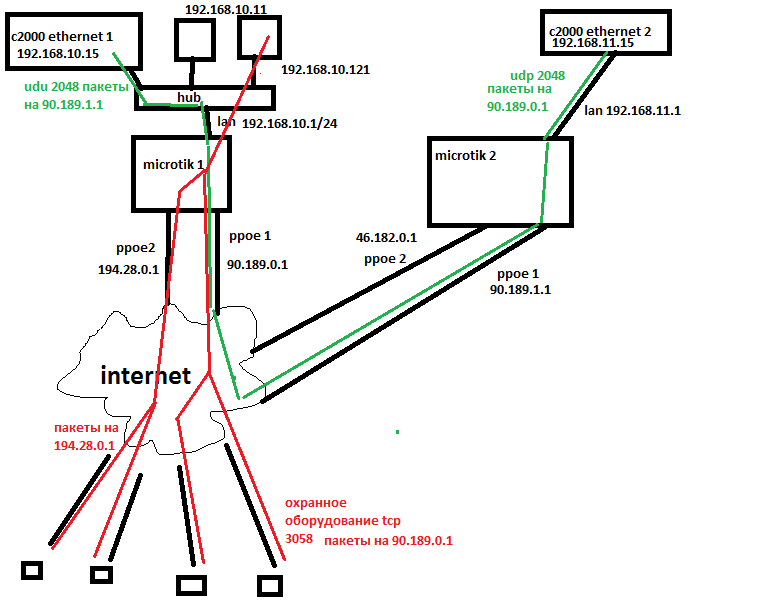
According to this scheme, everything works fine, but it is worth falling off the first ppoe on any microtike and all the basses are karapiziki, there is no connection between the two c2000ehernet. This situation often happens, it was decided to raise two gre tunnels with redundancy, and configure the c2000 equipment to send packets not to a white static address on the Internet, but directly to a remote local area.
To begin with, I made one tunnel, set up routing, and nothing works, but at the same time, the Internet is lost on the first microtic and packets via tcp 3058 either go or not!
Tunnel settings:
1st mikrotik
/interface gre add name=tunnel1 remote-address=90.189.0.1 local-address=192.168.5.1
/ip address
add address=192.168.5.1/30 interface=tunnel1
/ip route
add dst-address=192.168. 11.0/24 gateway=192.168.5.2
2nd mikrotik
/interface gre add name=tunnel1 remote-address =90.189.1.1 local-address=192.168.5.2
/ip address
add address=192.168.5.2/30 interface=tunnel1
/ip route
add dst -address=192.168.10.0/24 gateway=192.168.5.1
on the 1st c2000ethernet we configure to send packets to 192.168.11.15 the microtire gateway 192.168.10.1
on the 2nd c2000ethernet we configure to send packets to 192.168.10.15 the mikrotik gateway
192.168.11.1 the second one does not work, I tried to replace the gateway in the c2000 ethernet settings with the virtual address of the mikrotik, it does not work either! Kind people help me please, what did you do wrong?
Here are the firewall and nat settings of the first Mikrotik on the second everything is the same:
/ip firewall nat
add action=masquerade chain=srcnat out-interface=pppoe-rostelecom
# pppoe-skat not ready
add action=masquerade chain=srcnat out-interface=pppoe- skate
add action=masquerade chain=srcnat out-interface=ether4-intertelecom
# pppoe-skat not ready
add action=netmap chain=dstnat dst-port=3058 in-interface=pppoe-skat \
protocol=tcp to-addresses=192.168.10.253 to-ports=3058
add action=netmap chain=dstnat dst-port=3058 in-interface=pppoe-rostelecom \
protocol=tcp to-addresses=192.168.10.253 to-ports=3058
# pppoe-skat not ready to
add action=netmap chain=dstnat dst-port=3057 in-interface=pppoe-skat \
protocol=tcp to-addresses=192.168.10.254 to-ports=3057
add action=netmap chain=dstnat dst-port=3057 in-interface=pppoe-rostelecom \
protocol=tcp to-addresses=192.168.10.254 to-ports=3057
add action=netmap chain=dstnat dst-port=2048 in-interface=pppoe-rostelecom \
protocol=udp to-addresses=192.168.10.15 to-ports=2048
# pppoe-skat not ready
add action=netmap chain=dstnat dst- port=2048 in-interface=pppoe-skat \
protocol=udp to-addresses=192.168.10.15 to-ports=2048
add action=netmap chain=dstnat dst-port=2048 in-interface=ether4-intertelecom \
protocol=udp to -addresses=192.168.10.15 to-ports=2048
/ip firewall filter
add chain=input dst-port=8291 in-interface=ether1-local protocol=tcp
# pppoe-skat not ready
add chain=input in-interface=pppoe- skat protocol=icmp
# pppoe-skat not ready
add chain=input in-interface=pppoe-skat protocol=!icmp
add chain=input in-interface=pppoe-rostelecom protocol=icmp
add chain=input in-interface=pppoe-rostelecom protocol=!icmp
add chain=input in-interface=ether4-intertelecom protocol=icmp
add chain=input in-interface =ether4-intertelecom protocol=!icmp
add chain=input in-interface=ether1-local protocol=icmp
add chain=input in-interface=ether1-local protocol=!icmp
add chain=input dst-port=1723 protocol=tcp
add chain=input protocol=gre
add action=drop chain=input dst-port=53 protocol=udp
add action=drop chain=input
add chain=forward in-interface=ether1-local protocol=icmp
add chain=forward dst-port= 21 in-interface=ether1-local protocol=tcp
add chain=forward dst-port=22 in-interface=ether1-local protocol=tcp
add chain=forward dst-port=53 in-interface=ether1-local protocol=udp
add chain=forward dst-port=123 in-interface =ether1-local protocol=udp
add chain=forward dst-port=80 in-interface=ether1-local protocol=tcp
add chain=forward dst-port=443 in-interface=ether1-local protocol=tcp
add chain=forward dst -port=5190 in-interface=ether1-local protocol=tcp
add chain=forward dst-port=2048 in-interface=ether1-local protocol=udp \
src-address=192.168.10.15
# no interface
add chain=forward in- interface=*E
# pppoe-skat not ready
add chain=forward dst-port=3057 in-interface=pppoe-skat out-interface=\
ether1-local protocol=tcp
add chain=forward dst-port=3057 in-interface=pppoe-rostelecom out-interface=\
ether1-local protocol=tcp
# pppoe-skat not ready
add chain=forward dst-port=3058 in- interface=pppoe-skat out-interface=\
ether1-local protocol=tcp
add chain=forward dst-port=3058 in-interface=pppoe-rostelecom out-interface=\
ether1-local protocol=tcp
add chain=forward dst-port =10003 in-interface=pppoe-rostelecom out-interface=\
ether1-local protocol=tcp
add chain=forward dst-port=2048 in-interface=pppoe-rostelecom out-interface=\
ether1-local protocol=udp
# pppoe- skat not ready
add chain=forward dst-port=2048 in-interface=pppoe-skat out-interface=\
ether1-local protocol=udp
add chain=forward dst-port=2048 in-interface=ether4-intertelecom \
out-interface=ether1- local protocol=udp
add chain=forward dst-address=89.188.108.102 dst-port=2226 in-interface=\
ether1-local protocol=tcp
add chain=forward dst-address=89.108.73.22 dst-port=2226 in-interface =\
ether1-local protocol=tcp
add chain=forward dst-address=176.119.17.11 dst-port=554,8000 in-interface=\
ether1-local protocol=tcp
add chain=forward connection-state=established,related
add action =drop chain=forward
add action=drop chain=forward comment=social disabled=yes layer7-protocol=\
social src-address-list=192.168.10.238
Answer the question
In order to leave comments, you need to log in
I don't see the accept rules for gre in your firewall.
I guess it would be better to remove the drop rules and set up the tunnel, make sure it works, and only then turn on the firewall.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question