Answer the question
In order to leave comments, you need to log in
How to protect Mikrotik from external pptp, ipsec searches?
Good day, recently in the logs of Mikrotik there are records of unsuccessful authentication attempts using the pptp, ipsec protocols. There are not so many of them, but somehow I don’t like all this, tell me how to correctly make protection from such busts with blacklist. If possible, then a link to the manual is accessible and understandable for self-taught beginners in mikrotik.
Or would you advise not to pay attention to such entries in the logs at all? 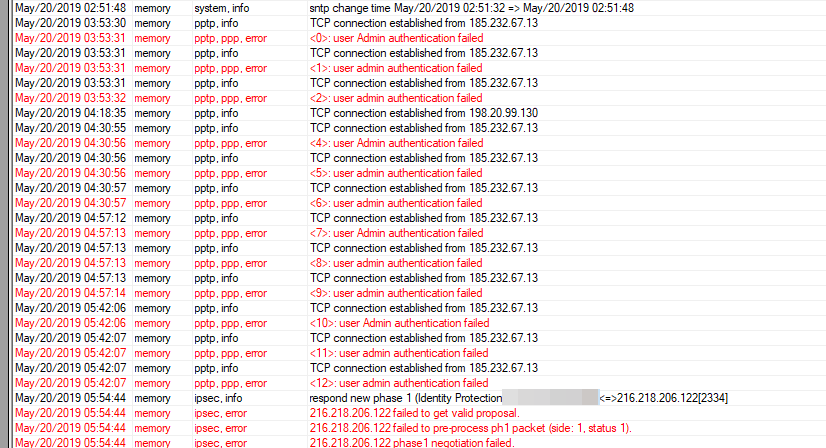
Many thanks in advance.
Answer the question
In order to leave comments, you need to log in
1. DO NOT use PPTP
2. Do not use PSK in IPSec, use only certificates issued in a given CA - even if they swell from enumeration
Georgy Izmailov Nevertheless, I would refuse pptp, if of course it is possible.
Setting up l2tp+ipsec is not that hard.
But in any of the options, you can block many things.
Make any popular port a trap, the main thing is that it would not intersect with workers.
For example, I have routers that only distribute the Internet and they do not have open ports at all.
I set the trap ports to 80,22,443,3389,5080 and whatever else you want.
If there are requests for these ports, then the request is blacklisted and requests from these ports are blocked for a certain time. I have everything going to one database and I do further processing there on more complex conditions.
For VPN, there are several additional options, this is to check the number of authorizations
here is an example for l2tp
https://hd.zp.ua/zashhita-routera-mikrotik-ot-brut...
and there are different options for
pptp
spvd.ru/page/mikrotik-simple-bruteforce-prevention
I use pptp, then I suggest looking for the rest of the option yourself.
You can implement functionality similar to fail2ban:
https://www.ekzorchik.ru/2018/03/i-disassemble-the...
If conditions allow - at least for IPSec it is worth setting explicit peers (addresses of the other side).
With pptp, this is unlikely to work, you can at least try to go to non-standard ports (if the client software allows), otherwise you should go to something else "on certificates".
If no one advises anything sensible and there are not many addresses, I would block all requests manually from these addresses, or from the /24 ranges
To ensure VPN security, you can suggest
1. Do not use standard logins (and ports, but this does not help much)
2. Use complex passwords
3. Restrict sources from which a connection can be initiated. For example, if you do not expect anyone from China, then block Chinese addresses completely (blacklist policy - everything that is not prohibited is allowed). It is also possible to use the whitelisting policy already recommended here (everything that is not allowed is forbidden).
4. You can use port knocking MikroTik + port knocking
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question