Answer the question
In order to leave comments, you need to log in
How to properly organize access?
Good afternoon community!
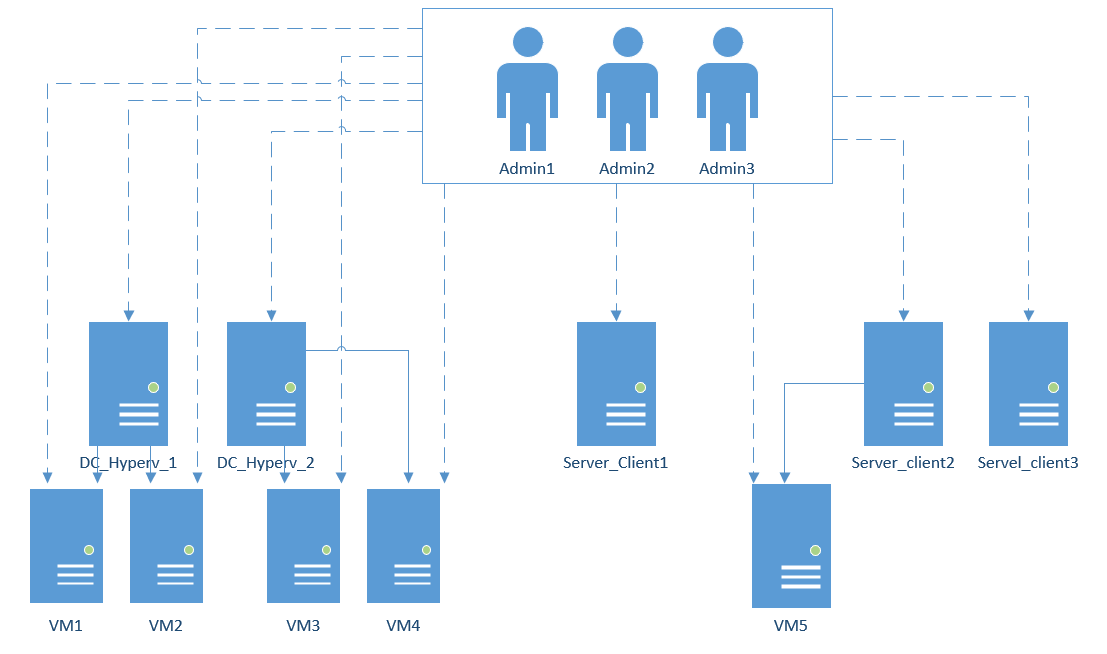
There are three system administrators. Several servers in the data center (DC) on which virtual machines are spinning, several client servers. All servers on Windows Server from 08 to 19. Where there is an Active Directory, where there is not.
How to properly organize access for administrators?
Now everyone has one login and password, I think that it’s wrong to do this, because. then you can’t find out who broke what and who to kick.
The option for everyone to make their own login and password is also very slippery, because. If a person leaves, then all accounts must be turned off.
A small diagram to visualize the issue.
Answer the question
In order to leave comments, you need to log in
Make a terminal. Set up accounts for 3 admins there.
You configure there accesses to all resources that they should adminit.
Set up ip whitelists for terminal access. (+vpn if necessary) The
admin left his ip is thrown out of the list.
Accordingly, all client servers are allowed to administer only from this terminal.
What do you actually want? Well, make three anonymous accounts - admin1, admin2, admin3 and assign each specific Ivanov, Petrov and Shvartsman. There are no other options here, except for: one account for everyone, depersonalized accounts for everyone, personal accounts for everyone.
Without a centralized accounting system, you all end up in the routine administration of administrator accounts anyway.
Alternatively, select a separate server that will be used for administration.
From the side of administrators accounts.
There are three system administrators
The option for everyone to make their own login and password is also very slippery, because. If a person leaves, then all accounts must be turned off.
Each admin has his own account.
If the administrator leaves, in AD you change the password / block the account. On machines outside the domain, access should be limited via rdp only from a specific machine, which in turn is in the domain. Direct access with administrator rights to databases only from the local host or from a special machine for management, without rights (read only, write to allowed tables/bases) from any machine.
You have windows everywhere, why not everything in the domain?
Individual accounts, centralized account management. On your scale, the option with ansible and text files with administrator accounts is suitable
You don't have to reinvent the wheel.
Cheap, Convenient and Safe in one bottle does not happen.
There is a domain, so everyone should have their own account. Not convenient is not an argument.
And raise a two-factor with reference to a corporate number? The person leaves - block the SIM card, switch the number to a new one? Or with reference to corporate mail?
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question