Answer the question
In order to leave comments, you need to log in
How to perform sql injection in this case?
Good afternoon. I train in attacks and defense (the first steps towards web defense). I'm trying to get information from the forum server of some small GTA 5 server. I am working on this article. There are a number of questions that bother me and put me in a stupor:
In the terminal, part of the query is displayed in green, does this mean that this sql has been successfully launched on the server? If so, then it works very strange for me - I had to stick 2 select and starting with an asterisk => * the request starts to be processed for some reason, if I remove it or put something else there - the green part of the code disappears, but in any case I I get status 200. However, there is also a nuance here - the result of my selection is 0 records, you can see it in the screenshot ( counter: 0 ). And even if I write a query that is normal in my opinion, that is, like this:
https://forum.gtavrp.ru/index.php?whats-new/posts/-1%20UNION%20SELECT%20title%20FROM%20posts%20WHERE%20id=1%20--%20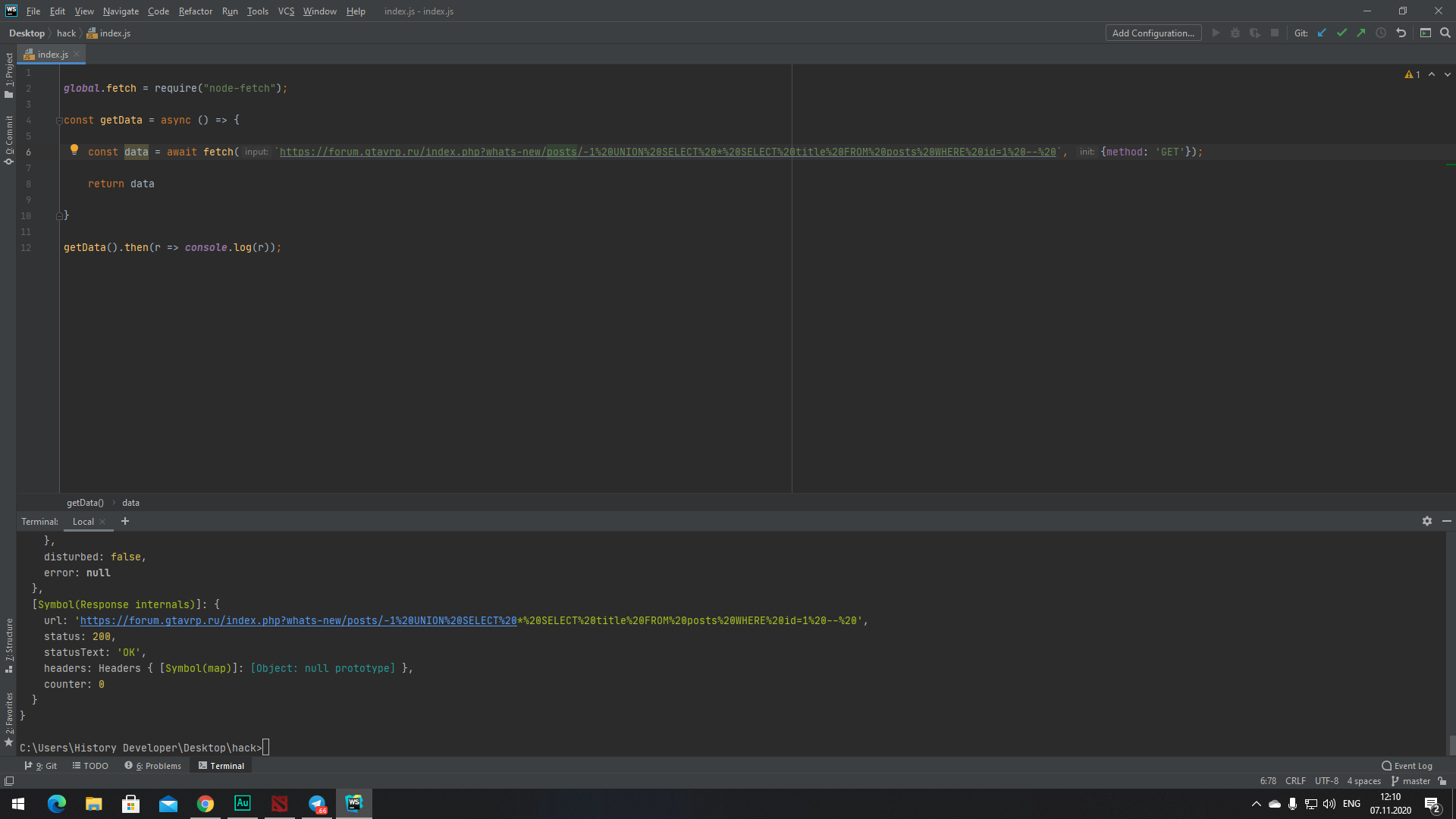
Answer the question
In order to leave comments, you need to log in
To protect against SQL injection, you do not need to train in attacks.
Protection consists of very simple rules that are very easy to follow.
This is what you need to do. If you are really interested in "the first steps towards web protection".
If you are interested in "I want to attack the admins of this site!!! 111", then no, you came to the wrong address here.
And no, "green discharge" means nothing at all, and your ideas about injections are very far from reality.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question