Answer the question
In order to leave comments, you need to log in
How to let all traffic on Ubuntu server through VPN?
Good day, I ask for help with advice, how can I implement the circuit as I drew below?
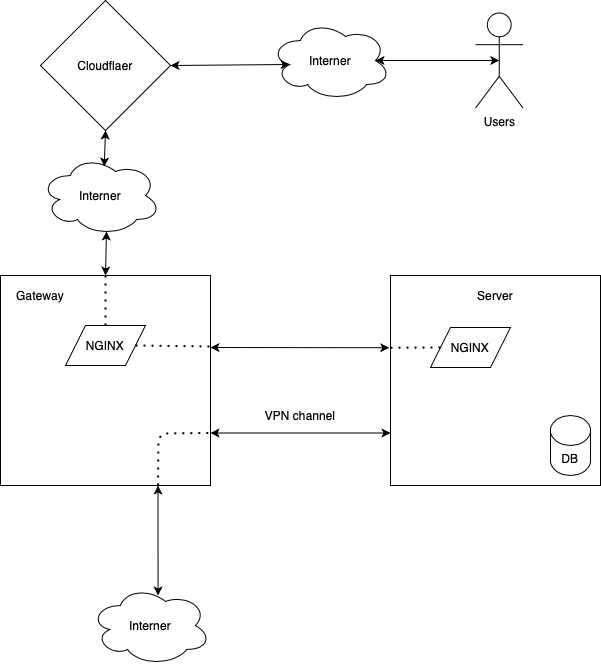
It is necessary to close the main server with a gateway.
If I can redirect incoming requests to the main server in nginx from the gateway also through nginx, then I have a problem with the VPN setup...
I installed and configured OpenVpn on the gateway according to this article
Then I try to connect the main server as a client with this command :
openvpn --config client1.ovpn
Through Tunnelblick everything works correctly.
After I have these messages, a pause without the ability to enter any command in the terminal and I exit the terminal.
Fri Nov 13 14:19:43 2020 OpenVPN 2.4.4 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on May 14 2019
Fri Nov 13 14:19:43 2020 library versions: OpenSSL 1.1.1 11 Sep 2018, LZO 2.08
Fri Nov 13 14:19:43 2020 Outgoing Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication
Fri Nov 13 14:19:43 2020 Incoming Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication
Fri Nov 13 14:19:43 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]{ip_gateway_vpn}:7653
Fri Nov 13 14:19:43 2020 Socket Buffers: R=[212992->212992] S=[212992->212992]
Fri Nov 13 14:19:43 2020 UDP link local: (not bound)
Fri Nov 13 14:19:43 2020 UDP link remote: [AF_INET]{ip_gateway_vpn}:7653
Fri Nov 13 14:19:43 2020 NOTE: UID/GID downgrade will be delayed because of --client, --pull, or --up-delay
Fri Nov 13 14:19:43 2020 TLS: Initial packet from [AF_INET]{ip_gateway_vpn}:7653, sid=2c36f517 9738c2a0
Fri Nov 13 14:19:43 2020 VERIFY OK: depth=1, CN=Easy-RSA CA
Fri Nov 13 14:19:43 2020 VERIFY KU OK
Fri Nov 13 14:19:43 2020 Validating certificate extended key usage
Fri Nov 13 14:19:43 2020 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Fri Nov 13 14:19:43 2020 VERIFY EKU OK
Fri Nov 13 14:19:43 2020 VERIFY OK: depth=0, CN=server
Fri Nov 13 14:19:43 2020 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, 2048 bit RSA
Fri Nov 13 14:19:43 2020 [server] Peer Connection Initiated with [AF_INET]{ip_gateway_vpn}:7653
Fri Nov 13 14:19:44 2020 SENT CONTROL [server]: 'PUSH_REQUEST' (status=1)
Fri Nov 13 14:19:44 2020 PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1 bypass-dhcp,dhcp-option DNS 208.67.222.222,dhcp-option DNS 208.67.220.220,route 10.8.0.1,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.6 10.8.0.5,peer-id 0,cipher AES-256-GCM'
Fri Nov 13 14:19:44 2020 OPTIONS IMPORT: timers and/or timeouts modified
Fri Nov 13 14:19:44 2020 OPTIONS IMPORT: --ifconfig/up options modified
Fri Nov 13 14:19:44 2020 OPTIONS IMPORT: route options modified
client_loop: send disconnect: Broken pipeAnswer the question
In order to leave comments, you need to log in
Fri Nov 13 14:19:44 2020 OPTIONS IMPORT: route options modified
client_loop: send disconnect: Broken pipeDidn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question