Answer the question
In order to leave comments, you need to log in
How to integrate authentication for Sharepoint 2013 from an ASP.NET MVC 5 site with ASP.NET Identity 2?
Given : there are a bunch of ASP.NET MVC 5 sites on the same domain. Authentication happens on one, "main" site, using ASP.NET Identity 2 + Thinktecture Resource Authorization . Because authentication happens in a cookie, and the cookie is available to all subdomains, then authentication happens transparently (via Resource Authorization ). Plus, there is a small API so that users also transparently enter the corporate portal on Bitrix-24.
It is necessary : another site appears - on sharepoint 2013. It is necessary to integrate it into the same authentication system (ASP.NET Idenity 2), even simple authentication without authorization is enough. For starters, even that will do.
Answer the question
In order to leave comments, you need to log in
You can try to look towards Membership provider and Role manager. SP supports the use of third party identity providers, I think Idenity 2 supports everything SP needs.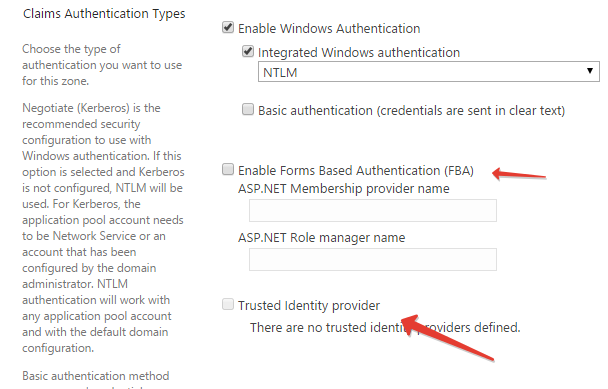
I implemented it like this:
- created a custom view web part
- in the site settings Custom login page specified the address of my view web part
- stuck it in the code-behind, not forgetting to add the machinekey the same as the site that is the SSO provider, the code that pulls the current one Username
private static string GetUserFromCoockie()
{
string username = "";
var request = HttpContext.Current.Request;
var cookie = request.Cookies.Get(".AspNet.ApplicationCookie");
if(cookie == null) { return String.Empty; } //coockie is null!!!
var ticket = cookie.Value;
ticket = ticket.Replace('-', '+').Replace('_', '/');
var padding = 3 - ((ticket.Length + 3) % 4);
if (padding != 0)
ticket = ticket + new string('=', padding);
var bytes = Convert.FromBase64String(ticket);
try {
bytes = System.Web.Security.MachineKey.Unprotect(bytes,
"Microsoft.Owin.Security.Cookies.CookieAuthenticationMiddleware",
"ApplicationCookie", "v1");
}
catch(Exception ex)
{
return String.Empty; //u lost machine key!!! stupid idiot
}
using (var memory = new MemoryStream(bytes))
{
using (var compression = new GZipStream(memory, CompressionMode.Decompress))
{
using (var reader = new BinaryReader(compression))
{
reader.ReadInt32(); // Ignoring version here
string authenticationType = reader.ReadString();
reader.ReadString(); // Ignoring the default name claim type
reader.ReadString(); // Ignoring the default role claim type
int count = reader.ReadInt32(); // count of claims in the ticket
var claims = new Claim[count];
for (int index = 0; index != count; ++index)
{
string type = reader.ReadString();
type = type == "\0" ? ClaimTypes.Name : type;
string value = reader.ReadString();
string valueType = reader.ReadString();
valueType = valueType == "\0"
? "http://www.w3.org/2001/XMLSchema#string"
: valueType;
string issuer = reader.ReadString();
issuer = issuer == "\0" ? "LOCAL AUTHORITY" : issuer;
string originalIssuer = reader.ReadString();
originalIssuer = originalIssuer == "\0" ? issuer : originalIssuer;
claims[index] = new Claim(type, value, valueType, issuer, originalIssuer);
}
var identity = new ClaimsIdentity(claims, authenticationType,
ClaimTypes.Name, ClaimTypes.Role);
username = identity.Name;
}
}
}
return username;
}Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question