Answer the question
In order to leave comments, you need to log in
How to implement reliable IP-telephony in the network?
Hello, dear forum users!
Given:
Mikrotik as the main router with several white ip addresses through which everything works.
Just delivered IP Telephony system CentOS7/Asterisk/Elastix (system unit with 3 eth interfaces).
Task: You need to install one IP phone in a remote area, through a VPN tunnel (L2TP / IPSec).
And install one softphone on the network 10.10.10.0/24
Here I'm breaking my head, I just can't decide how to implement it correctly with security.
So that no one has the opportunity to connect and so that bills for incomprehensible calls do not have to be paid.
According to what scheme to solve the problem, can something else be added to the network, how to organize a reliable vpn? Tell me please!
How would I solve the problem:
I would raise vpn l2tp / ipsec between microns, organize routes in both directions. and would limit access to management as much as possible, which would leave only the passage of a call, even for a local network.
communicating with SMG only with Elastix and also setting complex logins and passwords.
It seems that this approach is not the most reliable. And maybe I don’t know about something, because. first time faced with IP telephony.
Scheme: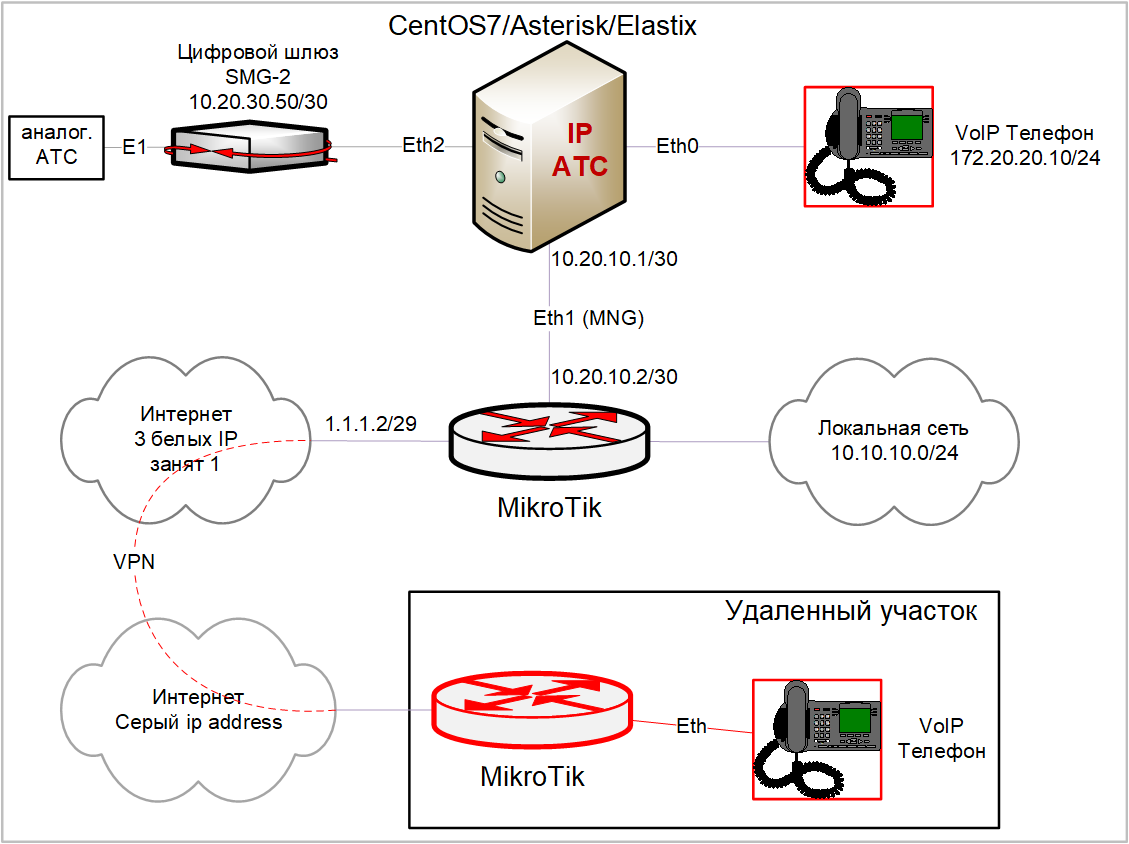
Answer the question
In order to leave comments, you need to log in
Your approach is correct, but what's the point of connecting phones in the office to a separate physical port in Asterisk? Are you using VLANs to separate voice and data traffic?
If you have unmanaged switches where there is no way to cut VLANs, then this approach makes sense.
Concerning difficult logins/passwords - everything is correct.
I didn’t understand only the beginning of the scheme, where do you accept city numbers? If on an analog PBX - then there are no problems, you will still have access to / from the city through an analog PBX. In this case, Asterisk simply acts as an extension of the PBX functionality to the level of "digit in LAN" and you do not receive SIP calls directly from the city.
We turn the "nuts" further. Only SIP traffic can be allowed on the Mikrotik tunnel (allow TCP/UDP 5060). If you do not use SSL, then only UDP / 5060 is possible - this is the standard port for SIP.
Do not forget about the firewall in CentOS itself (it seems to be possible to configure trusted nodes in the Elastix webcam).
So in short, if you do not directly receive SIP from the Internet and your users are in the security perimeter of the local area, then your scheme has a place to "be".
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question