Answer the question
In order to leave comments, you need to log in
How to forward a packet from LAN to LAN device when accessing external IP?
Network for example, any matches are random
WAN (ether1-wan) white IP: 10.10.10.10
Mikrotik address: 192.168.1.254
LAN (bridge-lan): 192.168.1.0/24
VPN+Web server: 192.168.1.100
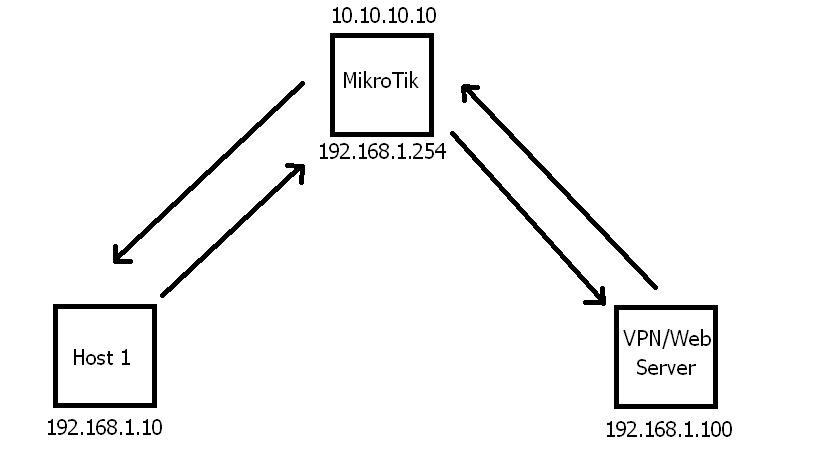
A rule is configured that redirects packets on port 80 and 12345 from the outside (ether1-wan) to the server (192.168.1.100)
/ip firewall nat
add action=netmap chain=dstnat dst-port=80 in-interface=ether1-wan protocol=tcp to-addresses=192.168.1.100 to-ports=80
add action=netmap chain=dstnat dst-port=12345 in-interface=ether1-wan protocol=tcp to-addresses=192.168.1.100 to-ports=12345/ip firewall nat
add action=masquerade chain=srcnat src-address=192.168.1.0/24
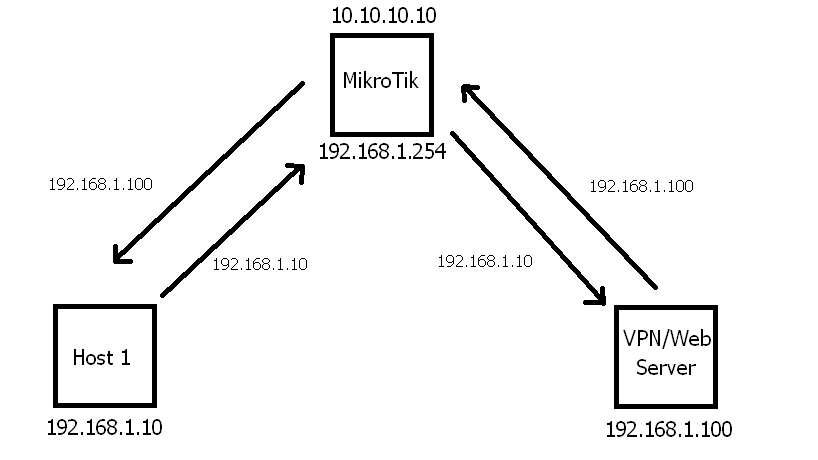
add action=netmap chain=dstnat dst-address=10.10.10.10 dst-port=12345 in-interface=bridge-lan protocol=tcp src-address=192.168.1.0/24 to-addresses=192.168.1.100 to-ports=12345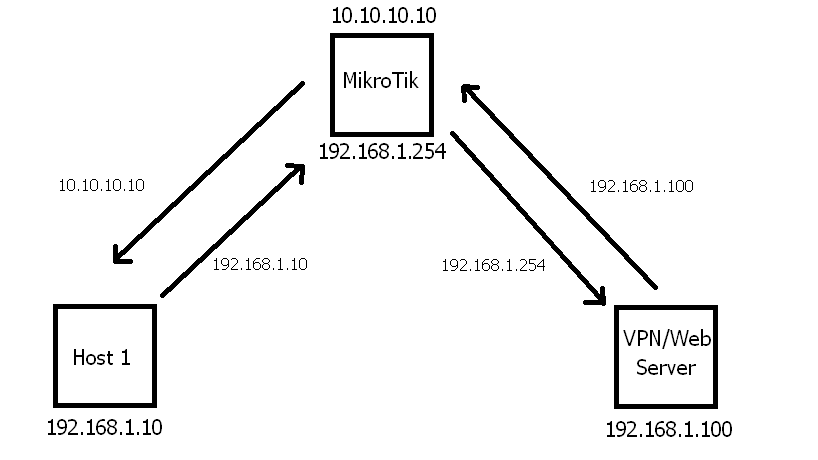
Answer the question
In order to leave comments, you need to log in
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question