Answer the question
In order to leave comments, you need to log in
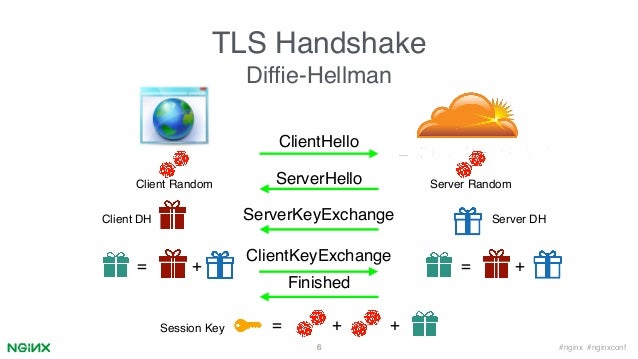
How exactly is the Diffie-Hellman session key obtained in the TLS protocol?
What exactly is accepted as private keys by each party and how is the public key (certificate) of the server used here?
Answer the question
In order to leave comments, you need to log in
1. But it's so easy !
2.TLS _
Algorithms used in TLS
The following algorithms are available in the current version of the protocol:
Combinations of algorithms are used for key exchange and authentication: RSA (asymmetric cipher), Diffie-Hellman (secure key exchange), DSA (digital signature algorithm), ECDSA;
For symmetric encryption: RC4, IDEA, Triple DES, SEED, Camellia or AES;
For hash functions: MD5, SHA, SHA-256/384.
Algorithms can be supplemented depending on the version of the protocol. Prior to the latest version of the TLS 1.2 protocol, the following symmetric encryption algorithms were also available, but they were removed as insecure: RC2, IDEA, DES.
https://tools.ietf.org/html/rfc5246
The server provides its own certificate with the DH parameters written in it, or a chain of certificates with them. As a result of the classical exchange over DH, a pre_master_secret is formed. Then a session symmetric master key is formed from it according to the formula master_secret = PRF(pre_master_secret, "master secret", ClientHello.random + ServerHello.random), which is used for encryption.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question