Answer the question
In order to leave comments, you need to log in
Is the diagram correct?
Good day. I'm doing something like a token to encrypt files. I am doing a project related to cryptography for the first time. Compiled a model (if you can call it that), including the transfer of the key from the token to the PC and the encryption itself. Perhaps I am doing globally wrong things. I would be glad for any comment, advice about the project. Thanks in advance.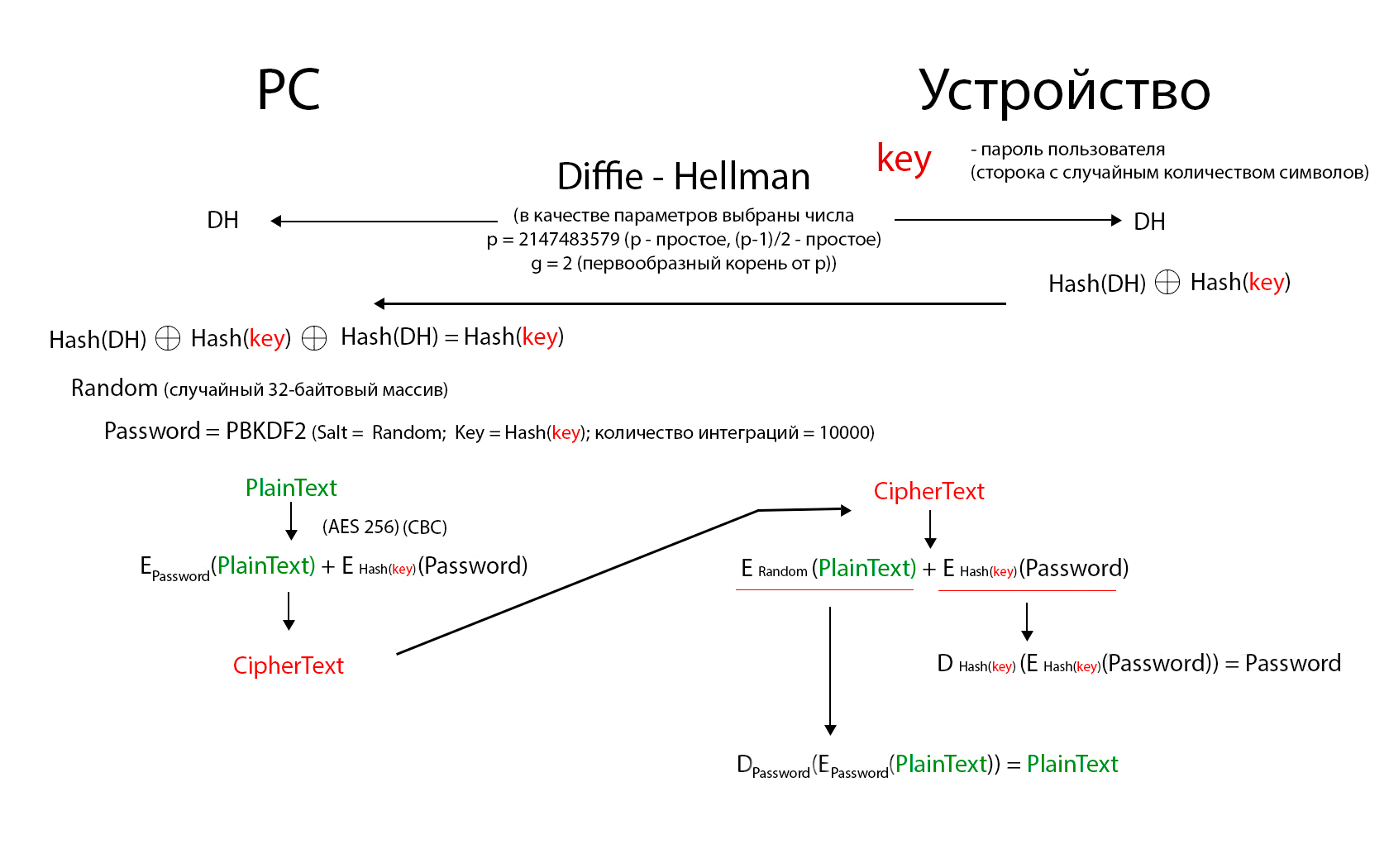
Answer the question
In order to leave comments, you need to log in
The exchange model cannot be verified until you say "Intruder Model". What threats are you protecting yourself from? (Disclosure, substitution, modification without decryption, etc.) Which of the depicted areas do you consider trusted? (Where can an attacker a priori not get?)
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question