Answer the question
In order to leave comments, you need to log in
Distinguish between local network and wifi network without VLAN?
Hello, from hardware I have cisco linksys ea6700wifi and tp-link tl-wr740n.
There is a network tied to the Tp-link tl-r600vpn router, it is a dhcp server, it also gives users an Internet NAT. In the local there are desktop computers that are connected via twisted pair, there are also laptops that are connected via wi-fi. There are also clients of the company who also connect via wi-fi and, accordingly, see the entire network, but should not (DO NOT OFFER GUEST ACCESS). In this regard, the idea arose to replace the working Tp-link tl-r600vpn with cisco linksys ea6700wifi to hide the ssid from wifi and connect those laptops that are employees via Wi-Fi. And what about the firm's clients? and even so that they do not see the local network? I found on the Internet that you can connect the WAN port of the wi-fi router to the LAN port of the router or switch, i.e. in my case tp-link tl-wr740n. connect to linksys ea6700wifi, change the gateway to a different one from the existing network, enable the dhcp server. Will this work?
Simplified diagram for clarity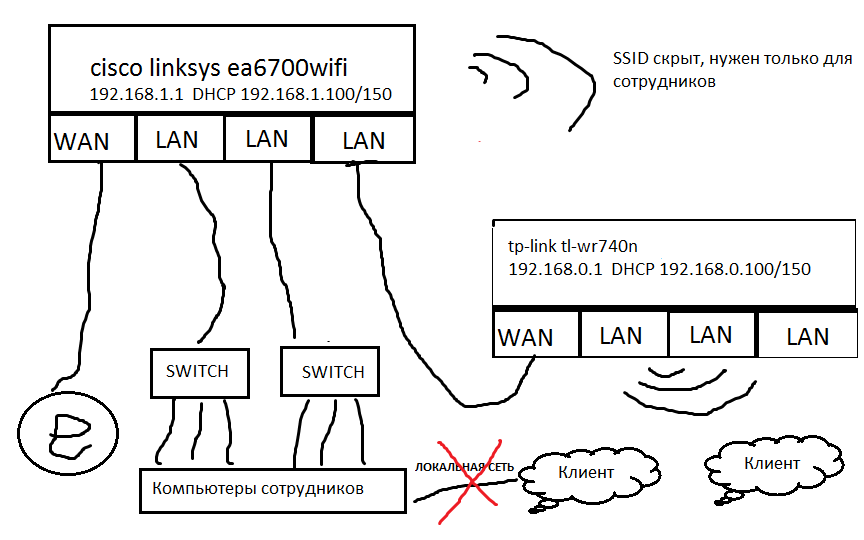
Answer the question
In order to leave comments, you need to log in
The default gateway will enter the network 192.168.1.0/24, and NAT on the TP-LINK TL-WR740n will mask all traffic from the network 192.168.0.0/24to the address 192.168.1.100/150, i.e. it will not work to hide anything in this way and delimit it with a firewall on any device either.
For such a trick to work, the physical part of it should look something like this: 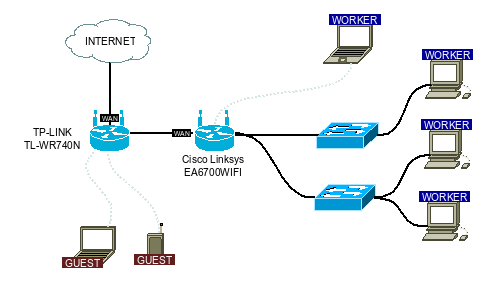
in this option, guests connected to TP-LINK will not have a route to the employee network, and NAT on Linksys will allow employees to see the guest network, but not vice versa.
In general, yes, such a scheme will work, but access to the network 192.168.1.0/24 from the network 192.168.0.0/24 will still be. I think it's easy to burn with the same traceroute.
subnetting by ports should be done: vlans, in order to give access only like this:
internet<->cisco [right LAN]<->TP-LINK
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question