Answer the question
In order to leave comments, you need to log in
Why won't ipsec ubuntu-cisco connect?
ipsec between ubuntu and cisco
communication goes through psk, which is in 94.97.1.132 : PSK KEY
/etc/ipsec.secrets ipsec config on ubuntu:
config setup
charondebug="all"
uniqueids=yes
strictcrlpolicy=no
conn Jump-to-STC
authby=psk
right=159.203.38.79
rightid=159.203.38.79
left=94.97.1.132
leftid=94.97.1.132
leftsubnet=100.64.0.0/16
rightsubnet=172.17.0.0/24
ike=aes256,aes256-sha,aes256-sha1-modp2048-prfsha1,aes256-sha-modp1536-prfsha256,aes128-sha1-modp1536,aes265-sha2_256,aes256-sha2_256-modp1024,aes256-sha-modp1024
esp=aes256-sha,aes256-sha2_256,aes256-sha-modз1536,aes256-sha-prfsha256,aes128-sha1
keyexchange=ikev1
keyexchange=ikev2
rekeymargin=3m
ikelifetime=24h
lifetime=6h
dpddelay=30
dpdtimeout=120
dpdaction=restart
auto=startsudo ipsec up Jump-to-STC
initiating IKE_SA Jump-to-STC[5] to 94.97.1.132
generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(HASH_ALG) ]
sending packet: from 159.203.38.79[500] to 94.97.1.132[500] (1316 bytes)
received packet: from 94.97.1.132[500] to 159.203.38.79[500] (38 bytes)
parsed IKE_SA_INIT response 0 [ N(INVAL_KE) ]
peer didn't accept DH group MODP_2048, it requested MODP_1536
initiating IKE_SA Jump-to-STC[5] to 94.97.1.132
generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(HASH_ALG) ]
sending packet: from 159.203.38.79[500] to 94.97.1.132[500] (1252 bytes)
received packet: from 94.97.1.132[500] to 159.203.38.79[500] (521 bytes)
parsed IKE_SA_INIT response 0 [ SA KE No V V V N(NATD_S_IP) N(NATD_D_IP) V ]
authentication of '159.203.38.79' (myself) with pre-shared key
establishing CHILD_SA Jump-to-STC
generating IKE_AUTH request 1 [ IDi N(INIT_CONTACT) IDr AUTH SA TSi TSr N(MOBIKE_SUP) N(ADD_4_ADDR) N(ADD_4_ADDR) N(EAP_ONLY) ]
sending packet: from 159.203.38.79[4500] to 94.97.1.132[4500] (492 bytes)
retransmit 1 of request with message ID 1
sending packet: from 159.203.38.79[4500] to 94.97.1.132[4500] (492 bytes)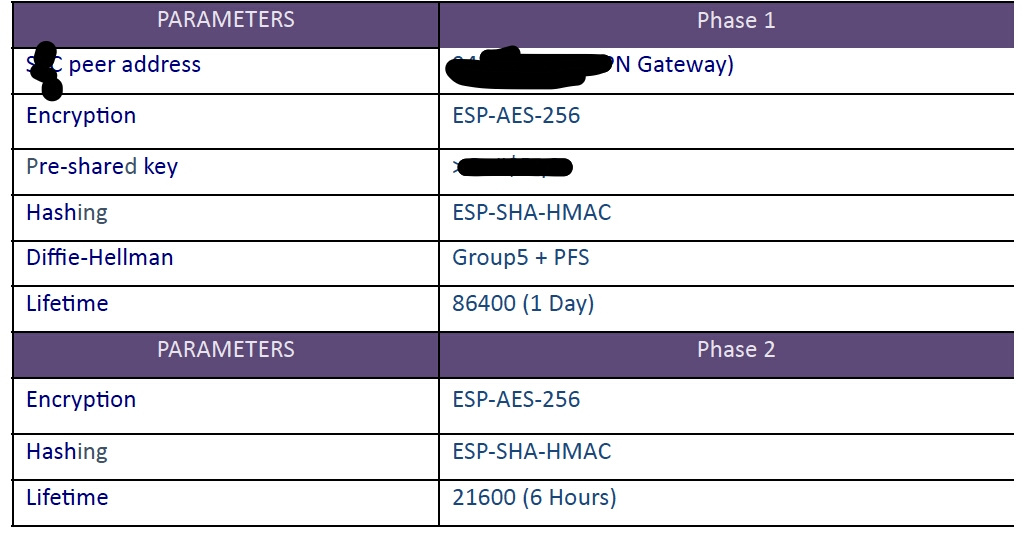
hain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 udp dpt:500
ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 udp dpt:4500
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
MASQUERADE all -- 172.17.0.0/16 0.0.0.0/0
MASQUERADE all -- 172.17.0.0/24 0.0.0.0/0Answer the question
In order to leave comments, you need to log in
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question