Answer the question
In order to leave comments, you need to log in
Why is the DROP rule not working?
Task: create a whitelist of IP addresses that can connect to my VPN. A PPTP server has been set up on Mikrotik, the same Mikrotiks are logging in to it.
I created an adress list in which I added all the ips that I want to give access to. After that, I added the following right to Firewall -> Filter Rules:
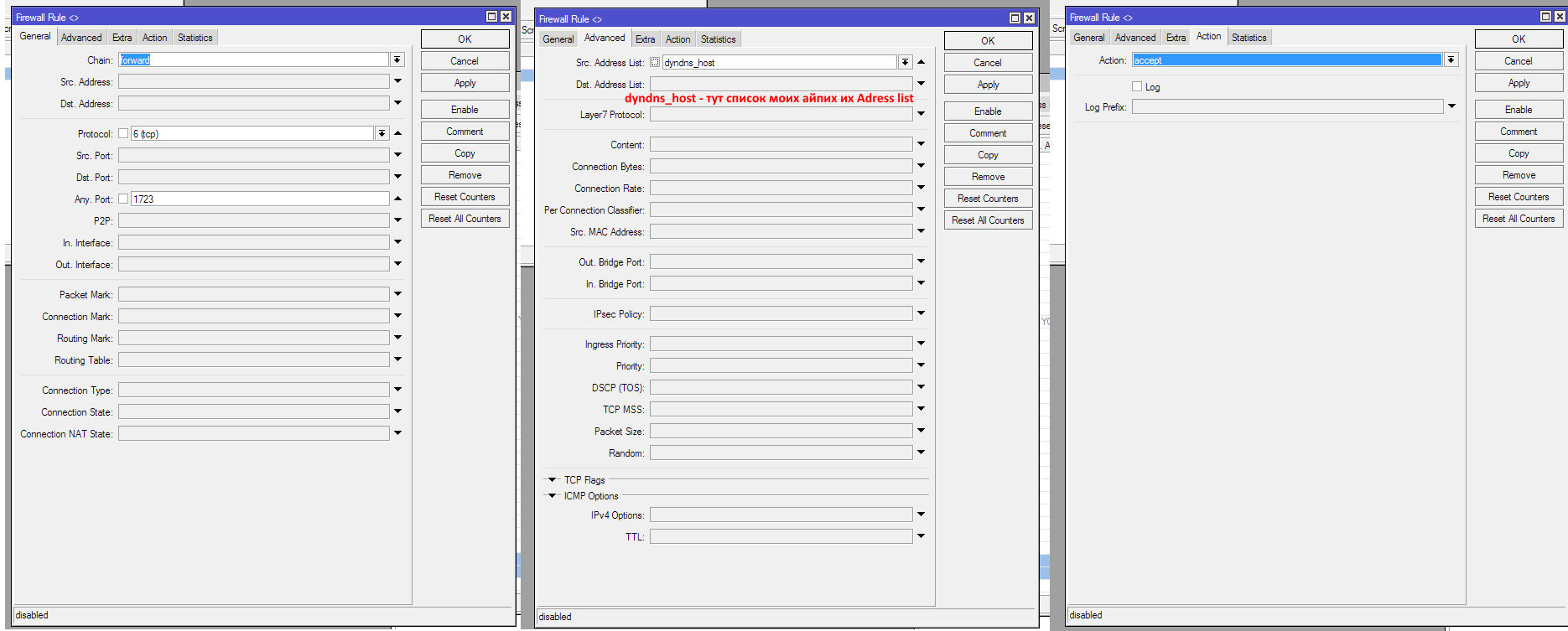
> /ip firewall export
# sep/29/2017 XX:56:52 by RouterOS X.XX.X
# software id = XXX
#
/ip firewall address-list
add address=XXX.XXX.XXX.XXX comment=XXX list=dyndns_host
add address=XXX.XXX.XXX.XXX comment=XXX list=dyndns_host
add address=XXX.XXX.XXX.XXX comment=XXX list=dyndns_host
add address=XXX.XXX.XXX.XXX comment=XXX list=dyndns_host
add address=XXX.XXX.XXX.XXX comment=XXX list=dyndns_host
add address=XXX.XXX.XXX.XXX comment=XXX list=dyndns_host
add address=XXX.XXX.XXX.XXX comment=XXX list=dyndns_host
add address=XXX.XXX.XXX.XXX comment=XXX list=dyndns_host
add address=XXX.XXX.XXX.XXX comment=XXX list=dyndns_host
add address=XXX.XXX.XXX.XXX comment=XXX list=dyndns_host
add address=XXX.XXX.XXX.XXX comment=XXX list=dyndns_host
add address=XXX.XXX.XXX.XXX comment=XXX list=dyndns_host
add address=XXX.XXX.XXX.XXX comment=lXXX list=dyndns_host
add address=XXX.XXX.XXX.XXX comment=XXX list=dyndns_host
add address=XXX.XXX.XXX.XXX comment=XXX list=dyndns_host
add address=XXX.XXX.XXX.XXX comment=XXX list=dyndns_host
add address=XXX.XXX.XXX.XXX comment=XXX list=dyndns_host
add address=XXX.XXX.XXX.XXX comment=XXX list=dyndns_host
add address=XXX.XXX.XXX.XXX comment=XXX list=dyndns_host
add address=XXX.XXX.XXX.XXX comment=XXX list=dyndns_host
/ip firewall filter
add chain=input comment="Accept VPN" port=1723 protocol=tcp src-address-list=dyndns_host
add chain=forward port=1723 protocol=tcp src-address-list=dyndns_host
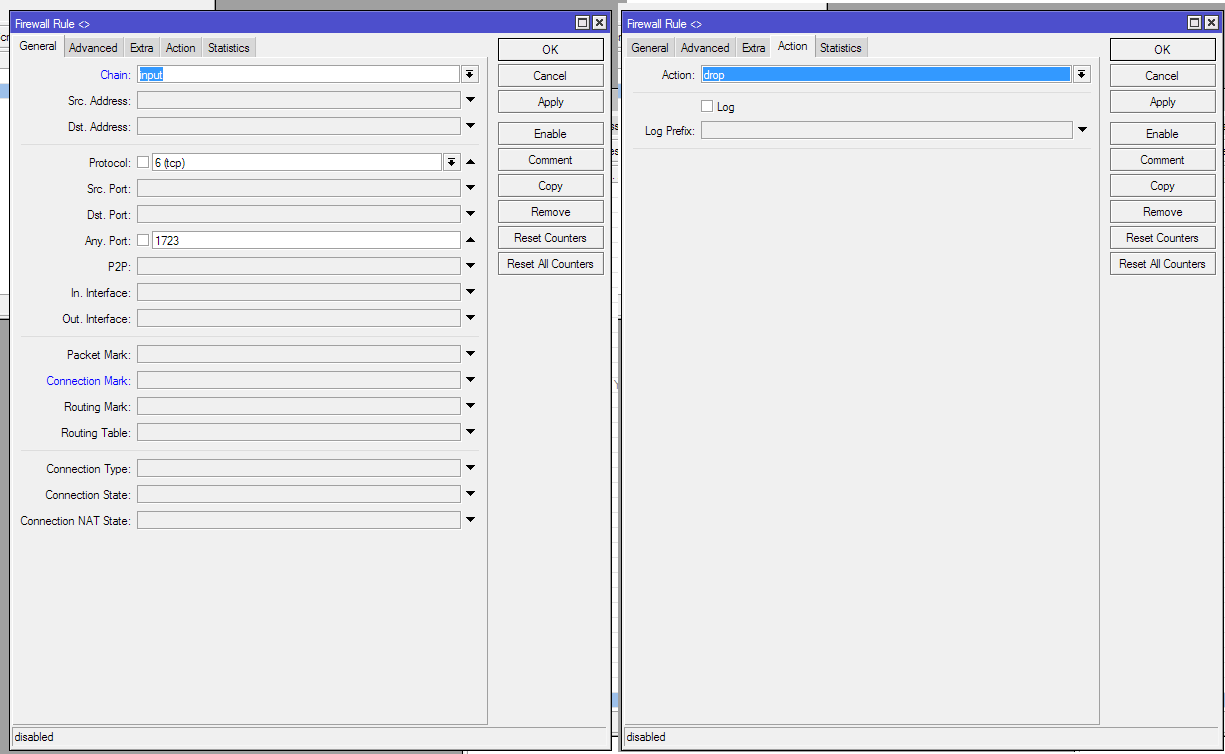
add action=drop chain=input port=1723 protocol=tcp
add action=drop chain=forward port=1723 protocol=tcpAnswer the question
In order to leave comments, you need to log in
To the input drop rule, you still need to do a forward drop.
In general, to drop at the end, you need all the packets that came to the wan interface
ZY . If the user has already connected to you, then after removing him from the address list, you still need to drop his connection to ip firewall connections.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question