Answer the question
In order to leave comments, you need to log in
Why does the site randomly change ssl certificates?
Good afternoon.
For the sake of interest, I decided to check if my computer could have been attacked by means of a mitm attack, since there is a suspicion that the root certificate could have been changed on the PC and, accordingly, the attacker gives me self-signed ones.
I found a convenient service for checking certificates: https://lospi.net/snuckme/
I decided to use google.com for the test. I entered the site address and got the following result:
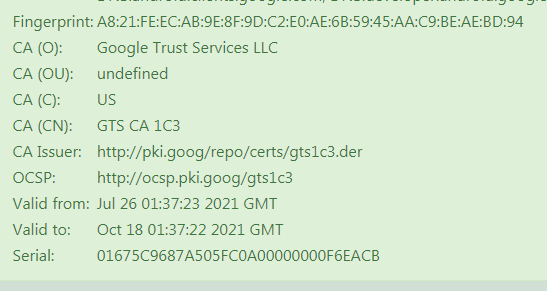
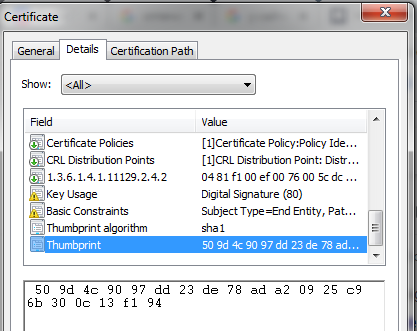
After that, I opened chrome and decided to check the validity. As a result, I found a different finger print.
I returned again to the site for verification, requested the certificate again, as a result, I received the third certificate:
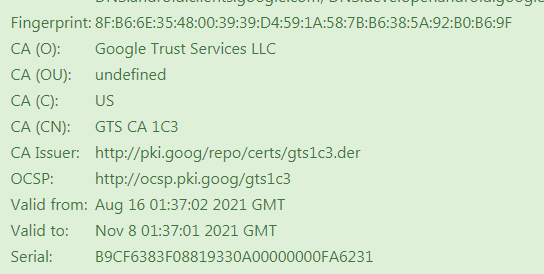
Why are they different every time? Why do they have different expiration dates?
Tested further. This behavior is observed only at Google, on other sites (Mail, Yandex) certificates are static. But Google is surprised, isn't the meaning of the certificate in being the same for everyone?
I understand that there is probably some way to bind several certificates, but then how can I be sure that the certificate is valid?
Perhaps it is worth looking at a non-finger print?
Answer the question
In order to leave comments, you need to log in
A site can have more than one certificate. And all can be valid. They can be, for example, deployed at different entry points, there are 6 of them, only in the context of ip addresses .... In general, everything is ok here.
"isn't the point of a certificate to be the same for everyone?" No, the point is to be able to verify it along the chain of trust.
What you want to check is checked wrong. You need to check the root certificate store and see if there is anything extra there, or import a set of root certificates that you know are correct. Instead of poke into arbitrary sites that may well have a valid chain of trust, expecting that one day some one will come across where traffic has been interfered with - it is not at all necessary that all requests are intercepted.
Well, look not at the fingerprint, but at the chain of trust then - if there is a substitution, there will be some kind of left root certificate at the beginning.
there is a suspicion that the root certificate could be replaced on the PC
How can I make sure the certificate is valid then?
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question