Answer the question
In order to leave comments, you need to log in
Why does hh.ru make many requests to 127.0.0.1 on different ports?
I go to the headhunter and what I see in devtools, in the network - xhr tab, get requests to 127.0.0.1 on different ports:
https://127.0.0.1:5900/
https://127.0.0.1:6900/
https://127.0.0.1:5650/
https://127.0.0.1:5931/
https://127.0.0.1:5938/
https://127.0.0.1:5939/
https://127.0.0.1:3389/
https://127.0.0.1:8080/
https://127.0.0.1:51/
https://127.0.0.1/
https://127.0.0.1:80/
https://127.0.0.1:22/
https://127.0.0.1:445/
https://127.0.0.1:5985/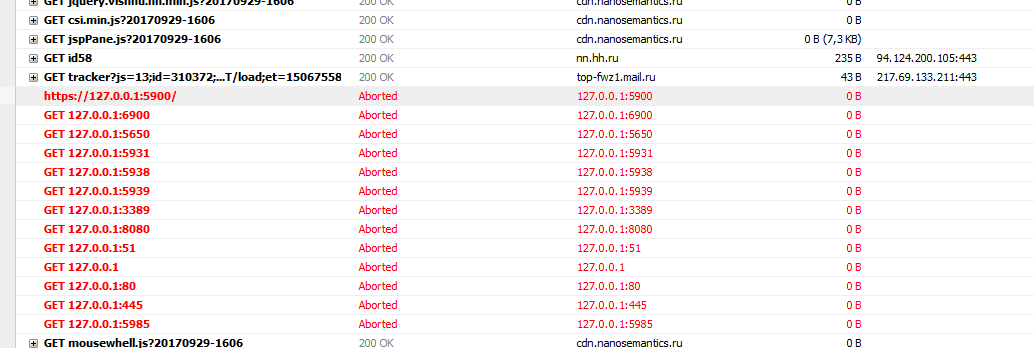
Answer the question
In order to leave comments, you need to log in
Checks the services available on the computer:
5900 - if it listens, then there is a possibility of a VNC service
8080 - proxy
3389 - rdp
, etc. - according to the list of known ports.
Sberbank also checks, and I think it can refuse authentication if these ports are open.
I sketched a server here on my knee:
import socketserver
import threading
ports = [5900, 6900, 5650, 5931, 5938, 5939, 3389, 8080, 51, 80, 443, 445, 5985]
threads = []
servers = []
class RequestHandler(socketserver.BaseRequestHandler):
def handle(self):
binaryData = self.request.recv(1024 * 1024)
print('server {} got data: {}'.format(
self.server.server_address, binaryData))
self.request.sendall("fuck you, hh.ru\n".encode())
def worker(port):
server = socketserver.TCPServer(('localhost', port), RequestHandler)
servers.append(server)
server.serve_forever()
if __name__ == "__main__":
for port in ports:
print('server on port {} is starting...'.format(port))
thread = threading.Thread(target=worker, args=(port,))
threads.append(thread)
thread.start()
for thread in threads:
thread.join()Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question