Answer the question
In order to leave comments, you need to log in
What is better - vpn on the phone or vpn on the router?
What is more reliable - the phone on which the VPN is running, or the phone that connects to the router on which the VPN is configured?
If the phone is vpn, then there will be leaks from the built-in programs, if on the router ... is it difficult to intercept from the phone to the router?
Answer the question
In order to leave comments, you need to log in
Of course on the router! The router wraps DNS on the VPS and the provider can only suck at the lack of DNS, which can be intercepted :) However, it doesn’t hurt to have a VPN configured on the phone - when on the street, for example.
It's essentially the same thing.
What leaks should be on the phone? where?
For home, I have
a VPN to blocked sites on the router, because at home there are a lot of all sorts of PCs / phones / laptops and too lazy to set up on each
phone. I use it when I’m not at home .
gateway, not through your carrier
I think in your question a third-party service is hidden behind VPN, and not the direct meaning of the term (private virtual network) - the union of two trusted extranet segments through an unreliable public channel.
Previously, in local networks and not only in them, data was transmitted in clear text. Passwords in the form of text to access the http site. Receiving mail via pop3 sending via smtp. Printing documents to a printer.
But now almost everything has switched to versions of protocols with encryption.
When you control both the server and clients - everything is secure.
And what happens when using a third-party server. You trust that some third party will play fair.
AdGuard VPN can be used as an example of the fact that nothing prevents you from replacing website certificates and modifying pages. Everything is clear here. You put it in just for that.
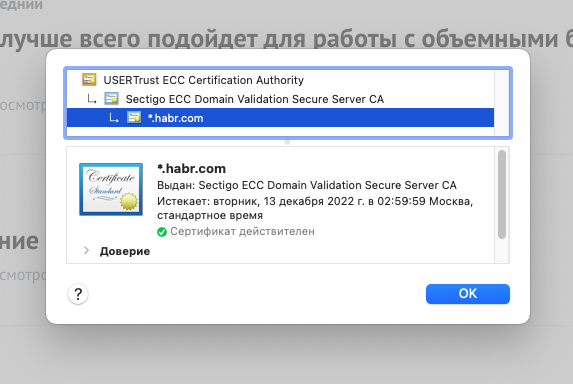
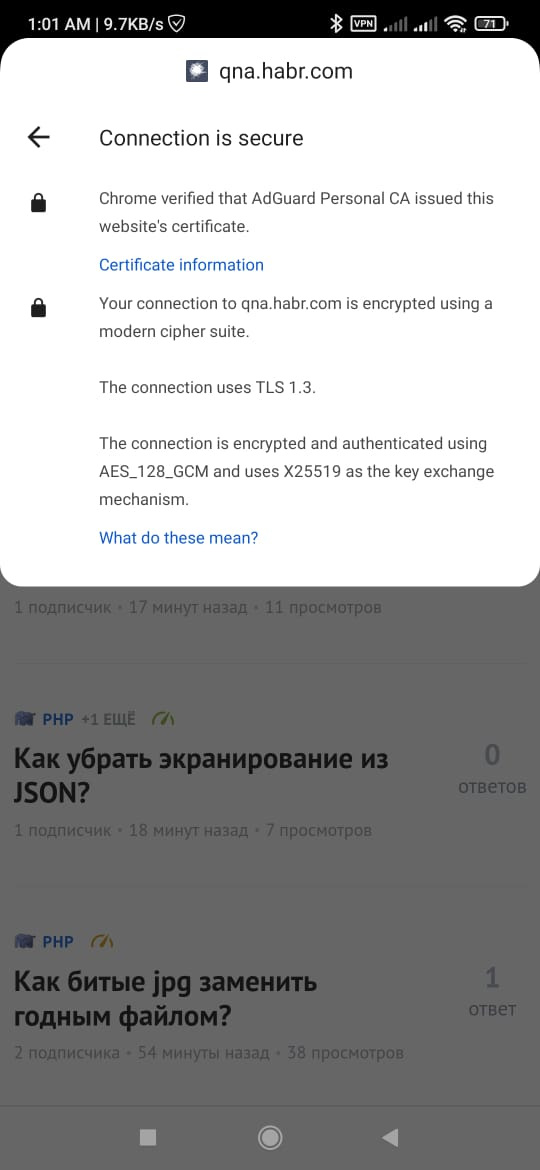
But a free VPN, which is not clear from whom, can do this in its own interests.
In general, if the client part asks to add some kind of certificate to the trusted ones as the root, there is reason to think about why it needs to decrypt the data.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question