Answer the question
In order to leave comments, you need to log in
Port forwarding on Mikrotik?
Hello everyone
I'm trying to forward the port on Mikrotik towards the server. I did everything according to the manuals
But something doesn't work
Where am I the fool?
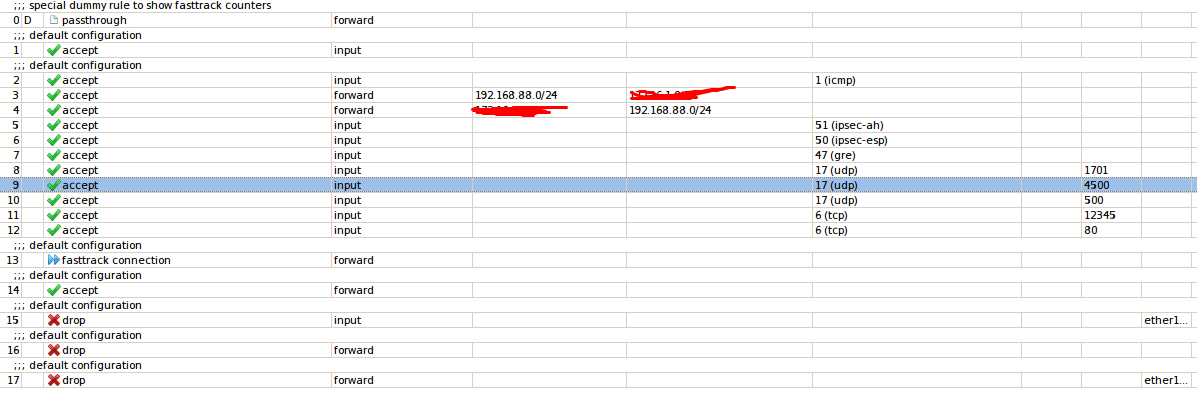
/ip firewall filter
add action=accept chain=input comment="default configuration" connection-state=established,related
add action=accept chain=input comment="default configuration" protocol=icmp
add action=accept chain=forward dst-address=x.x.x.x/24 log=yes src-address=192.168.88.0/24
add action=accept chain=forward dst-address=192.168.88.0/24 log=yes src-address=x.x.x.x/24
add action=accept chain=forward dst-address=192.168.88.110 dst-port=444 in-interface=ether1-gateway protocol=tcp
add action=accept chain=input log=yes protocol=ipsec-ah
add action=accept chain=input protocol=ipsec-esp
add action=accept chain=input protocol=gre
add action=accept chain=input dst-port=1701 protocol=udp
add action=accept chain=input dst-port=4500 protocol=udp
add action=accept chain=input dst-port=500 protocol=udp
add action=accept chain=input dst-port=80 protocol=tcp
add action=fasttrack-connection chain=forward comment="default configuration" connection-state=established,related
add action=accept chain=forward comment="default configuration" connection-state=established,related
add action=drop chain=input comment="default configuration" in-interface=ether1-gateway
add action=drop chain=forward comment="default configuration" connection-state=invalid
add action=drop chain=forward comment="default configuration" connection-nat-state=!dstnat connection-state=new in-interface=\
ether1-gateway
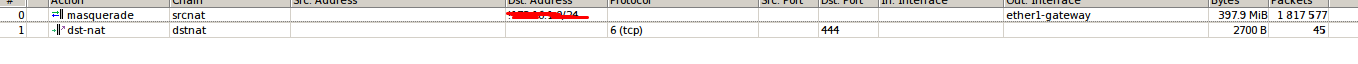
/ip firewall nat
add action=masquerade chain=srcnat dst-address=!172.16.1.0/24 out-interface=ether1-gateway
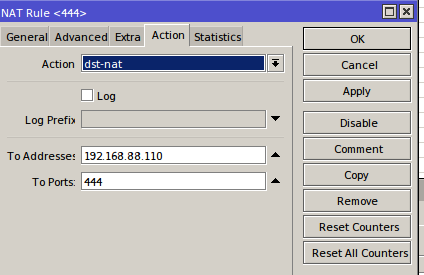
add action=dst-nat chain=dstnat dst-port=444 in-interface=ether1-gateway protocol=tcp to-addresses=192.168.88.110 to-ports=444Answer the question
In order to leave comments, you need to log in
Unload /ip firewall export
Without it, it is not clear what and how. The screenshots do not show all the information.
Below, working configuration for firewall/NAT with open ports for L2TP IPSec, web interface and port forwarding 444 to ip 192.168.88.110
/ip firewall nat
add action=masquerade chain=srcnat comment="masquerade" ipsec-policy=out,none out-interface-list=WAN
add action=netmap chain=dstnat dst-port=444 in-interface=ether1 protocol=tcp to-addresses=192.168.88.110 to-ports=44
/ip firewall filter
add action=accept chain=input comment="ALLOW ESTABLISHED" connection-state=established
add action=accept chain=input comment="ALLOW RELATED" connection-state=related
add action=drop chain=input comment="DROP INVALID" connection-state=invalid
add action=accept chain=input comment="ALLOW ICMP" protocol=icmp
add action=accept chain=input comment="ALLOW WINBOX" dst-port=8291 protocol=tcp
add action=accept chain=input comment="ALLOW L2TP IPSEC" dst-port=500,1701,4500 in-interface=ether1 protocol=udp
add action=accept chain=forward comment="ALLOW L2TP IPSEC" protocol=ipsec-esp
add action=accept chain=input comment="ALLOW WEB-INTERFACE" dst-port=80 protocol=tcp
add action=drop chain=input comment="DROP ALL INPUT"
add action=accept chain=forward comment="ALLOW ESTABLISHED" connection-state=established
add action=accept chain=forward comment="ALLOW RELATED" connection-state=related
add action=drop chain=forward comment="DROP INVALID" connection-state=invalid
add action=accept chain=forward comment="ALLOW ICMP" protocol=icmp
add action=accept chain=forward comment="ALLOW REDIRECT TO RDP" dst-port=444 protocol=tcp
add action=accept chain=forward comment="ALLOW INTERNET FROM LOCAL" out-interface=ether1 src-address=192.168.88.0/24
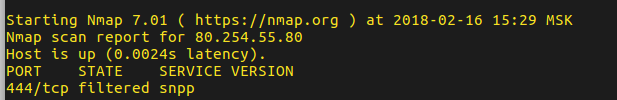
add action=drop chain=forward comment="DROP ALL FORWARD"The screenshot shows that the packets go through the nata rule, maybe the problem is still in the server?
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question