Answer the question
In order to leave comments, you need to log in
Mikrotik rb951g 2hnd VPN L2TP - the client does not see the LAN, how to fix it?
configured like this: bozza.ru/art-248.html , created a connection on win8. It connects, the connection is seen on the router, but the client does not see the local network and does not ping computers in the LAN, although the network address is the same as in the main LAN
Answer the question
In order to leave comments, you need to log in
Hands fall off if you take screenshots?
1.IP-Firewall-Filter rules
2.IP-Firewall-NAT
3.IP-Routes
of course they won't fall off:
[*****@MikroTik] /ip> route print
Flags: X - disabled, A - active, D - dynamic, C - connect, S - static, r - rip, b - bgp, o - ospf, m - mme, B - blackhole, U - unreachable, P - prohibition
# DST-ADDRESS PREF-SRC GATEWAY DISTANCE
0 ADS 0.0.0.0/0 **.**.228.1 0
1 ADC **.**.228.0 /24 **.**.228.128 ether1-gateway 0
2 ADC 192.168.85.0/24 192.168.85.1 wlan2 0
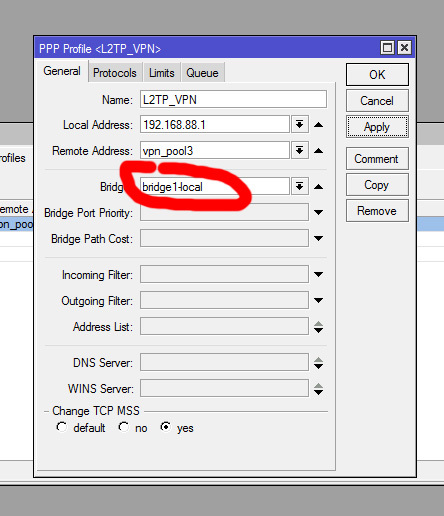
3 ADC 192.168.88.0/24 192.168.88.1 bridge1-local 0
[*****@MikroTik] /ip firewall>> filter print
Flags: X - disabled, I - invalid, D - dynamic
0 ;;; icmp
chain=input action=accept protocol=icmp log=no log-prefix=""
1 ;;; established
chain=input action=accept connection-state=established log=no log-prefix=""
2 ;;; related
chain=input action=accept connection-state=related log=no log-prefix=""
3 ;;; manage
chain=input action=accept in-interface=bridge1-local log=no log-prefix=""
4 ;;; VPN
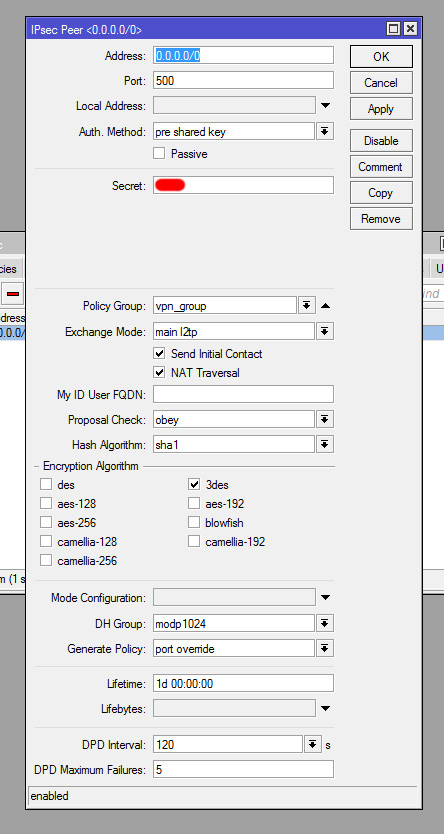
chain=input action=accept connection-state=new protocol=udp in-interface=ether1-gateway dst-port=1701,500,4500 log=no log-prefix=""
5 ;;; VPN
chain=input action=accept connection-state=new protocol=ipsec-esp in-interface=ether1-gateway log=no log-prefix=""
6 ;;;
chain=input action=accept protocol=tcp in-interface=ether1-gateway dst-port=443 log=no log-prefix=""
8 ;;; all other drop
chain=input action=drop in-interface=ether1-gateway log=no log-prefix=""
9 ;;; Drop invalid connection packets
chain=forward action=drop connection-state=invalid log=no log-prefix=""
10 ;;; Allow established connections
chain=forward action=accept connection-state=established log=no log-prefix=""
11 ;;; Allow related connections
chain=forward action=accept connection-state=related log=no log-prefix=""
12 ;;; Allow access to internet
chain=forward action=accept src-address-list=inet in-interface=bridge1-local out-interface=ether1-gateway log=no log-prefix=""
13 chain=forward action=accept src-address-list=inet2 in-interface=wlan2 out-interface=ether1-gateway log=no log-prefix=""
15 ;;; https NAS
chain=forward action=accept protocol=tcp dst-port=443 log=no log-prefix=""
16 ;;; VPN
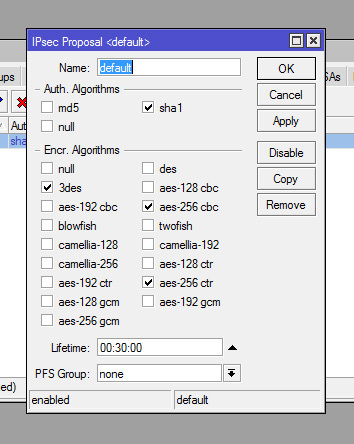
chain=forward action=accept protocol=ipsec-esp log=no log-prefix=""
17 ;;; VPN
chain=forward action=accept protocol=udp dst-port=1701,500,4500 log=no log-prefix=""
18 ;;; All other drop
chain=forward action=drop log=no log-prefix=""
/ip firewall nat>>
Flags: X - disabled, I - invalid, D - dynamic
0 chain=srcnat action=masquerade out-interface=ether1-gateway log=no log-prefix=""
1 chain=dstnat action=dst-nat to-addresses=192.168 .88.111 protocol=tcp in-interface=ether1-gateway dst-port=443 log=no log-prefix=""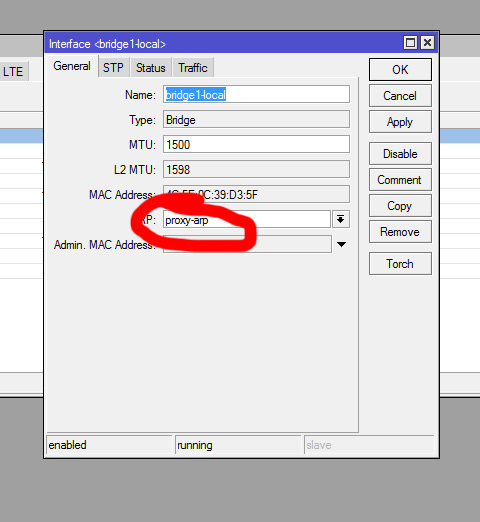
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question