Answer the question
In order to leave comments, you need to log in
Mikrotik - problem with firewall rules and setting up a vpn connection?
Guys, hello!
help me understand where I have a problem (floating), there are two microts, one with a "white" ip, the other with a "gray", on the one with the "white" vpn server (l2tp / ipsec) is raised, microts with a "gray" ip establishes a connection and everything is fine. But, often the connection breaks for no apparent reason and cannot be established, I attach a screenshot of the log from the client side,
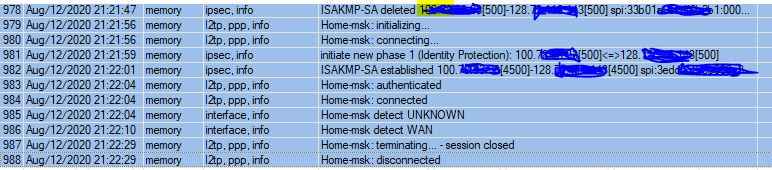
if at this moment we take and turn off all the rules in the firewall, the session will be established, then we turn the rules back on, kill the session and it itself is installed with the rules already enabled firewall, although a minute ago I could not .... where is my cant? Moreover, if you start turning off the prohibiting rules, this does not work, below the firewall rule
I will be grateful for your help.
0 D ;;; special dummy rule to show fasttrack counters
chain=forward action=passthrough
1 ;;; NO Ping Wan
chain=input action=drop protocol=icmp in-interface=WAN-ether1
icmp-options=8:0 log=no log-prefix=""
2 ;;; Dostup Mikrotik Winbox
chain=input action=accept protocol=tcp dst-port=8291 log=no log-prefix=""
3 ;;; defconf: accept established,related,untracked
chain=input action=accept connection-state=established,related,untracked
log=no log-prefix=""
4 ;;; VPN
chain=output action=accept protocol=udp dst-port=50,500,4500,1701 log=yes
log-prefix=""
5 ;;; VPN PPTP for Client Connected
chain=input action=accept protocol=tcp dst-port=1723,1194 log=no
log-prefix=""
6 ;;; VPN
chain=input action=accept protocol=ipsec-esp log=no log-prefix=""
7 ;;; VPN
chain=input action=accept protocol=ipsec-ah log=no log-prefix=""
8 ;;; VPN
chain=input action=accept protocol=l2tp log=yes log-prefix=""
9 ;;; VPN
chain=input action=accept protocol=gre log=yes log-prefix=""
10 chain=input action=accept protocol=igmp in-interface=WAN-ether1 log=no
log-prefix=""
11 ;;; Torrent
chain=input action=accept connection-state=new protocol=tcp
dst-port=51413 log=no log-prefix=""
12 ;;; allow sstp
chain=input action=accept protocol=tcp dst-port=443 log=no log-prefix=""
13 ;;; defconf: accept in ipsec policy
chain=forward action=accept log=no log-prefix="" ipsec-policy=in,ipsec
14 ;;; defconf: accept out ipsec policy
chain=forward action=accept log=no log-prefix="" ipsec-policy=out,ipsec
15 ;;; defconf: fasttrack, Esli vkluchit, ne rabotaet QoS
chain=forward action=fasttrack-connection
connection-state=established,related log=no log-prefix=""
16 ;;; defconf: accept established,related, untracked
chain=forward action=accept
connection-state=established,related,untracked log=no log-prefix=""
17 ;;; defconf: drop invalid
chain=forward action=drop connection-state=invalid log=no log-prefix=""
18 ;;; defconf: drop invalid
chain=input action=drop connection-state=invalid log=no log-prefix=""
19 ;;; defconf: drop all not coming from LAN
chain=input action=drop in-interface-list=!LAN log=no log-prefix=""
20 ;;; defconf: drop all from WAN not DSTNATed
chain=forward action=drop connection-state=new
connection-nat-state=!dstnat in-interface-list=WAN log=no log-prefix=""
Answer the question
In order to leave comments, you need to log in
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question