Answer the question
In order to leave comments, you need to log in
Mikrotik is not available. Oddities in winbox when connected, can anyone come across?
Good day to all! An incident happened to me today. So I have a HAP mini lite, I mean, I'm sitting and playing around with Wi-Fi settings, when suddenly my winbox loses connection with Mikrotik, I'm confused. I press connect, it says it's impossible to connect to the device, I restart winbox just in case, Mikrotik is in the visibility zone as usual, but the connection does not occur. I'm trying to log in from the Mikrotik application on an android smartphone, the same song. Well, I think I'll have to do a reset, since there is a fresh backup. So I rip it out of the socket, hold down the magic button, plug it into the socket, wait and what do I see?
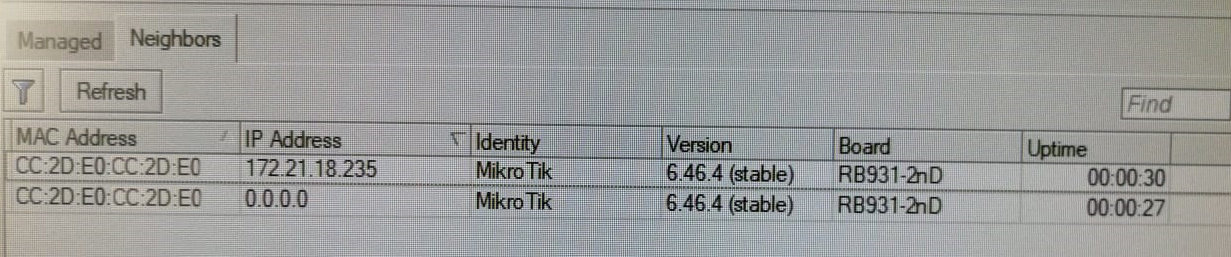
Well, what a hedgehog in the list of 2 identical microtics, both with identical poppies, only one has a strange address (I had the default 192.168.88.1), and there should not be such a thing as far as I remember. So I rebooted Mikrotik, restarted winbox, for greater fidelity, and nothing changed until I went to the one that 0.0.0.0 and did not poke to delete the configuration after reset-a. My grid is simple, the WAN provider's cable is in Mikrotik and there are more and more pieces of iron except for a PC and a couple of smartphones. And now I'm sitting and thinking, either a glitch or hacked. Can anyone come across or tell me what kind of tambourine?
My firewall:
0 D ;;; special dummy rule to show fasttrack counters
chain=forward action=passthrough
1 X ;;; HAR
chain=forward action=accept protocol=tcp dst-port=888 log=no log-prefix=""
2 ;;; Access from LAN
chain=input action=accept in-interface=Bridge log=no log-prefix=""
3 ;;; Allow established and connected connections
chain=input action=accept connection-state=established,related log=no log-prefix=""
4 ;;; Allow Address List LAN
chain=input action=accept src-address-list=allow-ip log=no log-prefix=""
5 ;;; Drop invalid
chain=forward action=drop connection-state=invalid log=no log-prefix=""
6 ;;;
chain=input action=drop in-interface=domru log=no log-prefix=""
7 ;;; Fasttrack#
chain=forward action=fasttrack-connection connection-state=established,related log=no
log-prefix=""
8 ;;; Fasttrack accept
chain=forward action=accept connection-state=established,related log=no log-prefix=""
9 ;;; Deny connections from WAN -> LAN
chain=forward action=drop in-interface=domru out-interface=Bridge log=no log-prefix=""
Answer the question
In order to leave comments, you need to log in
1. You can access microt via MAC, even if you turn off all services. winbox, ssh, telnet. You can still come in. The main thing in MAC SERVER is to specify that you want to use microt only from LAN.
2. Enemies can launch a Bogon network over the WAN, those simulate 192.168.x.x on the WAN. It is necessary to discard such networks on the firewall.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question