Answer the question
In order to leave comments, you need to log in
Mikrotik client Strongswan l2tp/ipsec how to configure correctly?
Hello, I'm trying to put all traffic through vpn. Mikrotik is at home, ubuntu is installed on a remote machine with strongswan configured (configured through a script on DigitalOcean) I want all devices in the Mikrotik network to go to the Internet via vpn on DO.
It connects from the phone to vpn without any problems and there is internet, there is no internet on Mikrotik when connected to vpn)
Mikrotik settings
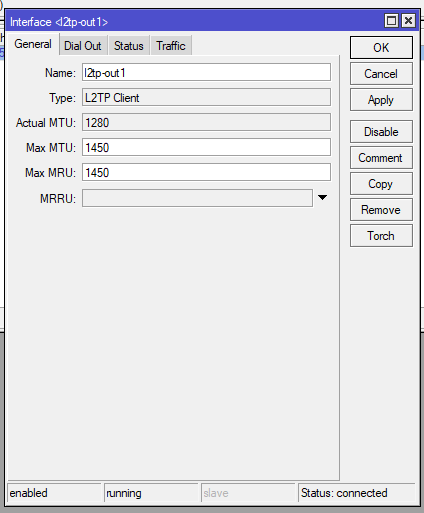
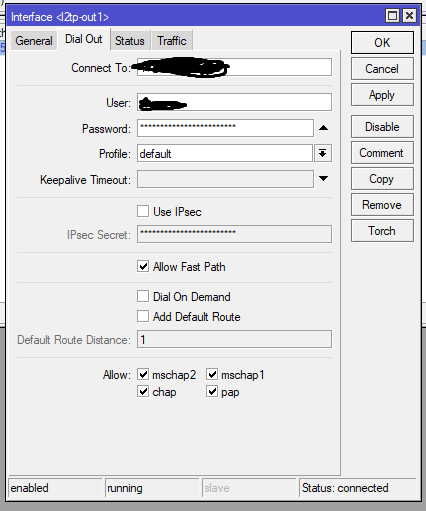
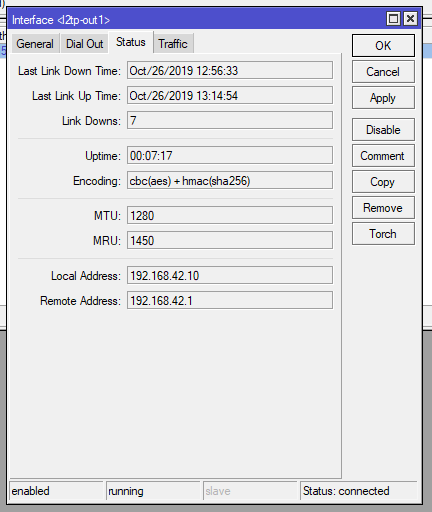
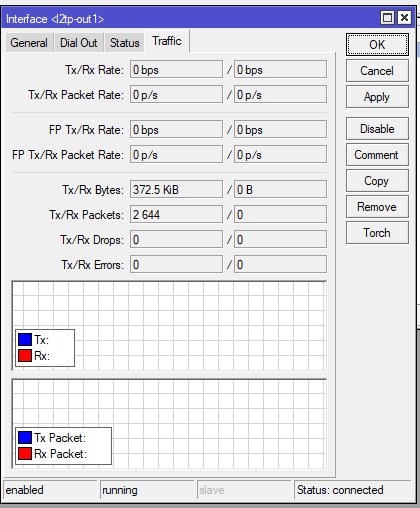
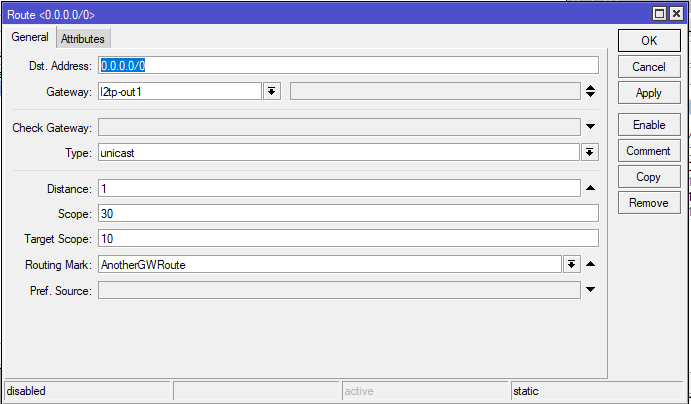
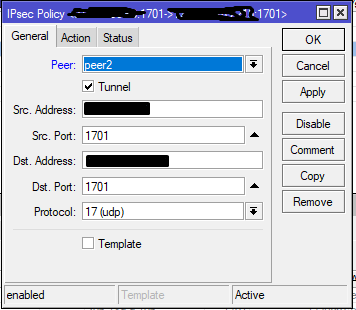
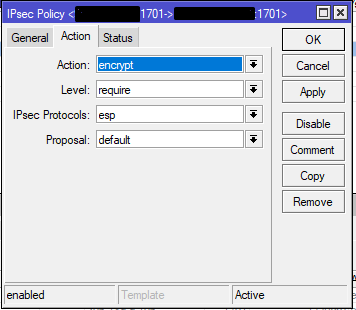
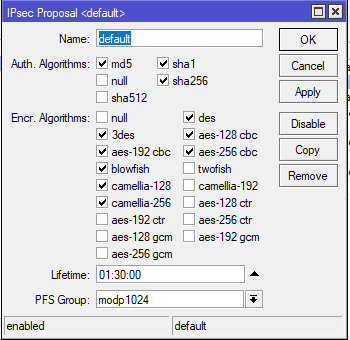
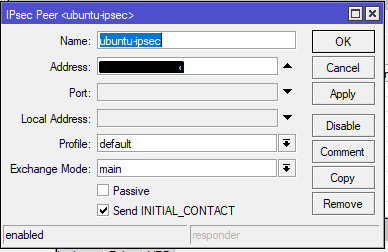
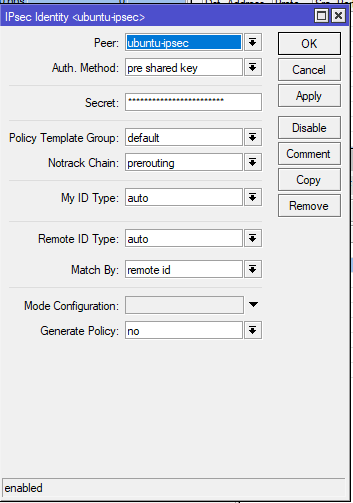
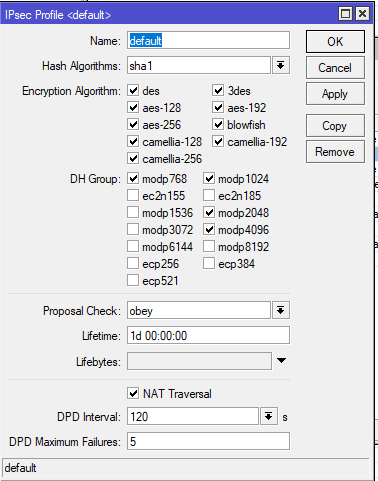
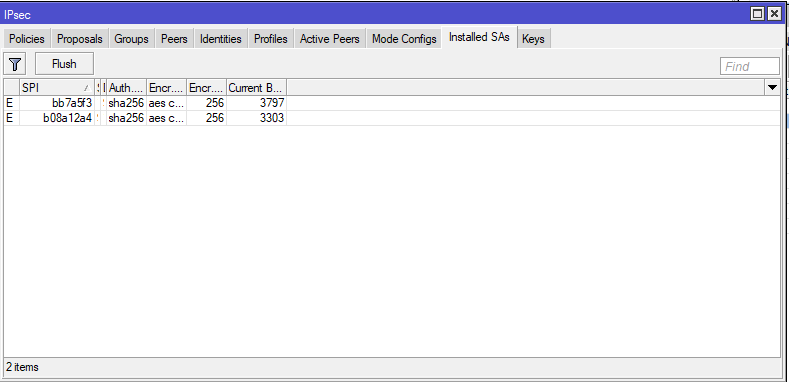
Answer the question
In order to leave comments, you need to log in
Better implementation of IPSec on Mikrotik can only be strongwan. I say this because I set up IPSec on both Mikrotik and Linux. And once I had to configure IPSec between juniper vSRX and Linux server. On Linux, I used strongwan route based, the mode is configured using crutches, you need to mark the interfaces and specify the marking in the config
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question