Answer the question
In order to leave comments, you need to log in
Is it possible to hack through POST?
Recently I saw this code from a friend:
$url = 'http://blabla.com/?id='.(array_key_exists('id', $_POST) ? $_POST["id"] : '').';
$otvet = json_decode(file_get_contents($url), true);
if($otvet['error'] == 'no'){
...
}Answer the question
In order to leave comments, you need to log in
You should not look at this piece of code, because here, the id parameter is simply passed to the request called by the file_get_contents function.
And you need to look where the $url request is processed on the blabla.com resource: is there or is there no processing of incoming data.
In general, see what is SQL injection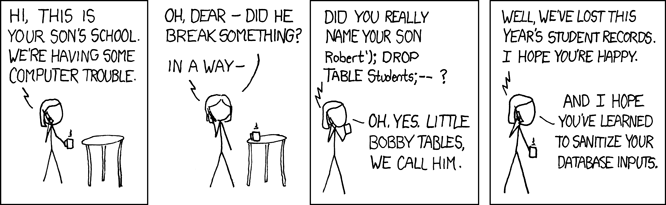
Specifically, in this example, it is quite likely to get a denial of service on the first student who decides to crawl the site using nessus. But even if it doesn’t come to that (in the sense of a denial of service, schoolchildren will not keep themselves waiting long), then it will be a waste of resources for processing connections from both this application and blabla.com. This can hardly be called a terrible vulnerability, but the code clearly smacks of something unpleasant.
Once my programming teacher asked me to write a program that would display the result of adding two numbers 3 and 2. So no one coped with the task normally, everyone wrote like
x=2
y=3
z=x+y
print z
Everyone got no, but the solution was simple print 5. I remember it for the rest of my life.
It's about the same here. I asked a question, and in response a lot of unnecessary information, 80% of which does not relate to the essence of the question.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question