Answer the question
In order to leave comments, you need to log in
Is it a vulnerability?
I read about xcc vulnerabilities and decided to find a site with this vulnerability and it seems I found it to write what kind of site I don’t want, but I will describe what is happening and what questions I have. There are two fields, one for searching the other for selection: all words, a phrase, or any word in general, a drop-down list. In the search field, if you write just a word, then there will be nothing between the two forms, and if you insert "><script>alert()</script>
it, it will appear between them alert()" class="text-input" />
. Tell me this vulnerability, if you need to do some kind of manipulation for additional information, write. And what could be the consequences of such a vulnerability?
picture of what's going on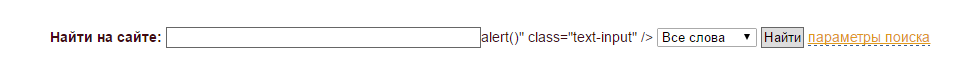
Answer the question
In order to leave comments, you need to log in
Yes, most likely it can be promoted to XSS, try a vector like" onmouseover="alert()" b="
Yes, it's XSS and you can execute almost any (If filters are still there) JavaScript code in the client's browser... There is no filter for quotes and they are not converted to html code. You can try something different:
"onfocus=prompt(/OPENBUGBOUNTY/) autofocus= />
"onmouseover=confirm(/OPENBUGBOUNTY/)
"onload=prompt(/XSSPOSED/)Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question