Answer the question
In order to leave comments, you need to log in
Iptables redirect eth0 to eth1, how to check if it works?
The point is this:
I have a computer with eth0 at home - an Internet (direct via dhcp from the provider) and eth1 - which is connected to the router through which I want to distribute the waffle, but there is no time to configure.
Because I just switched to Linux (by the way, DEBIAN JESSIE), I also installed it at work on a virtual machine in order to write a script for network settings and just execute it at home.
But there is a problem, I need to check it, 2 attempts to set it up at home have already failed (so I decided to do it this way), the question is:
how to set up packet routing on eth1 and check it, i.e. packets will be distributed only through eth0->eth1->browser, if for example to make ifconfig eth1 down - that the Internet will be cut off?
tried like this:
#принимаем только установленные
iptables -P INPUT DROP
iptables -A INPUT -i eth0 -m state --state ESTABLISHED,RELATED -j ACCEPT
#тут пытаюсь направить все пакеты на eth1
iptables -tnat -A PREROUTING -i eth0 -j DNAT --to-destination 192.168.10.5
#собственно думаю понятно, что я хотел сделать
iptables -P FORWARD DROP
iptables -A FORWARD -i eth0 -o eth1 -j ACCEPT
iptables -A FORWARD -i eth1 -o eth0 -j ACCEPT
#вот тут есть вопрос: я запрещаю все локальные исходящие пакеты с eth0, но с eth1->eth0 - будет считаться ?
iptables -A OUTPUT -o etho -j DROP
#собственно сам роутинг
iptables -tnat -A POSTROUTING -o eth0 -j MASQUERADEAnswer the question
In order to leave comments, you need to log in
It is necessary to turn the computer with debian into a router:
sysctl net.ipv4.ip_forward=1 # Разрешаем шлюзу передавать транзитный трафик
iptables -F FORWARD # На всякий случай очистим цепочку FORWARD
# Разрешаем проходить пакетам по уже установленным соединениям
iptables -A FORWARD -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT
# Разрешаем исходящие соединения из локальной сети к интернет-хостам
iptables -A FORWARD -m conntrack --ctstate NEW -i eth1 -j ACCEPT
iptables -P FORWARD DROP # Весь остальной транзитный трафик — запрещаем.
iptables -t nat -F POSTROUTING # На всякий случай очистим цепочку POSTROUTING таблицы nat
# Маскарадим весь трафик, идущий через eth0
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE#here there is a question: I forbid all local outgoing packets from eth0, but from eth1->eth0 - will it be considered ?With this rule, you will cut off access to the Internet from the Debian router itself. the packet first passes output and then postrouting. Here is a visual diagram:
iptables -A OUTPUT -o etho -j DROP
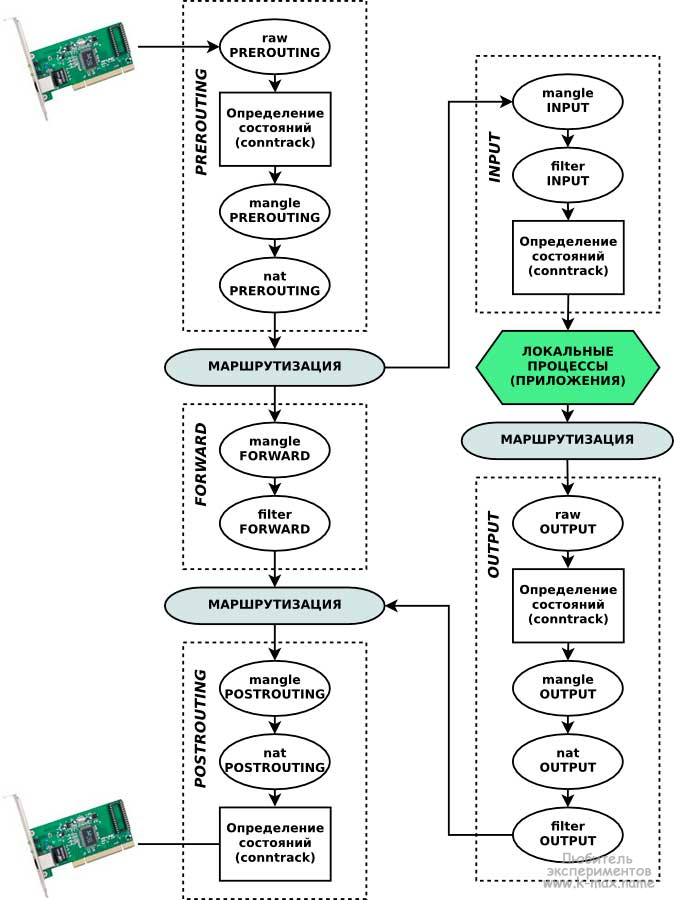
iptables -tnat
won't work because -t nat will be valid.
#собственно думаю понятно, что я хотел сделать
iptables -P FORWARD DROP
iptables -A FORWARD -i eth0 -o eth1 -j ACCEPT
iptables -A FORWARD -i eth1 -o eth0 -j ACCEPT#принимаем только установленные
iptables -P INPUT DROPyou dropped all traffic forwarding. After the first rule, the subsequent ones will not work.
won't work because -t nat will be valid.
It's not very clear what you want to do. What is the address in DNAT, what are the addresses on the interfaces?
Not good. First you banned the forward, then you allowed it. Do you have more than two adapters there?
If you need to make a simple primitive NAT, as on ordinary routers, then this is done in a completely different way, without dnat, but with snat / masquerade.
iptables -t nat -A POSTROUTING -o <interface towards the internet> -j MASQUERADE
iptables -P FORWARD ACCEPT
sysctl -w net.ipv4.ip_forward=1
This is usually enough if you haven't screwed up elsewhere.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question