Answer the question
In order to leave comments, you need to log in
Intercepted by HTTPS, signed with the left signature, how to find the culprit?
I ran into a problem on a friend's computer - some kind of bad program:
1. Intrudes into https traffic, re-signs server certificates with a certificate from the Moscow office "TNS GALLUP MEDIA"
2. Added this certificate to the trusted root certificates store.
Reminds me of the same piece of paper from the three musketeers "The submitter of this document is acting on my orders and for the good of France. Richelieu"
Actually confirmation:
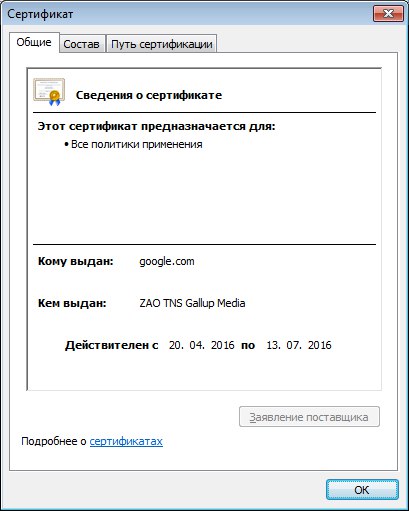
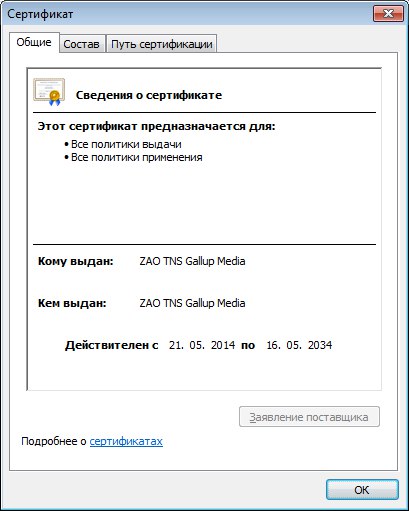
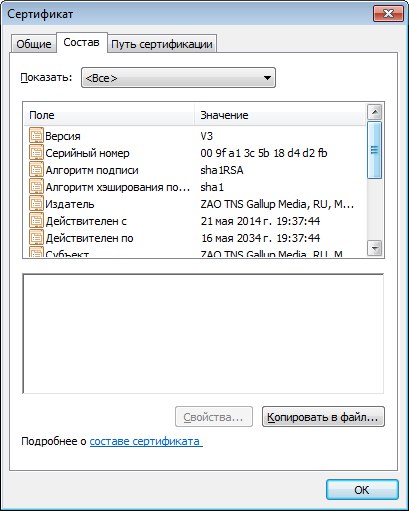
From the most suspicious - Avast antivirus, but disabling all three filters (file, mail and web), followed by a reboot, does not matter helped.
I managed to notice strange behavior only thanks to working from a virtual machine - it’s so easy not to add it to the trusted certificate store.
Help in diagnosing, maybe someone has already come across?
UPD: The culprit turned out to be the ResearchBar plug-in from the Internet Questionnaire Company
As expected... Thank you!
Answer the question
In order to leave comments, you need to log in
This TNS, as far as I understand, collects information from computers, then cooks up various polls and ratings from it. I myself have not come across this particular rubbish, but here the approach is standard for any software with similar behavior. It most likely came to you when installing some free software, you didn’t uncheck the daw somewhere, etc. Pretty common distribution method. It seems to be legal, but you want to strangle for such behavior :)
You can do the following (listed by degree of difficulty):
1.Check the browser proxy settings and if you have a typical configuration (no proxy), then remove the proxy settings, if any. Remove all unnecessary programs and programs whose purpose you do not know, as well as recently installed programs (there is a risk of deleting device drivers). After removing the programs in the user profile and the general profile (c:\ProgramData), delete the directories of these programs from AppData. Purge the user's %TEMP% directory. Clear browser caches, or even better, delete browser profiles.
2.Create a new user in the system, log in with him, if the same behavior does not occur, then your spy has registered in the profile of the previous user. You can transfer the necessary data from the old user, and delete the old account. Or, if the account is as expensive as memory - delete the profile of the old user, log in to them, the profile will be created from scratch. Or rename the directory with the profile, create a new one and transfer the information. In general, act more carefully here so as not to lose your information. If there is nothing of value, then you can safely delete the profile.
3. If none of the above helps, then the spy penetrated the system quite deeply - it was installed in Program Files or in the Windows directory. Find a boot disk / flash drive with an antivirus: Casper has it, other web has ready-made assemblies. Set up a full scan with the removal of the found.
4.Reinstall Windows with system partition formatting.
Personally, I would start immediately with 2 points. If it does not help, then 1,3,4. Point 3 is not particularly effective, but it should not be excluded.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question