Answer the question
In order to leave comments, you need to log in
How to split WAN by IP addresses?
Hello, friends!
There is an office network organized as follows: 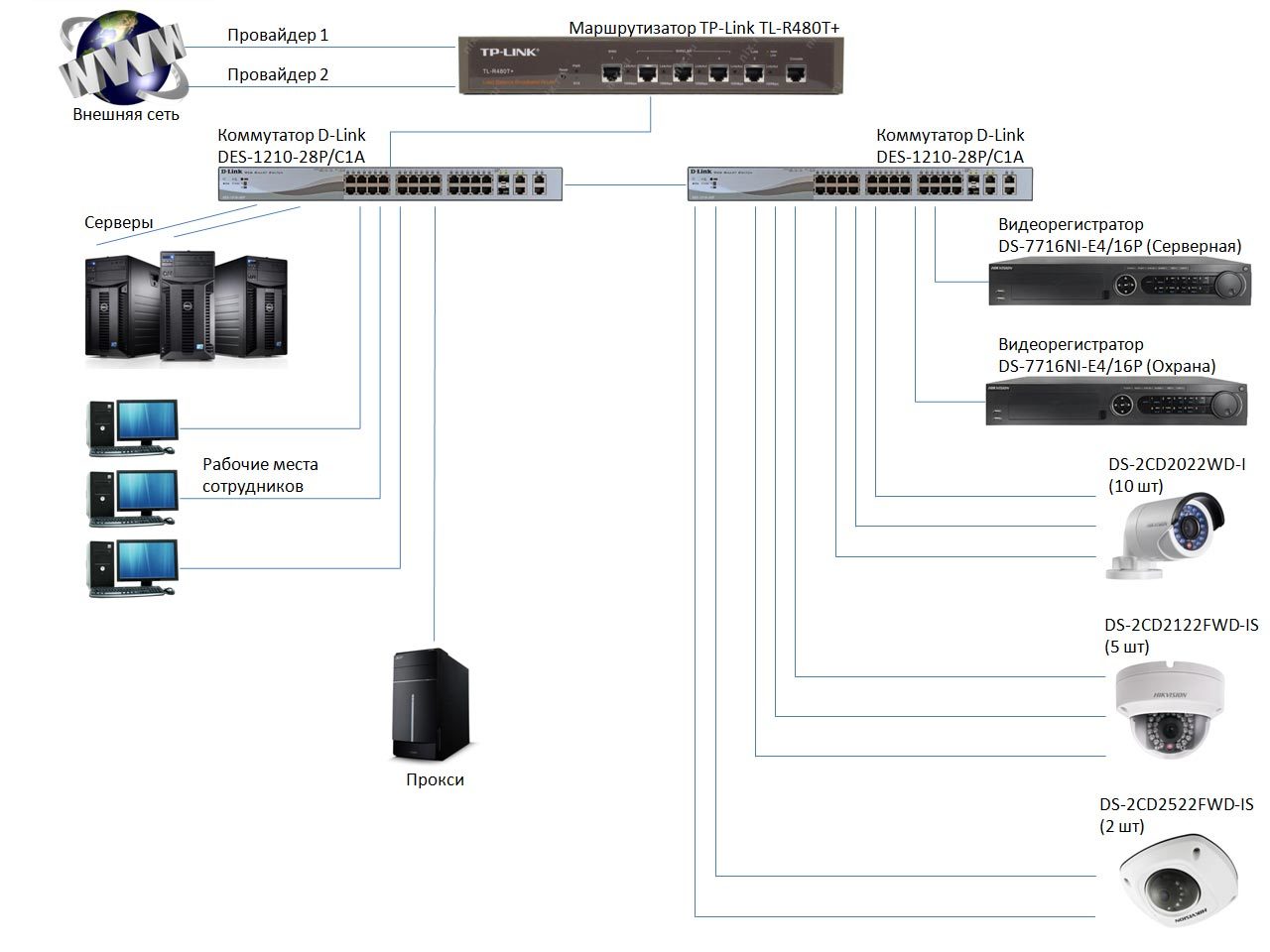
We want to have separate access to video surveillance from the outside. Separate, that is, not connected to the office network, so that if an intruder gains access to video surveillance, he could not get inside the office network at the same time.
What we have come up with so far is as follows: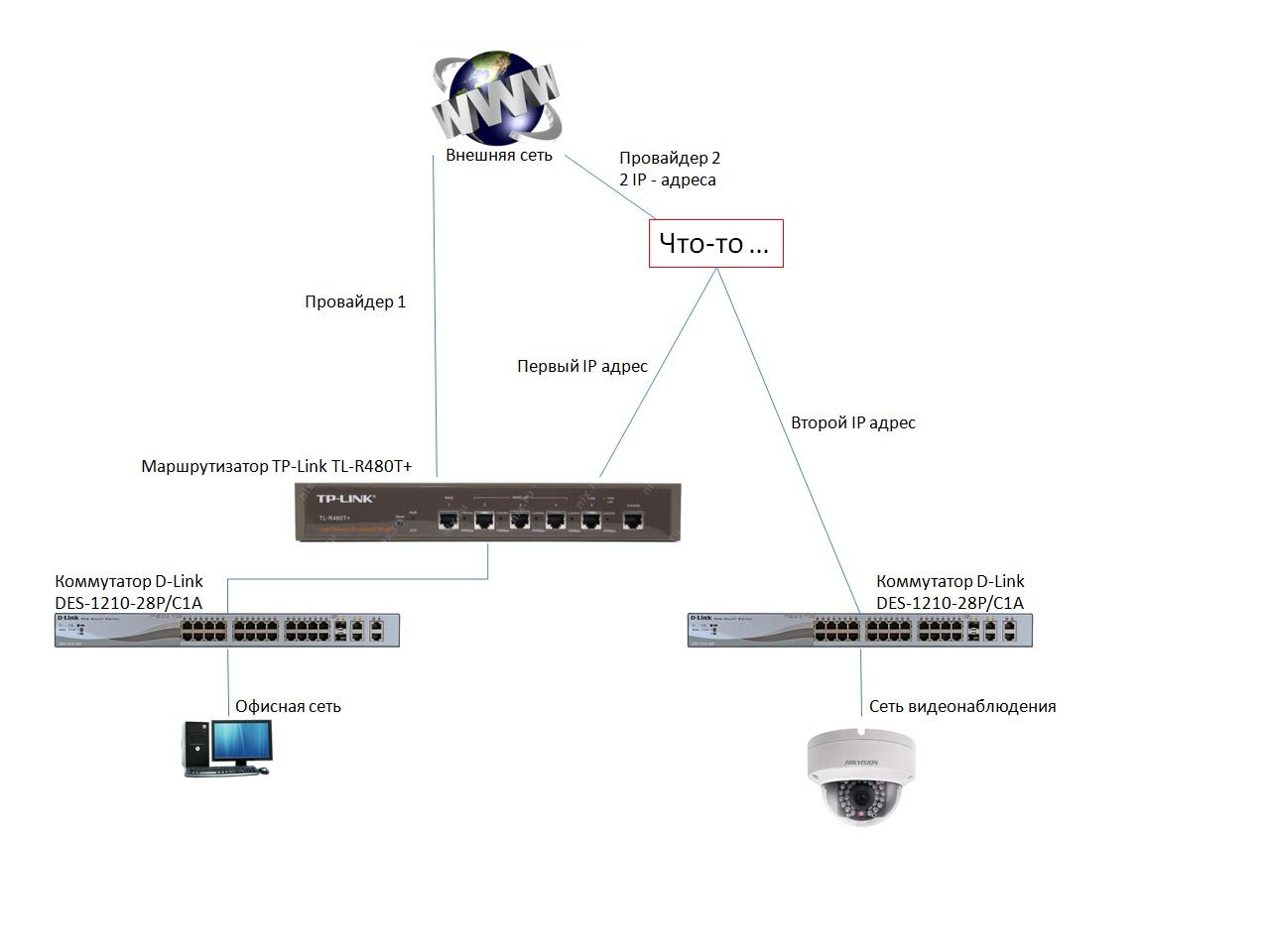
We have two ISPs in case there is an outage with one of them. We do not touch provider 1, order a second IP address from provider 2, collect what is shown in the second figure (after replacing the "Something" block with something working) and disconnect the office network switch from the video surveillance switch. The logic is as follows: we will access video surveillance at the second IP address of provider 2, nothing will change for the rest of the network (its protection is provided further - by a router and a proxy server). Well, and accordingly, in order not to clog the Internet channel, access to video surveillance from the internal network should also be carried out not "via the Internet", but inside the "Something" block.
Therefore, the "something" block must:
1.
2. Be able to forward ports. Apparently, this will already be a router, on the WAN of which a cord with an ip address for video surveillance will come. It is also desirable that it forwards ports only for a set of ip-addresses from which it is accessed, and "denies" the rest of the ip-addresses.
3. Conduct data exchange between networks within themselves, and not "via the Internet."
Our router can also be replaced with the "Something" block, if it is more correct.
Please tell me what equipment or set of equipment we need to buy, and where to look for the necessary settings?
Thank you!
Answer the question
In order to leave comments, you need to log in
How to split WAN by IP addresses?Routes and firewall.
Please tell me what equipment or set of equipment we need to buyNone.
It seems to me that everything can be done much easier, especially since you have Mikrotik. Look in the direction of DMZ, it seems to me that this is exactly what you need, in Mikrotik it is configured for once, there is a lot of information in Google.
Alex Suvoroff : Thank you so much for your reply! There is one more thing: everything that enters the router is redirected to a proxy, where almost everything is prohibited, including our access to video surveillance, so from what was available, we assembled this scheme Do 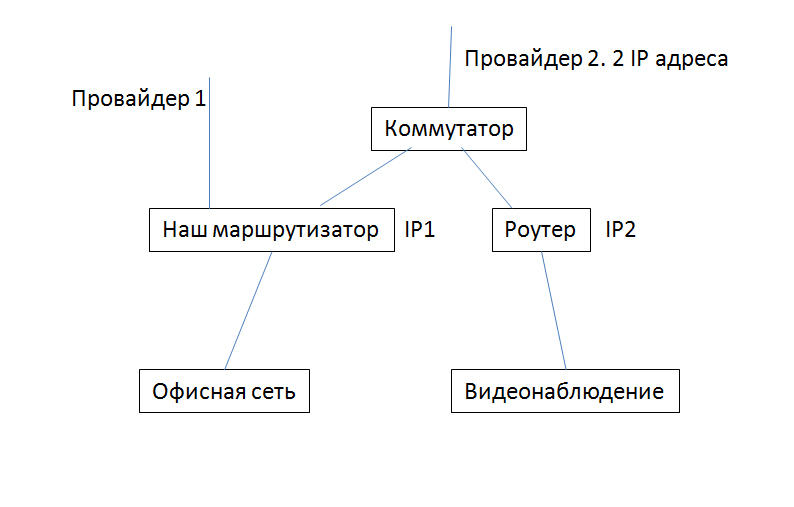
you think it will work correctly ? Naturally, taking into account your comment about the additional route rule, i.e. we will access video surveillance from the internal network only through the router port corresponding to IP1
I would look towards setting up VLANs. Video surveillance - in one VLAN'e, office network - in another. In addition, your VLAN equipment (including 802.1q) supports.
PS And in order to have access to viewing video surveillance from the office network, we access the video server via external IP using the "loopback".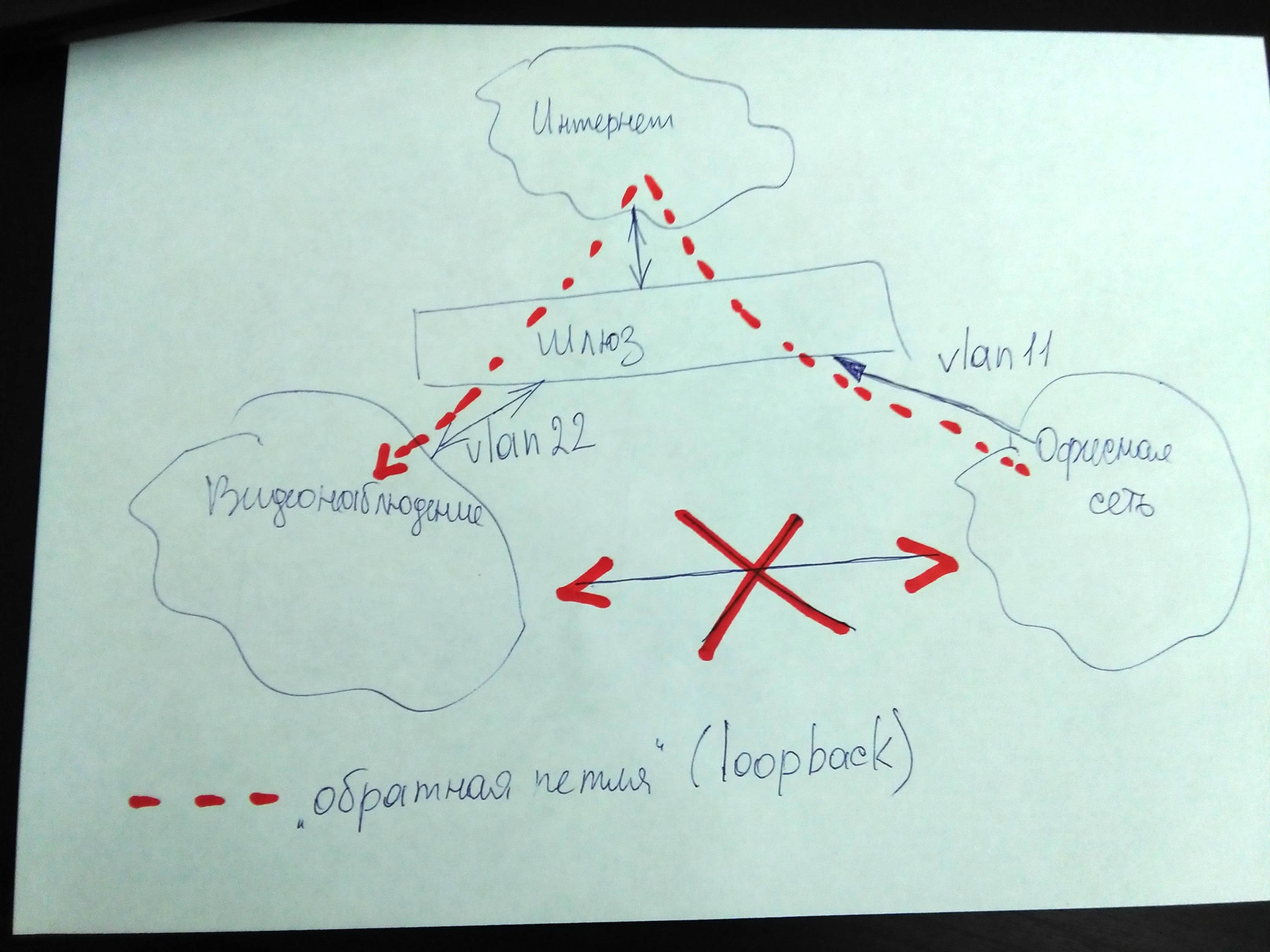
Switch the second switch to the router. Set up firewall and routing on the router.
There are two attack options, the first is a perimeter attack, i.e. an attempt to take control of the router from the outside, a second attack on services outside the "border" of the router. If you want to secure the network and believe that the services in the video surveillance network may be vulnerable, then you should treat it as an untrusted network and configure the firewall accordingly (i.e. consider that this is the second Internet of the same kind).
But we should not forget that having gained access to the video surveillance network, an attacker can use a very sophisticated attack based on video surveillance data, ranging from password spying to cunning social engineering.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question