Answer the question
In order to leave comments, you need to log in
How to set up a Windows AD subordinate CA if root CA on Linux openssl (easyrsa)?
Gentlemen, good day!
I came up with the idea to configure the issuance of certificates for users and devices on the network. Since AD is being used, the decision was made to raise Windows Certificate Services.
In order to save money, I want the certificate of the root certificate server to be generated by openssl (I use easyrsa).
So, in the vars file from the easyrsa kit, I changed the following:
set_var EASYRSA_DN "org"
set_var EASYRSA_DIGEST "sha512"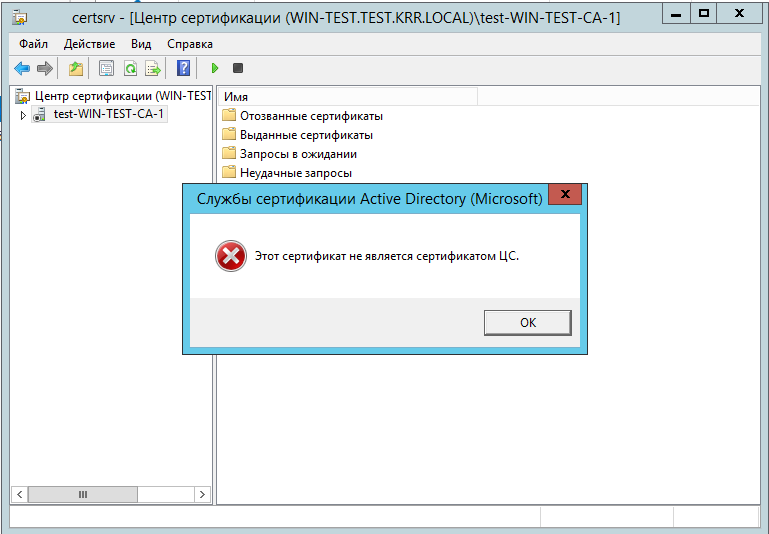
Answer the question
In order to leave comments, you need to log in
I won’t say anything about easyrsa, but the CA certificate must have a special sign that it is a CA certificate. The desire to create a CA, then release a sub-CA and issue certificates in Windows on its behalf, in principle, takes place. When there is Windows and non-Windows on the network, there are, for example, Mikrotiks, d-link, and some other devices ... Again, it is easier for users to generate certificates on openssl. But this is if you understand what to do - no easyrsa will be needed there.
If you just need a certificate service for Windows, then don't pull yourself out of the swamp by your hair - start the service and let it generate the CA root certificate by itself. True, you should immediately take into account that without an additional PKCS # 12 template, there is no way for the user to collapse - you can only getcertificate filled with data based on AD and only on one computer.
To issue a CA certificate using openssl, openssl.cnf must contain the
[ v3_ca ]
basicConstraints = CA:true
section, and when a certificate is issued with this section as an extension, it becomes a CA certificate.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question