Answer the question
In order to leave comments, you need to log in
How to forward traffic 80/443 from interface eth0 to ip address of openvpn client?
Hello everyone!
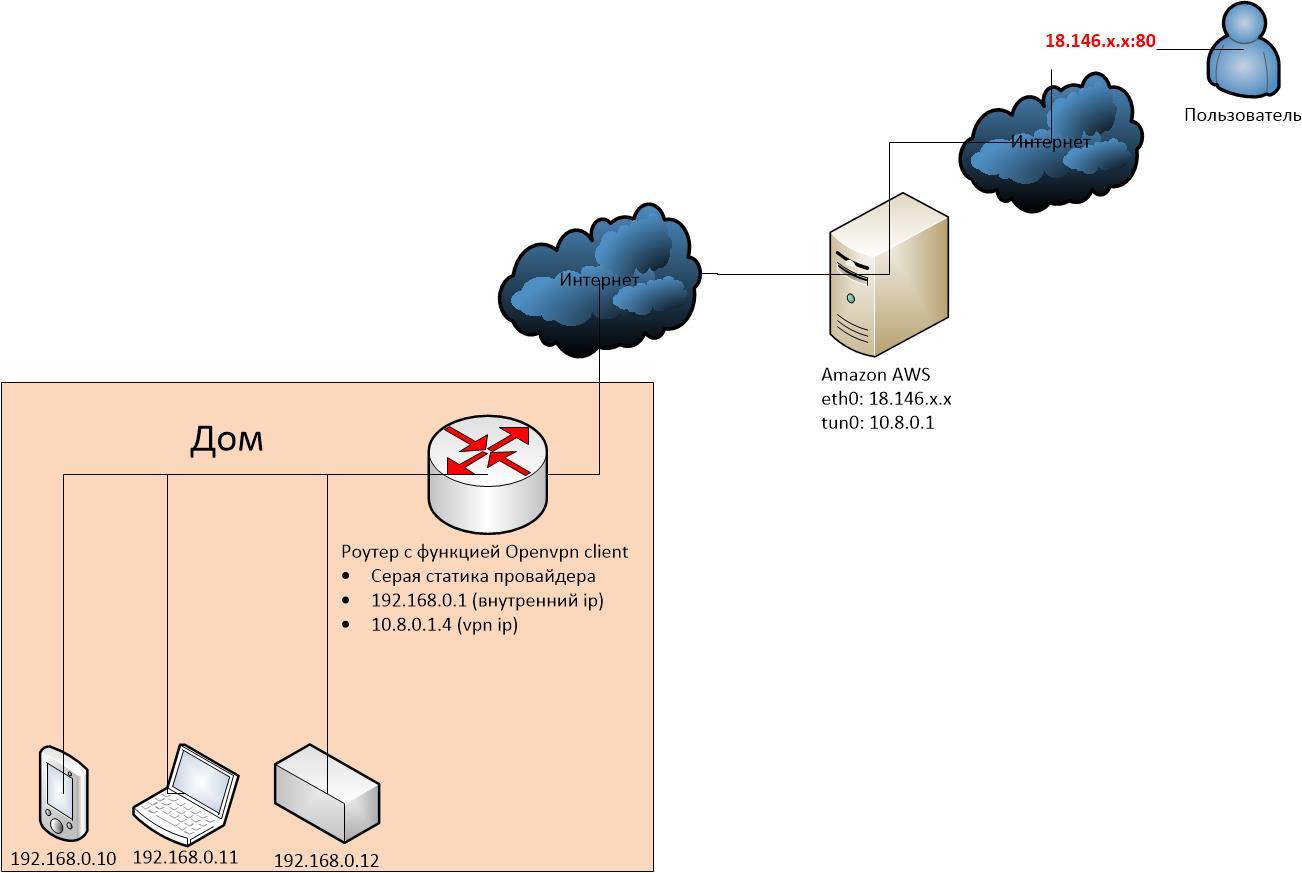
I'm trying to set up access to the home server from the outside, taking into account the gray static from the Internet provider.
Initial data (see the attached diagram under the spoiler):
etc/ufw/before.rules
*nat
:PREROUTING ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
-A PREROUTING -i eth0 -d 18.146.x.x -p tcp --dport 80 -j DNAT --to-destination 10.8.0.4:80
-A PREROUTING -i eth0 -d 18.146.x.x -p tcp --dport 443 -j DNAT --to-destination 10.8.0.4:443
-A POSTROUTING -s 10.8.0.0/8 -o eth0 -j MASQUERADE
COMMIT/etc/sysctl.conf
net.ipv4.ip_forward= 1Answer the question
In order to leave comments, you need to log in
And on the home router, in addition to redirecting FROM the tunnel, is the same NAT made INSIDE the tunnel?
And what's the point of doing two redirects (forwarding) when you can immediately register a direct route to the server behind the tunnel on AWS and not do any forwarding on your home router?
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question