Answer the question
In order to leave comments, you need to log in
How to determine the encryption method?
Good day!
There are two devices communicating via the CAN bus, device No. 1 wants to access the flash memory of device No. 2, for this a special request is sent and device No. 2 generates a message with a random 4-byte key, to which the device No. 1 sends the answer also in the form of a 4-byte key, changed in an unknown way. Device No. 2 on the response message understands that the answer is correct and gives access. Accordingly, if the answer is incorrect, then access is not opened. Of course the coding algorithm is known to both devices. The question is - how to determine the encoding algorithm, if there is both an initial key and a final answer? Moreover, we managed to get several of these combinations and you can get as many more as you like. Here they are (in HEX):
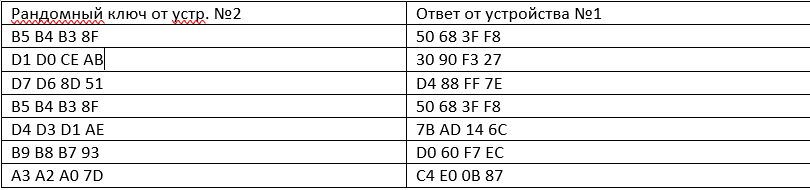
Answer the question
In order to leave comments, you need to log in
What you are asking is called cryptanalysis. If I understand the task correctly, you are working with a "black box"; the encoding algorithm itself is known to devices, but unknown to you.
Probably some experienced cryptanalyst could help you with a very slim chance of success.
Or rather, the chances of success depend on the encryption algorithm, which is initially designed by smart people specifically to make this what you are doing as difficult as possible.
For example, check if the same incoming message is encoded differently or the same each time. If it is different, then the algorithm uses some unknown parameter (initialization vector), and it can be anything (for example, an internal lookup table). And if the devices can use any other data, then the task becomes more complicated many times over. Here it will be necessary to already understand where these initialization vectors can be taken from in principle.
And somehow brute-forcing 4 bytes is a trifling task, but, of course, you won’t find an algorithm like that. And another question - every time the key is different or the same?
Well, the best thing is to unearth the documentation for these two devices, or, well, open up and check the electronics themselves. If there are chips with memory, then solder it - read the memory, smoke datasheets, see what happens. If this is not a nuclear weapon control panel, then I don’t think that they bothered too much with protection. It is quite possible to try to intercept the signal to open access and make a bypass.
PS Are you sure that this is encryption? Maybe some kind of control signal?
4 bytes - painfully primitive protection.
managed to get a few of these combinations and you can get as many more as you like.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question