Answer the question
In order to leave comments, you need to log in
How to connect via IPSec?
Good day tosterchane
upd as an answer, the current manual / link to the example is accepted, and not notations, because I didn’t use IPSec before and I didn’t manage to solve the problem on my own even after several
days of
googling . so that instead of the number was the name of the site. There are two ways to do this: through a personal account (it does not suit you) or through the SMPP protocol (you need it that way). To do this, you need to create a tunnel through IPSec to
195.19.216.1 . Problem:
I can’t create this tunnel: I tried both in Win10 with built-in methods and not built-in, and on Debian through strongswan, there is no connection and that’s it (
and this is half the trouble, Rostelecom’s technical support did not provide any manual, but responded to a request for help:
we do not train clients to use a personal computer
[09:36, 31.8.2018] Our_company: hello
[09:36, 31.8.2018] Our_company: Didn't they send you the page where to enter?
[09:42, 31.8.2018] Stanislav Rostelecom/Beeline: Hello.
*******, I’ll clarify now
[09:42, 31.8.2018] Stanislav Rostelecom/Beeline: * but this is the data for joining (this is not a personal account)
[09:54, 31.8.2018] Stanislav Rostelecom/Beeline: B The questionnaire had an ip address for connection
[09:54, 31.8.2018] Stanislav Rostelecom/Beeline: Excel
[09:54, 31.8.2018] Our_firm: ok
[09:58, 31.8.2018] Stanislav Rostelecom/Beeline: You need our_firm set up your own A2p data connection.
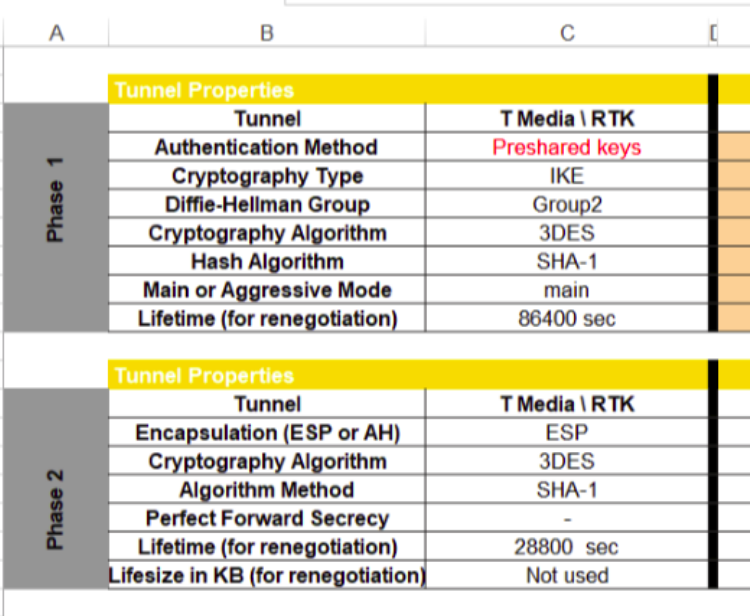
According to the IPSec file.
This is the Excel file
[09:58, 31.8.2018] Our_firm: accepted
[10:28, 8/31/2018] Stanislav Rostelecom/Beeline: Before trying to connect, a new client needs to raise the tunnel from its Gate to gate 195.19.216.1
Inside the tunnel, register your ip ACL --> 195.19.216.18
After that, make sure that the traffic is correctly routed to tunnel and execute the command telnet 195.19.216.18 27750.
The response of port 27750 means that everything is done correctly.
Answer the question
In order to leave comments, you need to log in
0. If you have a username and password, this either means that they have nothing to do with the IPSec tunnel, or you need to raise not just IPSec, but IPSec + L2TP or IPSec + PPPoE.
1. Find on the Internet a manual for setting up IPSec for your OS (the same Debian, for example), and try to do it. Try to find up-to-date instructions for the current distribution: all these Swans are always changing names from release to release from Opwnswan to Strongswan and back. Plus pluto, yes...
2. In case of errors - look at the console output, look at the logs in /var/log, /var/log/messages, /var/log/syslog, etc., google the error text.
3. Setting up IPSec - the process is long and almost always accompanied by errors in the settings that fall into the log. Various. You don't bring them to us.
4. There is no universal manual in the style of "copy to the terminal and press Enter".
5. As a memory, the process of setting up IPSec with all possible wiggles in different directions is remembered, presumably, by a few dozen people on the planet. On the toaster, you may not be able to shout them, so I advise you to take on this business yourself and do it by trial and error. Errors can be sent here - info will appear for discussion.
on my debian 9 openswan + l2tp is now configured like this:
# cat /etc/ipsec.conf
# /etc/ipsec.conf - Libreswan IPsec configuration file
#
# Manual: ipsec.conf.5
config setup
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/12,%v4:25.0.0.0/8,%v4:100.64.0.0/10,%v6:fd00::/8,%v6:fe80::/10
#logfile=/var/log/pluto.log
#plutodebug=all
include /etc/ipsec.d/*.conf# cat /etc/ipsec.secrets
%any: PSK "HERE_IS_MY_PRESHARED_KEY"# cat /etc/ppp/xl2tpd-options
asyncmap 0
auth
crtscts
lock
hide-password
modem
lcp-echo-interval 30
lcp-echo-failure 4
noipx
require-mschap-v2
ms-dns 8.8.8.8
ms-dns 8.8.4.4# cat /etc/ppp/chap-secrets
HERE_IS_MY_LOGIN * HERE_IS_MY_PASSWORD *Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question