Answer the question
In order to leave comments, you need to log in
How to connect to home remote desktop from corporate network?
Good time!
I work in a large organization with a domain corporate network.
There is a desire to connect at work to the remote desktop of a home computer.
To do this, I connected a static ip, on the keenetic router I made forwarding from port 3389 to a computer in the local network where remote access was activated. Configured without VPN, AD, servers and other wisdom
From the external network, everything works (distributed to the laptop from the phone).
I can’t connect from work:
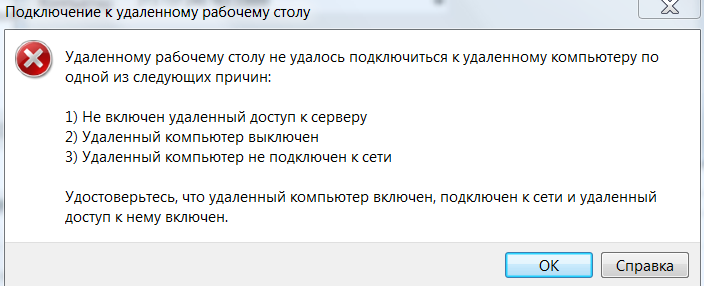
How can I find out what the problem is and what can be done to organize remote access?
Answer the question
In order to leave comments, you need to log in
I work in a large organization with a domain corporate network.
For home needs, a home solution that does not require port forwarding may be suitable - anydesk, teamviewer ...
As for rdp, you need to check the connectivity from any other place. So it's easier to make sure that the problem is not in setting up a home router / computer. And only then see if the same thing happens from the office.
Another moment. By exposing port 3389 to the outside (or with a different number, but rdp), you need to make sure that all the latest updates are installed on the PC + there are definitely no accounts with simple passwords. Because brute force will start immediately after opening the port.
1. Exposing port 3389 is a bad, very bad idea.
I'm not talking about hacking - but over time, the computer will simply be DDoSED by bots trying to hack it.
2. There are several VPN implementations on Kinetic - choose the one that:
a) will pass through the protection at your work.
b) you will be able to set up a connection on a working machine.
Everything is at your own peril and risk, of course - you are going to a clear violation of some internal regulations, official or not, and it is not clear what this can lead to.
Expose some standard port outside (for example, 443) and forward it on the router to the same 3389 computer.
3389 outgoing cuts your corp. firewall.
But better - VPN, at least in the L2TP release on the same home Zyxel. Well, yes, with a non-standard port, because. 1701 is also likely stabbed to death.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question