Answer the question
In order to leave comments, you need to log in
How to configure network routing with openvpn?
Friends, for the first time I am setting up a server, I ask for help from specialists. The main thing is that the server is up and running , I figured it out, but with the routing of the problem, I don’t understand much about it at all, a dark forest. I set up the server for three days, collecting information from dozens of sites, but that's it, my strength has run out.
Network diagram
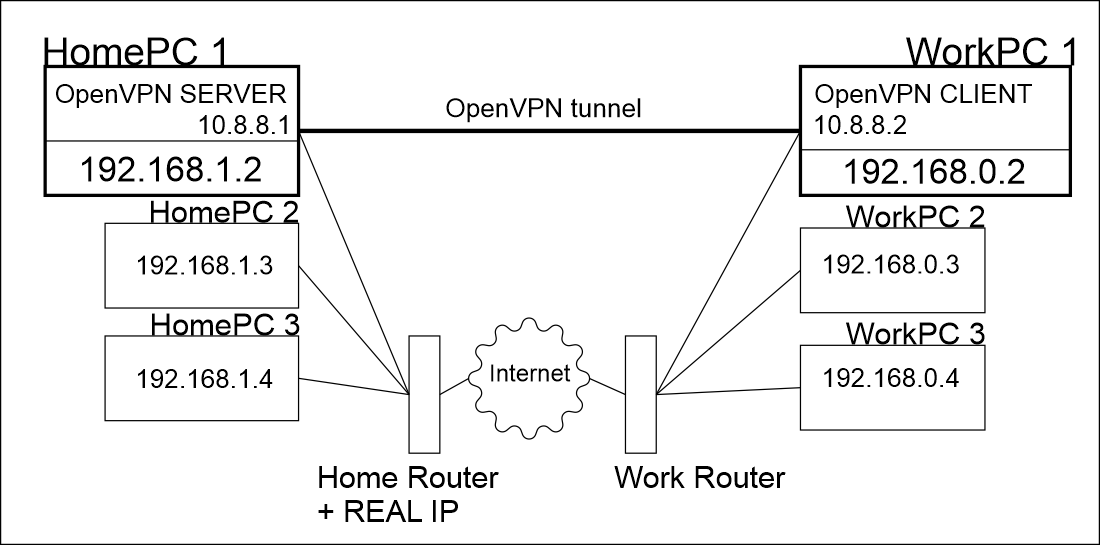
Answer the question
In order to leave comments, you need to log in
1. Do you have Windows on the openvpn server and on the client? What versions and there and there? If Home or Pro, then you need to enable routing: set the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\IPEnableRouter (REG_DWORD) registry value to 1 and reboot. Routing is normally already included on server Windows.
2. On the openvpn server, add the directive to the client config (located in the C:\\OpenVPN\\ccd directory):
iroute 192.168.1.0 255.255.255.0
This will add a route to the client's network on the openvpn server when the client connects (when disconnected, it will be deleted).
3. in the main openvpn server config add add directive:
This will add on the client a route to the network behind the server when connected.
push "route 192.168.0.0 255.255.255.0"
4. On the other computers behind the server there is an Internet router as the default gateway, so they send all packets destined for the client network to the router, and not to the opewnvpn server. You need to add a route to the client network to the routing table on each computer in the network (except for the openvpn server) with the command:
route -p add 192.168.1.0 mask 255.255.255.0 192.168.0.2route -p add 192.168.0.0 mask 255.255.255.0 192.168.1.2Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question