Answer the question
In order to leave comments, you need to log in
How to adjust a Cisco 1921 router to different subnets?
Greetings, Comrades!
Need help with a Cisco 1921 router, namely forwarding it to other Vlans. I can't think of a route.
In general, initially there was a simple network, i.e. one 0th subnet on unmanaged switches. Servers and users were in a common heap. If it was necessary, for example, to forward 1C to an external device, then I simply registered a cisco on the server as a gateway and simply made port forwarding on it. Also, a DMVPN network between offices for phones is configured on it (savings on intercity)
Here is its config:
dbt_vlg#sh run
Building configuration...
Current configuration : 5404 bytes
!
version 15.1
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
service internal
no service dhcp
!
hostname dbt_vlg
!
boot-start-marker
boot-end-marker
!
!
enable password 7 ************************
!
aaa new-model
!
!
aaa authentication login default local
aaa authorization exec default local
!
!
!
!
!
aaa session-id common
!
!
no ipv6 cef
ip source-route
ip cef
!
!
!
ip multicast-routing
!
!
ip domain name donbiotech.local
ip name-server 83.221.202.254
ip name-server 8.8.8.8
ip inspect WAAS flush-timeout 10
!
multilink bundle-name authenticated
!
crypto pki token default removal timeout 0
!
username francyz privilege 15 secret 5 ***********************
!
redundancy
!
!
ip ssh version 1
!
!
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key dbtkey address 0.0.0.0 0.0.0.0
!
!
crypto ipsec transform-set dmvpn_ts esp-3des esp-md5-hmac
mode transport
!
crypto ipsec profile dmvpn_profile
set transform-set dmvpn_ts
!
!
interface Tunnel1
description DMVPN
ip address 10.0.0.1 255.255.255.224
no ip redirects
ip mtu 1400
ip nhrp authentication nhrpkey
ip nhrp map multicast dynamic
ip nhrp network-id 2014
ip ospf authentication message-digest
ip ospf authentication-key 7 151D181C0215202131
ip ospf network broadcast
ip ospf hello-interval 3
ip ospf priority 100
tunnel source GigabitEthernet0/1
tunnel mode gre multipoint
tunnel key 2014
tunnel protection ipsec profile dmvpn_profile
!
interface GigabitEthernet0/0
description LAN
ip address 192.168.0.1 255.255.255.0
ip nat inside
ip virtual-reassembly in
duplex auto
speed auto
!
interface GigabitEthernet0/1
description INTERNET
ip address <внешний адрес> 255.255.255.252
ip access-group LANNET-in in
ip nat outside
ip virtual-reassembly in
duplex auto
speed auto
no cdp enable
!
router ospf 10
router-id 1.1.1.1
auto-cost reference-bandwidth 1000
area 0 authentication message-digest
area 192.168.0.0 authentication message-digest
redistribute static subnets
passive-interface default
no passive-interface Tunnel1
network 10.0.0.0 0.0.0.31 area 0
network 192.168.0.0 0.0.0.255 area 192.168.0.0
!
ip forward-protocol nd
!
no ip http server
no ip http secure-server
!
ip nat inside source list internet_to_lan interface GigabitEthernet0/1 overload
ip nat inside source static tcp 192.168.0.2 3389 <внешний адрес> 51788 extendable
ip nat inside source static tcp 192.168.0.3 3389 <внешний адрес> extendable
ip route 0.0.0.0 0.0.0.0 <внешний шлюз провайдера>
!
ip access-list extended LANNET-in
permit icmp any any
permit tcp any any established
remark DNS
permit udp any host <внешний адрес> eq domain
permit tcp any host <внешний адрес> eq domain
permit udp any any
remark WEB
permit tcp any host <внешний адрес> eq www
permit tcp any host <внешний адрес> eq 443
remark AVP
permit tcp any host <внешний адрес> eq 13000
permit tcp any host <внешний адрес> eq 14000
permit udp any host <внешний адрес> eq 15000
remark RDP
permit tcp any host <внешний адрес> eq 51788
ip access-list extended internet_to_lan
permit ip 192.168.0.0 0.0.0.255 any
!
dialer-list 1 protocol ip permit
!
!
control-plane
!
!
line con 0
line aux 0
line vty 0
transport input all
line vty 1
exec-timeout 30 0
privilege level 15
transport input ssh
line vty 2 4
transport input all
!
scheduler allocate 20000 1000
endAruba-2930F-48G-01# sh run
Running configuration:
hostname "Aruba-2930F-48G-01"
module 1 type jl260a
time timezone 180
ip routing
ip route 0.0.0.0 0.0.0.0 192.168.1.1
snmp-server community "public" unrestricted
vlan 1
name "DEFAULT_VLAN"
no untagged 11-32,47-48
untagged 1-10,33-46,49-52
no ip address
exit
vlan 99
name "Management"
untagged 47-48
tagged 50-52
ip address 192.168.99.250 255.255.255.0
exit
vlan 100
name "Active"
untagged 1-10
tagged 50-52
ip address 192.168.0.250 255.255.255.0
ip helper-address 192.168.1.2
exit
vlan 101
name "Servers"
untagged 11-20
tagged 50-52
ip address 192.168.1.250 255.255.255.0
exit
vlan 102
name "Users"
tagged 50-52
ip address 192.168.2.250 255.255.255.0
ip helper-address 192.168.1.2
exit
vlan 103
name "Printers"
tagged 50-52
ip address 192.168.3.250 255.255.255.0
ip helper-address 192.168.1.2
exit
management-vlan 99
no tftp server
no autorun
no dhcp config-file-update
no dhcp image-file-update
device-profile name "default-ap-profile"
cos 0
exit
activate provision disable
password manager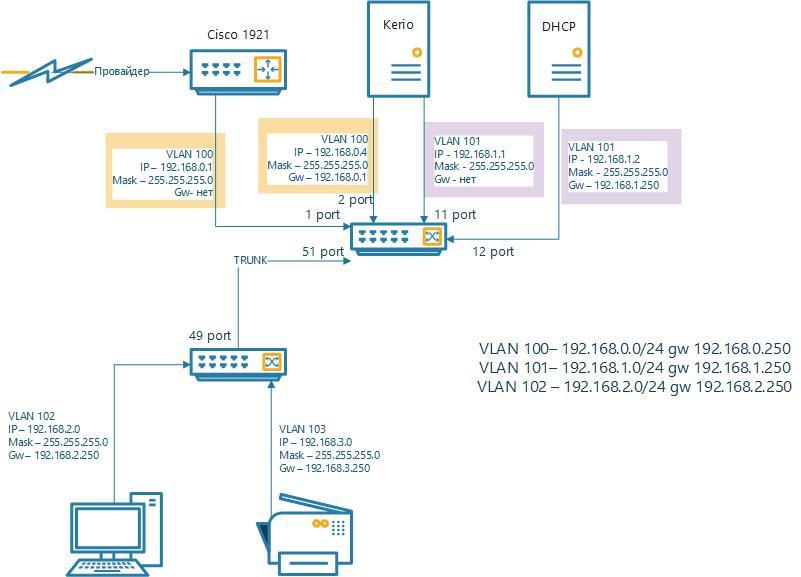
Answer the question
In order to leave comments, you need to log in
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question