Answer the question
In order to leave comments, you need to log in
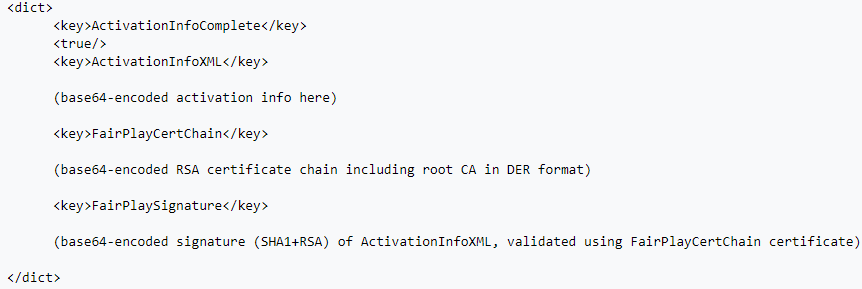
How is the signature generated?
Studying Wiki:
Here is a good example of a real request: link
If I understand correctly,
1) Activation data (BASe64)
2) Certificate (Base 64 RSA), in which I didn’t find much ..
3) Signature (which, according to WIKI, is generated from the data ( 1) and certificate (2)
Signature (3):
wBEUU8oNnOuvKqnB1n3PYm1MlqMC8LTWtnLPX0V1XIMyUs4XGNK7BVaYAqdIIJdyENs4
PNgjT17EJ8JSkIHfkRnsrTh7GGQT7EeXS8HTpksZn1yKoT7AjZgIni72DgofOIA0tsDu
hVqcP0BDtWQIBFub3NeHYT8FNACytWI/FNc=Answer the question
In order to leave comments, you need to log in
Will not work.
An electronic signature is just about such smart people. It ensures that the text it protects has not been modified. The signature is made with a personal certificate (key) that you do not have (if you have, you can simply regenerate the signature in the standard way). If there is no key, nothing will work.
There, on the other side, the subscriber will check the signature against the sender's common certificate - and if the text is changed, the signature will not match ...
A signature is a hash sum (sha1 in this case) of the data encrypted with a secret RSA key. By decrypting the signature with the public RSA key, you can get the hash of the data back and comparing it with the hash of the available data, you can verify the signature. The certificate contains the public RSA key. You cannot generate a valid signature without having a secret key, which is the essence of any asymmetric cryptography. If it were possible to get around this, then the entire security of the Internet would be covered with a copper basin, because asymmetric encryption is the basis of SSL.
Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question