Answer the question
In order to leave comments, you need to log in
Configure LAN access for OpenVPN clients on CentOS?
Good evening, please help me with this issue. Newbie in Linux.
OpenVPN is configured on centos 8, clients connect without problems. One of the clients is a Mikrotik router. Here you need to configure the micro PC to see the network of the OpenVPN server.
Network configuration
enp0s3: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.101.2 netmask 255.255.254.0 broadcast 172.25.101.255
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500
inet 192.168.10.1 netmask 255.255.255.255 destination 192.168.10.2port 55000
proto tcp
dev tun
ca /etc/openvpn/server/keys/ca.crt
cert /etc/openvpn/server/keys/srv-openvpn.crt
key /etc/openvpn/server/keys/srv-openvpn.key
dh /etc/openvpn/server/keys/dh.pem
#VPN сеть
server 192.168.10.0 255.255.255.0
#Чтобы локалка клиентов видила сервак VPN
push "route 172.25.101.0 255.255.254.0" \\Локал сеть сервера
push "route 192.172.10.0 255.255.255.0" \\Сеть за микротом
push "route 192.168.10.0 255.255.255.0"
#Маршруты к сети за VPN
#Чтобы сервер VPN видел локалку
route 192.172.10.0 255.255.255.0
#параметры клиентов
ifconfig-pool-persist /etc/openvpn/client/ipp.txt
#клиеты видят друг друга
client-to-client
client-config-dir /etc/openvpn/client
keepalive 10 120
#tls-проверка подлиности
#tls-server
#tls-auth /etc/openvpn/server/keys/ta.key 0 # This file is secret
#tls-timeout 15
tun-mtu 1500
tun-mtu-extra 32
mssfix 1450
#Кодировка
cipher AES-256-CBC
auth SHA1
#Не пересматривать сертификаты после перезагрузки
persist-key
persist-tun
status /var/log/openvpn/openvpn-status.log
log-append /var/log/openvpn/openvpn.log
verb 6
mute 20172.25.100.0 0.0.0.0 255.255.254.0 U 100 0 0 enp0s3
192.168.10.0 192.168.10.2 255.255.255.0 UG 0 0 0 tun0
192.168.10.2 0.0.0.0 255.255.255.255 UH 0 0 0 tun0
192.168.43.0 192.168.10.2 255.255.255.0 UG 0 0 0 tun0
192.172.10.0 192.168.10.2 255.255.255.0 UG 0 0 0 tun0Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 192.162.10.0/24 192.172.10.0/24
ACCEPT all -- 192.162.10.0/24 172.25.100.0/23
Chain OUTPUT (policy ACCEPT)
target prot opt source destinationiroute 192.172.10.1 255.255.255.0
ifconfig-push 192.168.10.13 192.168.10.14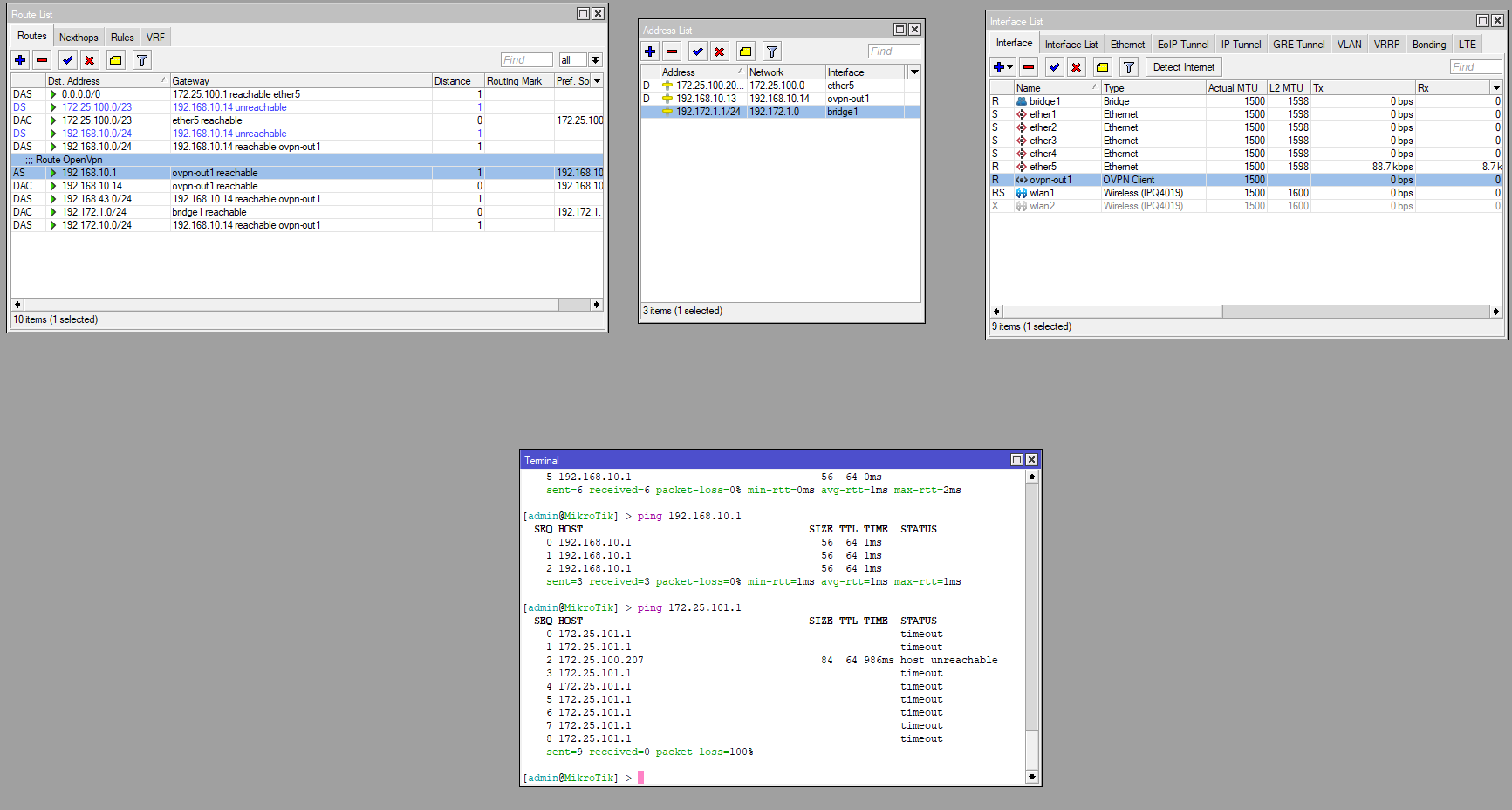
Answer the question
In order to leave comments, you need to log in
It's too much:
push "route 192.172.10.0 255.255.255.0" \\Сеть за микротом
push "route 192.168.10.0 255.255.255.0"route 192.172.10.0 255.255.255.0192.172.10.0/24 are the addresses that mikrotik distributes via dhcp for its users.
Вообще вам же, видимо, нужно что бы компы в сети за сервером ВПН имели доступ к компам за микротиком и наоборот?Сама ВПН у вас настроена нормально. Это видно из того, что вы успешно подключаетесь к ВПН серверу и видимо с микротика имеете доступ к компам в сети за сервером ВПН.Подозреваю, что ВПН сервер не является шлюзом по умолчанию для компов внутри сети и они не знают правильного маршрута до сети за микротиком.Didn't find what you were looking for?
Ask your questionAsk a Question
731 491 924 answers to any question